漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-074827
漏洞标题:中兴某业务弱口令(直接弹弹弹入内网)
相关厂商:中兴通讯股份有限公司
漏洞作者: Summer
提交时间:2014-09-03 08:57
修复时间:2014-10-18 08:58
公开时间:2014-10-18 08:58
漏洞类型:成功的入侵事件
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-09-03: 细节已通知厂商并且等待厂商处理中
2014-09-03: 厂商已经确认,细节仅向厂商公开
2014-09-13: 细节向核心白帽子及相关领域专家公开
2014-09-23: 细节向普通白帽子公开
2014-10-03: 细节向实习白帽子公开
2014-10-18: 细节向公众公开
简要描述:
弹弹弹弹弹 第五弹!
详细说明:
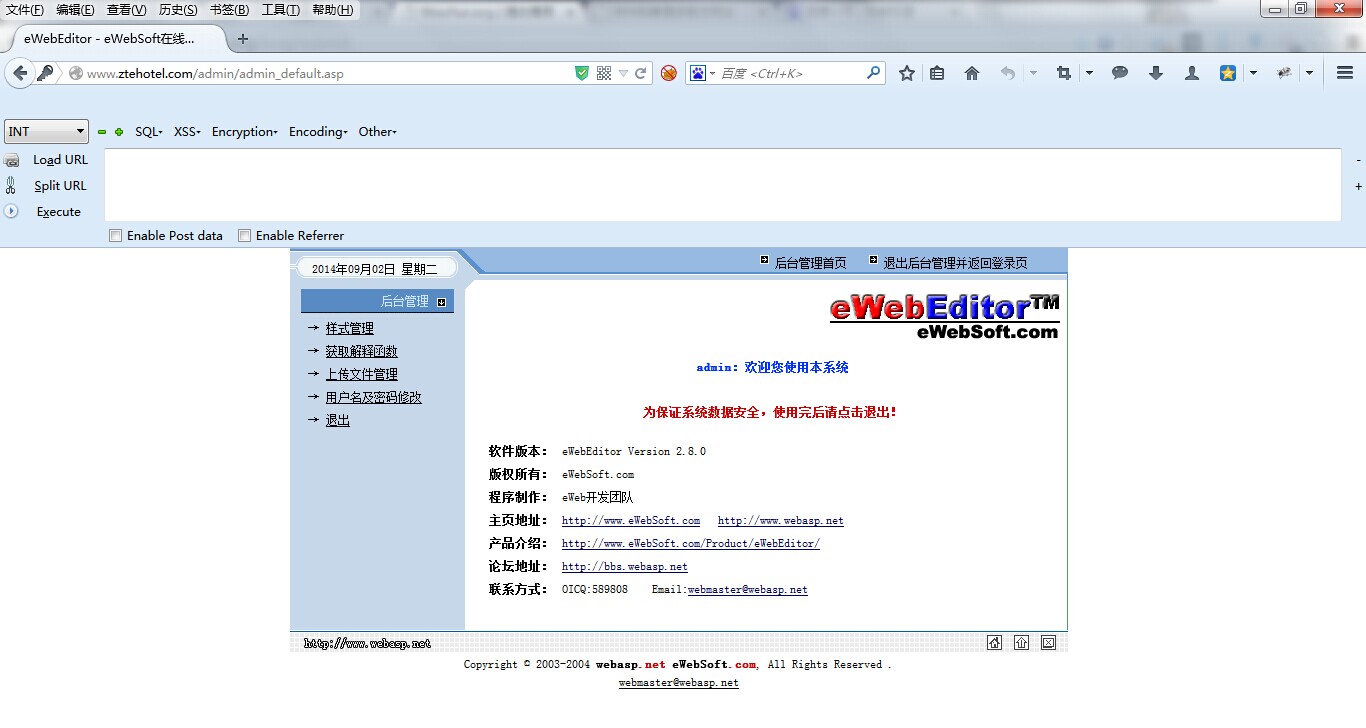
中兴和泰酒店
http://www.ztehotel.com/admin/index.asp
帐号:admin
密码:admin
http://210.21.236.173/images/dm.aspx 大马地址 到时候删除即可
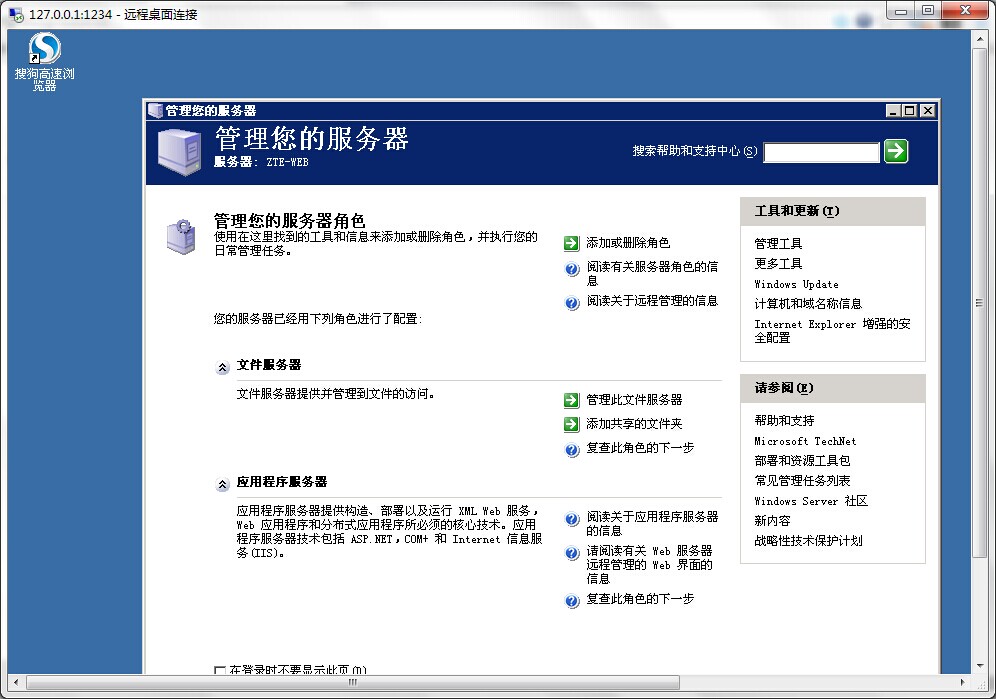
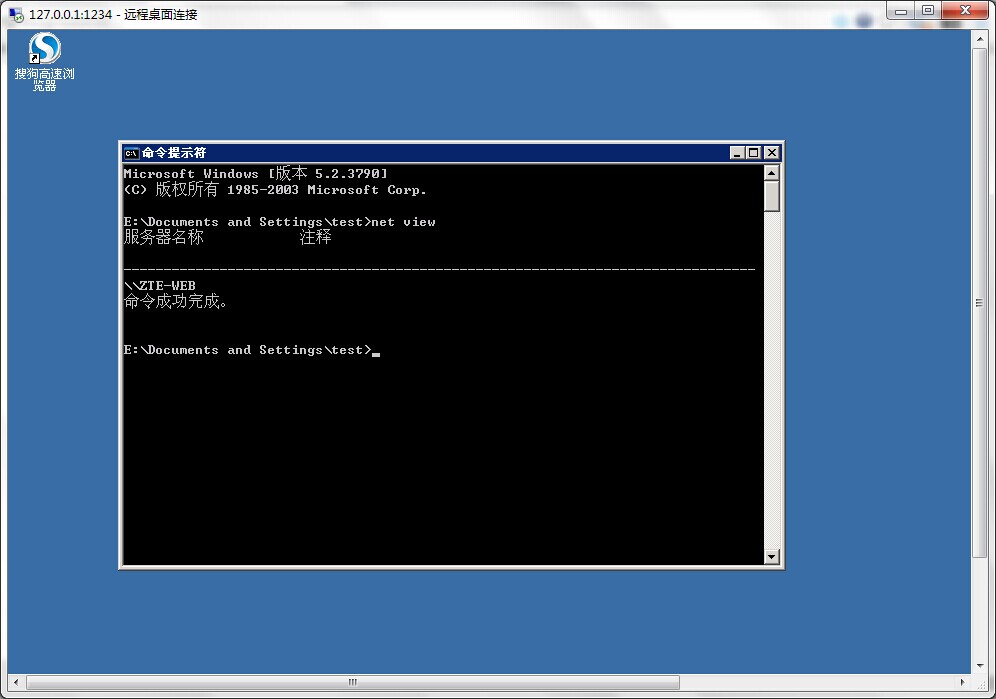
直接溢出,拿到system权限,添加用户之,探了下我这个段。
其他段我ping了下,很大。由于我的网络环境不能继续渗透下去了。
192.168.174.129 | | | |
192.168.174.131 |ZTE-789 |WORKGROUP |00.50.56.86.00.23 |
192.168.174.132 |ZTE-771 |WORKGROUP |00.50.56.86.00.26 |
192.168.174.133 |ZTE-733 |ITB2B |00.50.56.86.00.27 |
192.168.174.137 |TEST |WORKGROUP |34.40.B5.AA.6D.4C |
