漏洞概要
关注数(24)
关注此漏洞
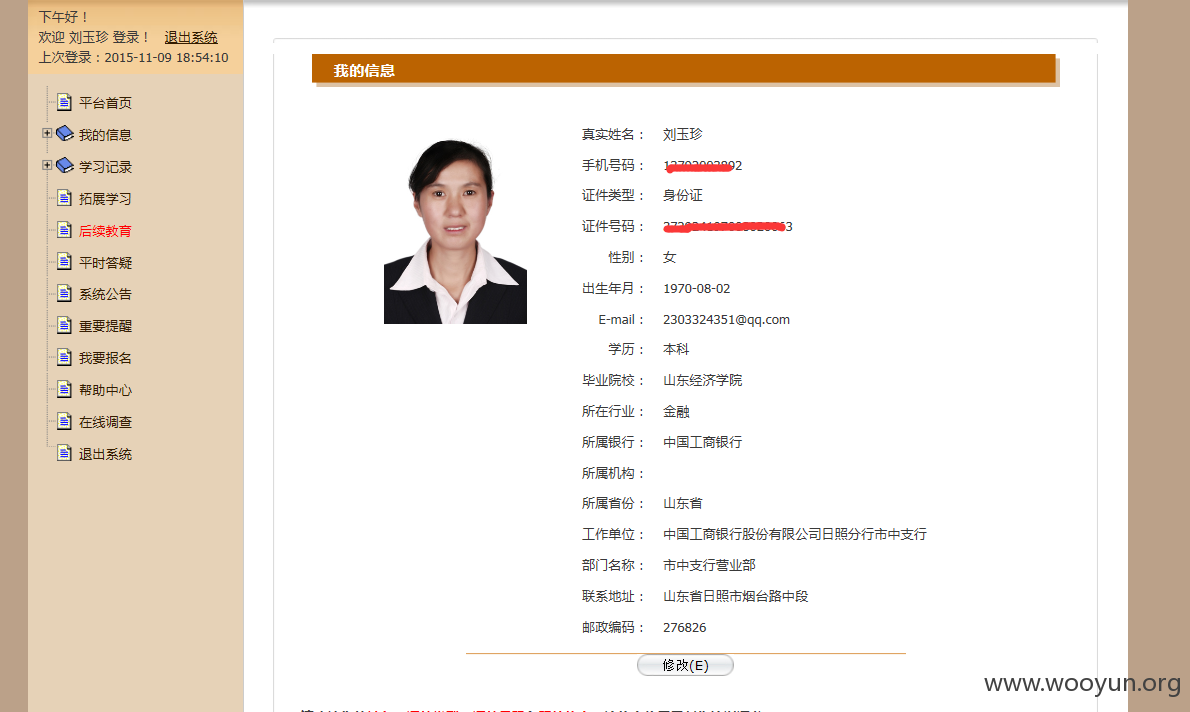
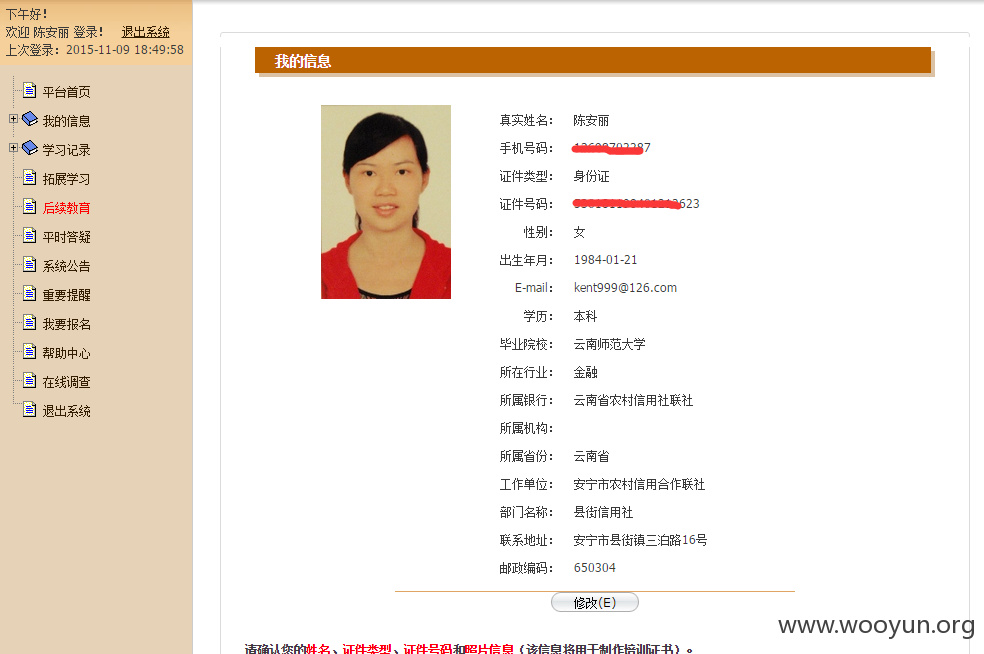
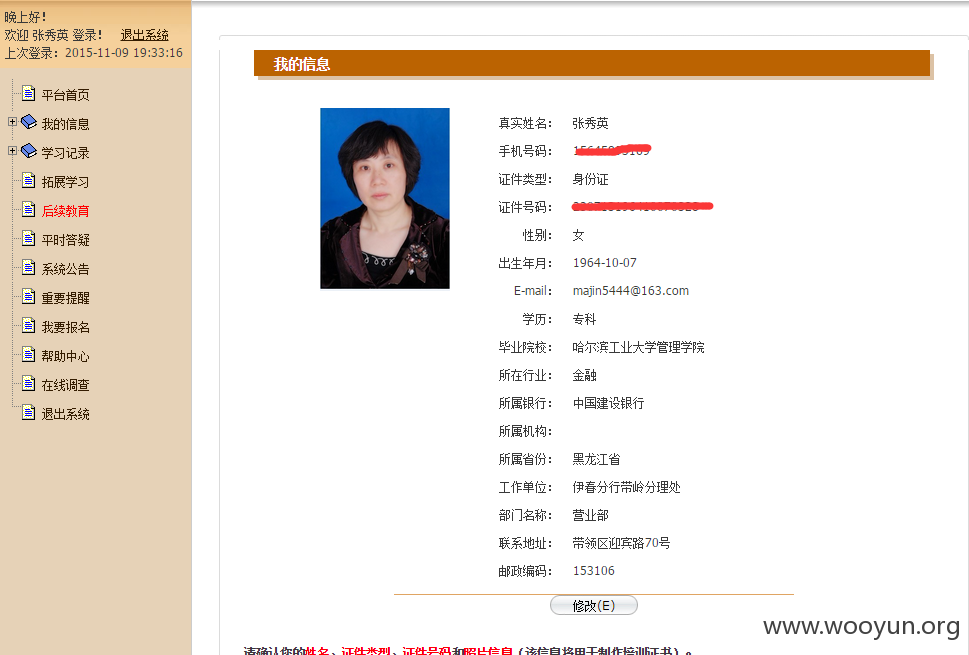
漏洞标题:银行业反洗钱系统某漏洞致银行职员信息泄露(照片/身份证/手机号/出生日期/工作单位/住址等等)
提交时间:2015-11-09 20:08
修复时间:2016-01-11 15:32
公开时间:2016-01-11 15:32
漏洞类型:敏感信息泄露
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
Tags标签:
无
漏洞详情
披露状态:
2015-11-09: 细节已通知厂商并且等待厂商处理中
