91金融安卓APP客户端升级过程存在缺陷,,校验过程不严格,可被中间人攻击利用植入木马
点击检查更新后
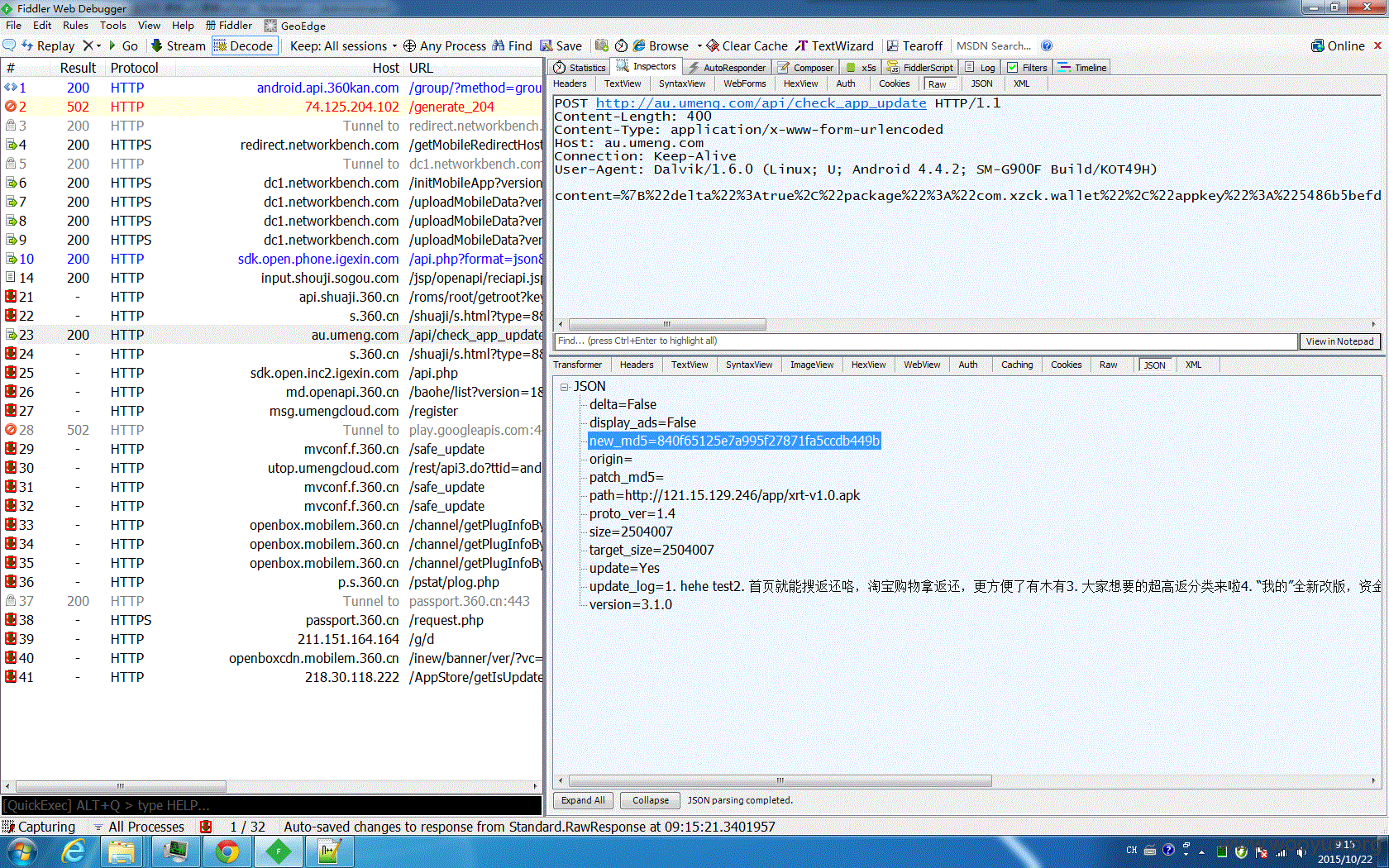
客户端发送如下数据包
使用fiddler拦截服务端返回数据,其中path可以随意指定为恶意木马,诱导用户安装
修改为