192.168.174.143 |ZTE-64148 |WORKGROUP |00.50.56.86.00.20 |
192.168.174.146 | | | |
192.168.174.151 |SRV-FTP147 |HWI |00.15.5D.50.0B.00 |
192.168.174.152 |SRV-FTPHOST |HWI |00.1C.C4.5C.9D.16 |
192.168.174.156 |ZTE-WEB |KL |00.26.B9.61.E3.5A |
192.168.174.163 |A10029047 |WORKGROUP |00.14.22.14.B5.EB |
192.168.174.162 |A10103566 |WORKGROUP |00.10.18.42.93.AC |
192.168.174.166 | | | |
192.168.174.167 | | | |
192.168.174.168 | | | |
192.168.174.177 |GPSSERVER |WORKGROUP |BC.34.73.18.FC.E3 |
192.168.174.181 |ZTE-6949DCDF538 |ZTE |00.1E.0B.DC.91.32 |
192.168.174.186 |EIP22 |WORKGROUP |00.1B.B9.DE.9D.F4 |
192.168.174.185 |EIP98 |WORKGROUP |00.1B.B9.DE.9F.F4 |
192.168.174.187 |ZJYDTEST1 |WORKGROUP |00.1A.A0.33.2E.84 |
192.168.174.189 |EIP25 |WORKGROUP |D4.85.64.4B.05.74 |
192.168.174.188 |SVCTAG-GDH562X |WORKGROUP |00.1A.A0.33.2E.A4 |
192.168.174.190 | | | |
192.168.176.131 |ZTE-Z7Y5OXM3FN4 |WORKGROUP |34.40.B5.9F.09.80 |
