漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0141388
漏洞标题:诚信人才网注入(47万银行卡/家庭住址/身份证/电话号泄漏)
相关厂商:cncert国家互联网应急中心
漏洞作者: 路人甲
提交时间:2015-09-17 21:18
修复时间:2015-11-03 20:00
公开时间:2015-11-03 20:00
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-09-17: 细节已通知厂商并且等待厂商处理中
2015-09-19: cncert国家互联网应急中心暂未能联系到相关单位,细节仅向通报机构公开
2015-09-29: 细节向核心白帽子及相关领域专家公开
2015-10-09: 细节向普通白帽子公开
2015-10-19: 细节向实习白帽子公开
2015-11-03: 细节向公众公开
简要描述:
倘若下午四点就能见到你,我便在下午三点就能感到快乐
详细说明:
POST注入
Database: newcxrc
+---------------------------+---------+
| Table | Entries |
+---------------------------+---------+
| dbo.app_xczpview | 12815588 |
| dbo.send_resume | 1430232 |
| dbo.app_jobview | 822166 |
| dbo.jobview1 | 822166 |
| dbo.app_sendview | 767535 |
| dbo.sendResumeView | 746000 |
| dbo.app_defaultresumeview | 570072 |
| dbo.per_account | 506958 |
| dbo.per_resume | 471624 |
| dbo.zhuce | 471588 |
| dbo.per_basic | 435334 |
| dbo.app_userbasicinfo | 435325 |
| dbo.perBasic | 435325 |
| dbo.UserBasicInfo | 435325 |
| dbo.DefaultResumeView | 386825 |
| dbo.View_1 | 386825 |
