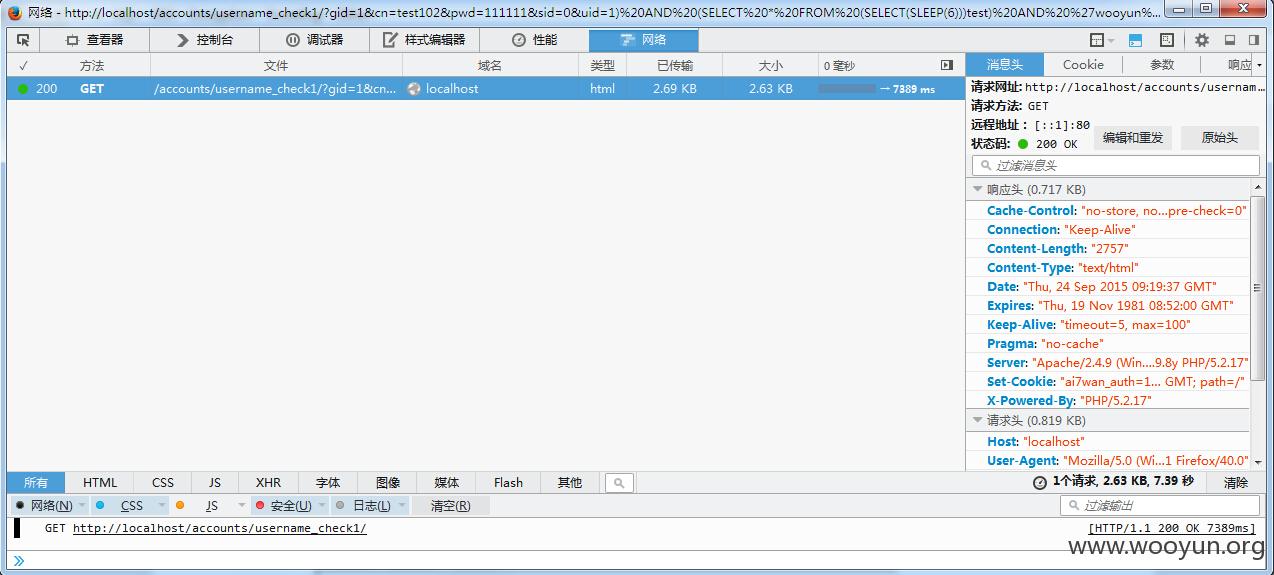
public function username_check1() {