2015-11-20: 厂商已经确认,细节仅向厂商公开
2015-11-30: 细节向核心白帽子及相关领域专家公开
2015-12-10: 细节向普通白帽子公开
2015-12-20: 细节向实习白帽子公开
2016-01-11: 细节向公众公开
简要描述:
详细说明:
http://**.**.**.**/FxqStudent/Login.aspx
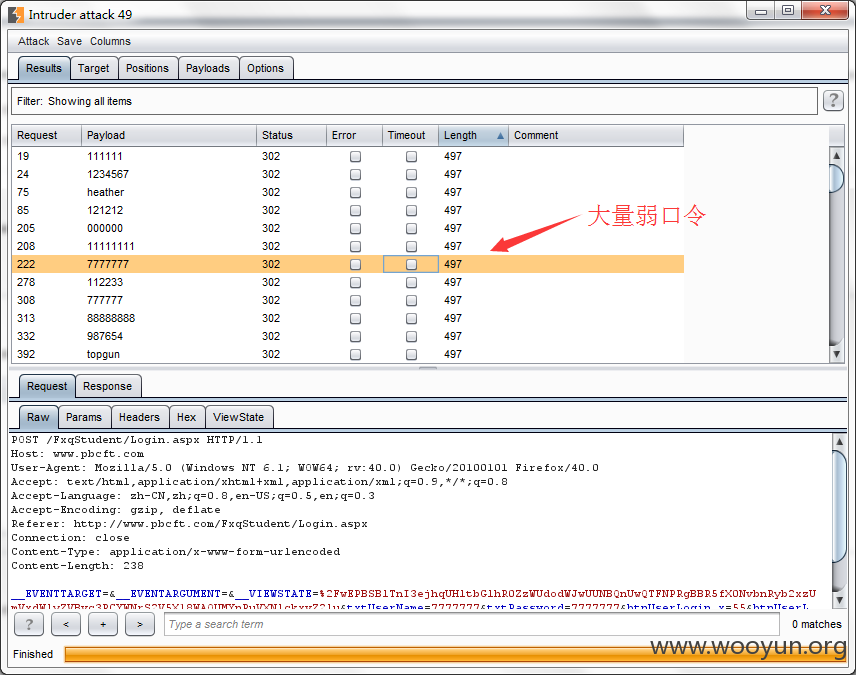
弱口令太多,只跑了我字典的不到1/5
漏洞证明:
修复方案:
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:12
确认时间:2015-11-20 14:35
厂商回复:
CNVD确认并复现所述情况,已经转由CNCERT向银行业信息化主管部门通报,由其后续协调网站管理单位处置。
最新状态:
暂无