| dbo.Asece | 291754 |
| dbo.Nsence | 280433 |
| dbo.safe | 277166 |
| dbo.resume_workExp | 223468 |
| dbo.jobView | 201441 |
| dbo.tjview | 201441 |
| **.**.**.**_job | 187842 |
| dbo.zj_job_colocale | 166290 |
| dbo.collection | 101223 |
| dbo.Resume_Edu | 99608 |
| **.**.**.**_basic | 92772 |
| dbo.inqiu | 87482 |
| dbo.admin_log | 87420 |
| dbo.article | 77874 |
| dbo.app_messageview | 70635 |
| dbo.notice | 70635 |
| dbo.zj_company | 63142 |
| dbo.NoticeView | 50606 |
| dbo.qjob | 44812 |
| dbo.Resume_Train | 44570 |
| dbo.adminLogView | 40804 |
| dbo.collectionPerView | 40458 |
| dbo.zj_colocale | 36997 |
| dbo.baobiao | 31023 |
| dbo.collectionJobView | 30743 |
| dbo.userRC | 30193 |
| dbo.inqiu2 | 17131 |
| dbo.per_photo | 17006 |
| **.**.**.**_tempReg | 15804 |
| dbo.zj_job | 7421 |
| dbo.per_missive | 6654 |
| dbo.text | 5367 |
| dbo.foxconn_account | 5107 |
| dbo.JobCenter | 3886 |
| dbo.Sence | 2519 |
| dbo.vote_result | 1149 |
| dbo.foxconn_emp | 752 |
| **.**.**.**_sideline | 727 |
| dbo.class | 725 |
| dbo.articleReview | 676 |
