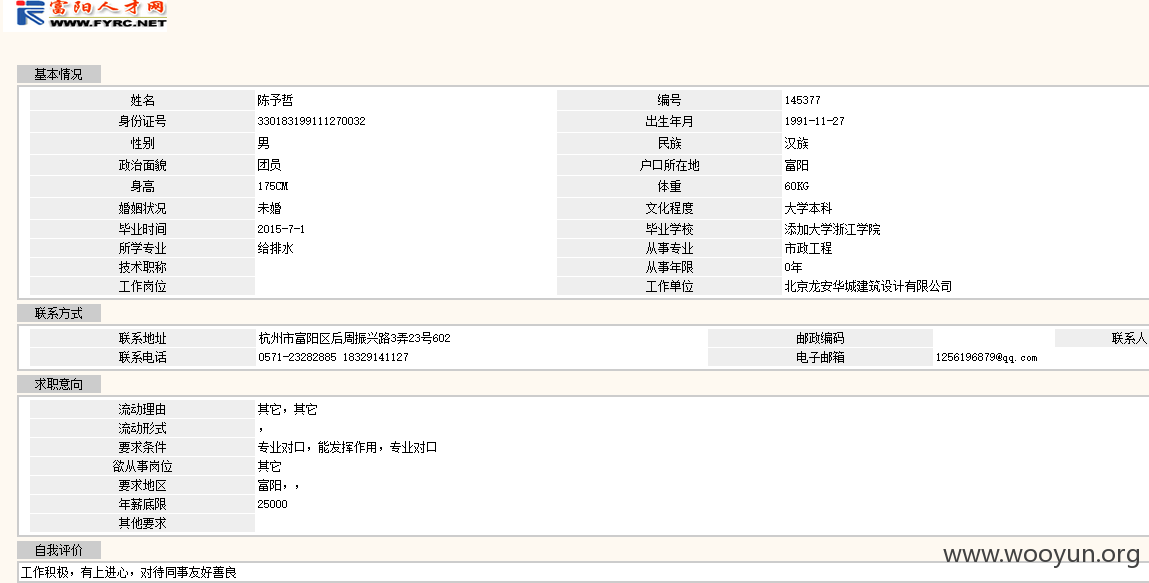
Database: newjxrc
+--------------+---------+
| Table | Entries |
+--------------+---------+
| dbo.RC_INFO | 1228864 |
| dbo.groupPos | 30611 |
| dbo.postptj | 899 |
| dbo.indutj | 70 |
| dbo.wkregtj | 32 |
| dbo.cd_educ | 9 |
+--------------+---------+
Database: newjxrc
+-------------+---------+
| Table | Entries |
+-------------+---------+
| dbo.RC_INFO | 1228864 |
+-------------+---------+
赠送3个注入点