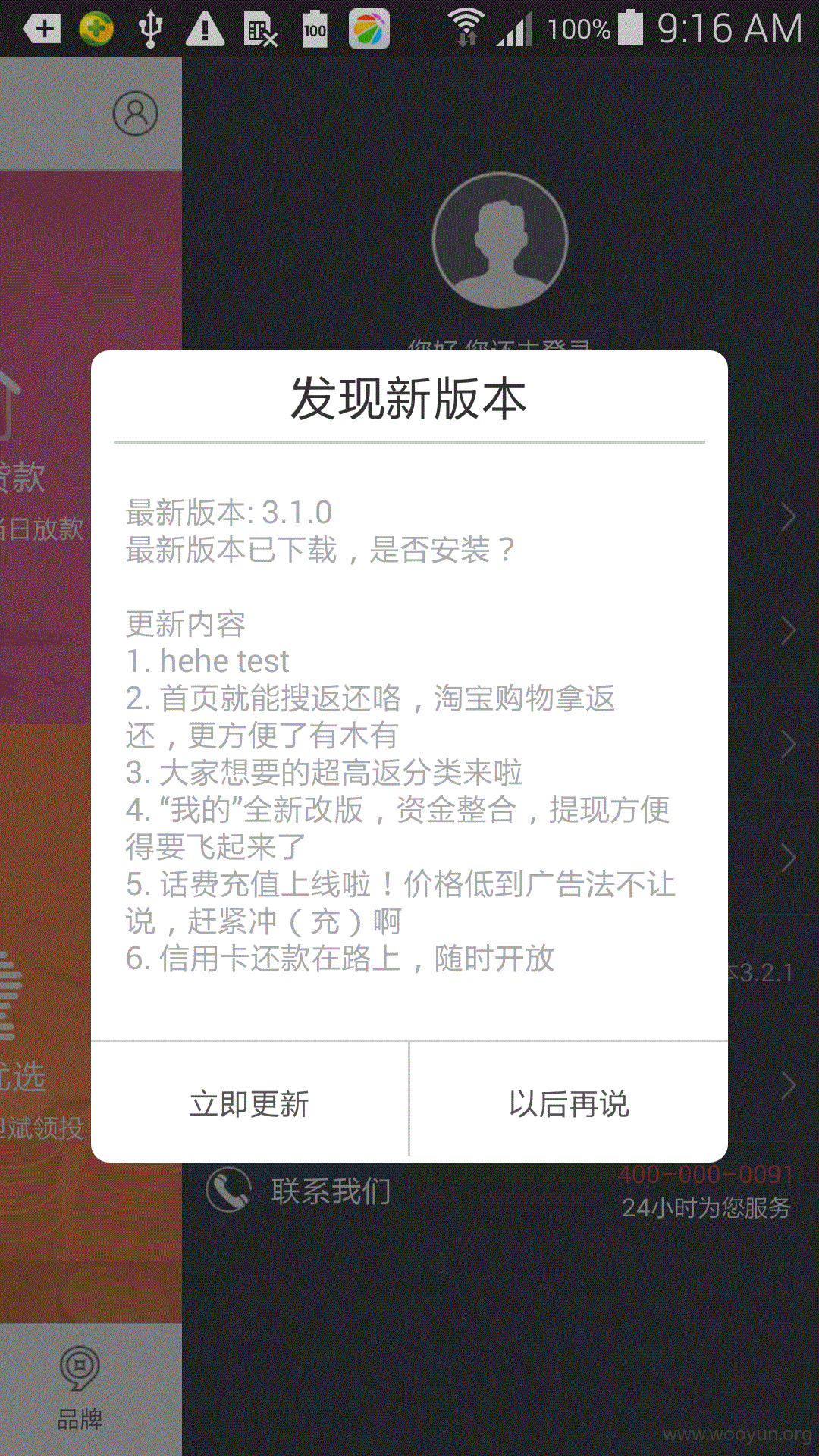
用户点击确定安装apk
91金融安卓APP客户端升级过程存在缺陷,,校验过程不严格,可被中间人攻击利用植入木马
点击检查更新后
客户端发送如下数据包
使用fiddler拦截服务端返回数据,其中path可以随意指定为恶意木马,诱导用户安装
修改为
抓包修改如下图
用户点击确定安装apk