192.168.176.133 |WIN-BDT765JE0T4 |WORKGROUP |00.50.56.94.01.9E |
192.168.176.132 | | | |
192.168.176.136 |WIN-GEJ09VIE65B |WORKGROUP |98.F5.37.E0.CC.D8 |
192.168.176.137 |ZTE-624 |WORKGROUP |00.50.56.94.01.03 |
192.168.176.142 | | | |
192.168.176.138 |BIZTALK2013TEST |WORKGROUP |00.50.56.94.01.71 |
192.168.176.143 |WIN-176143 |WORKGROUP |00.50.56.94.01.99 |
192.168.176.134 |ZTEMEETING |WORKGROUP |34.40.B5.9C.B2.14 |
192.168.176.146 | | | |
192.168.176.149 |ICT149 |WORKGROUP |9E.0B.A1.B0.3C.C4 |
192.168.176.151 | | | |
192.168.176.152 |ICT51 |WORKGROUP |BE.73.6F.21.EF.75 |
192.168.176.153 | | | |
192.168.176.156 |WINDOWS-KVDZHQZ |WORKGROUP |AC.16.2D.8D.DC.30 |
192.168.176.157 | | | |
192.168.176.160 |ZTE-650 |WORKGROUP |00.50.56.94.00.D7 |
192.168.176.159 | | | |
192.168.176.158 | | | |
漏洞证明:
修复方案:
版权声明:转载请注明来源 Summer@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2014-09-03 14:16
厂商回复:
多谢summer,已经安排研发同事确认,谢谢!
最新状态:
暂无