| dbo.sidelineView | 642 |
| dbo.lt_job | 427 |
| dbo.baobiao1 | 345 |
| dbo.leagueUser | 233 |
| dbo.foxconn_account2 | 205 |
| dbo.leagueJob | 179 |
| dbo.snce_account | 133 |
| **.**.**.**pany_photo | 79 |
| dbo.placard | 69 |
| dbo.vote_answer | 68 |
| dbo.jzpt | 62 |
| dbo.jp_account | 56 |
| dbo.Links | 52 |
| dbo.Advertise | 42 |
| dbo.articleClass | 40 |
| **.**.**.**pany_job | 34 |
| dbo.link | 25 |
| dbo.dtproperties | 14 |
| dbo.vote_Question | 12 |
| dbo.adminUser | 7 |
| dbo.tj_article | 7 |
| dbo.daxing | 6 |
| dbo.userGroup | 6 |
| dbo.leagueArticle | 5 |
| dbo.subscribe | 4 |
| dbo.vote_Subject | 3 |
| dbo.secnceview | 2 |
| dbo.senceyu | 2 |
| dbo.sysdiagrams | 2 |
| dbo.lt_per | 1 |
| dbo.paper_from | 1 |
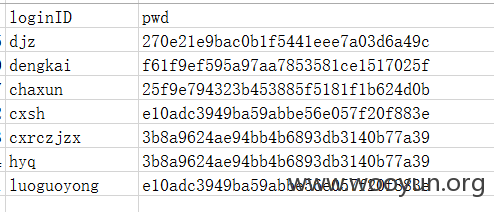
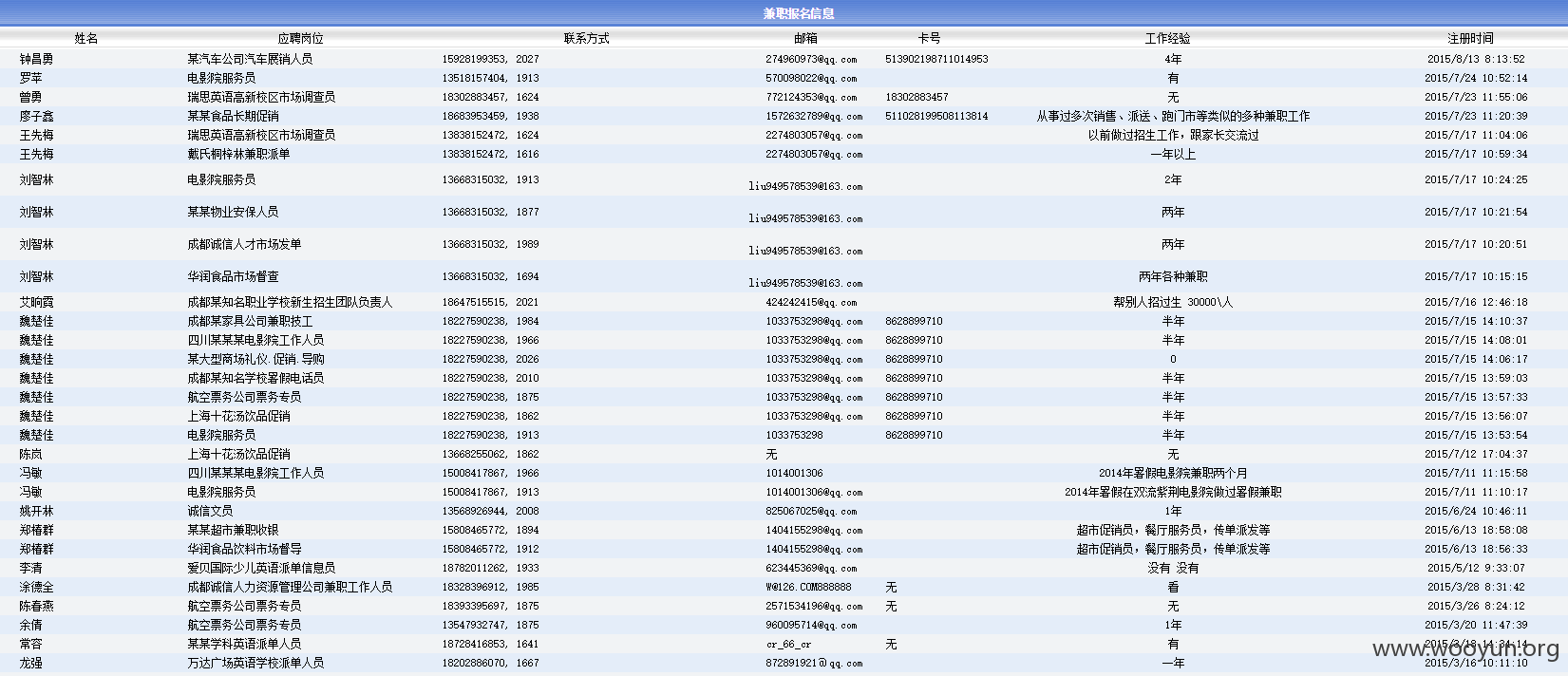
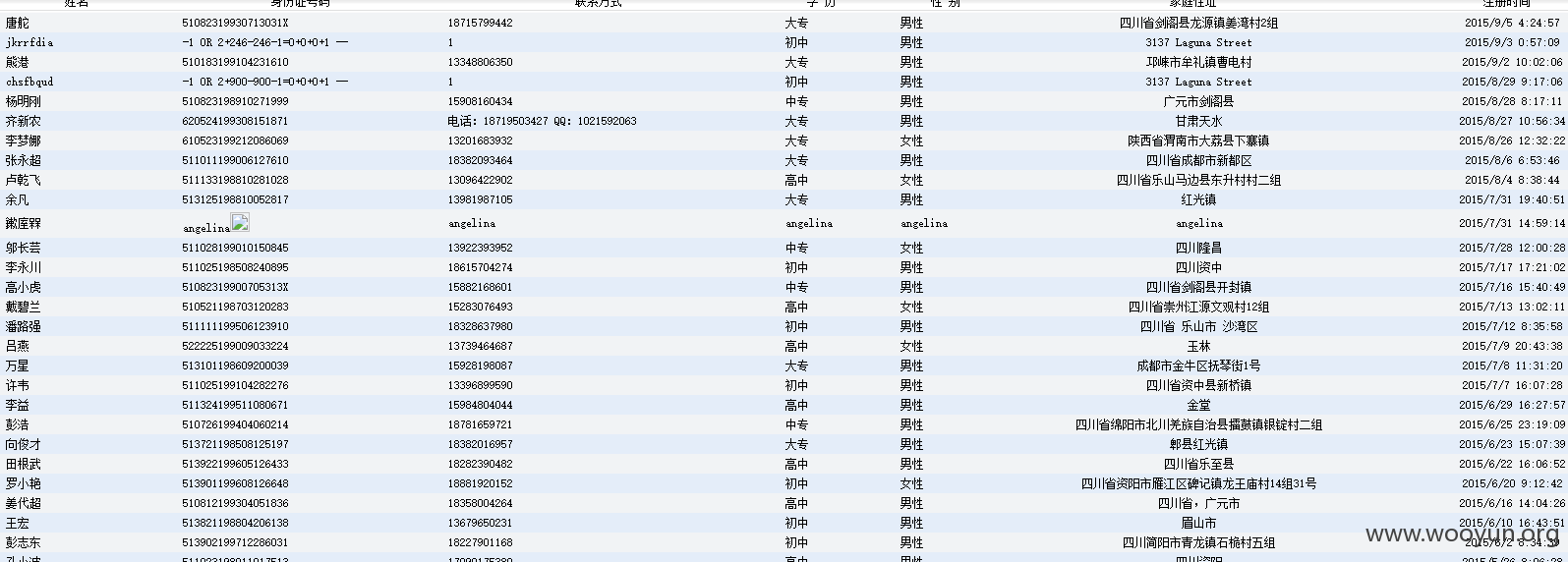
漏洞证明:
修复方案:
测试数据已删除,拒绝查水表,送快递等服务
过滤
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:13
确认时间:2015-09-19 19:58
厂商回复:
CNVD确认并复现所述情况,已由CNVD通过网站管理方公开联系渠道向其电话通报,由其后续提供解决方案并协调相关用户单位处置。
最新状态:
暂无