随便注册一个账号,然后修改账户信息。
利用短信验证钓鱼。
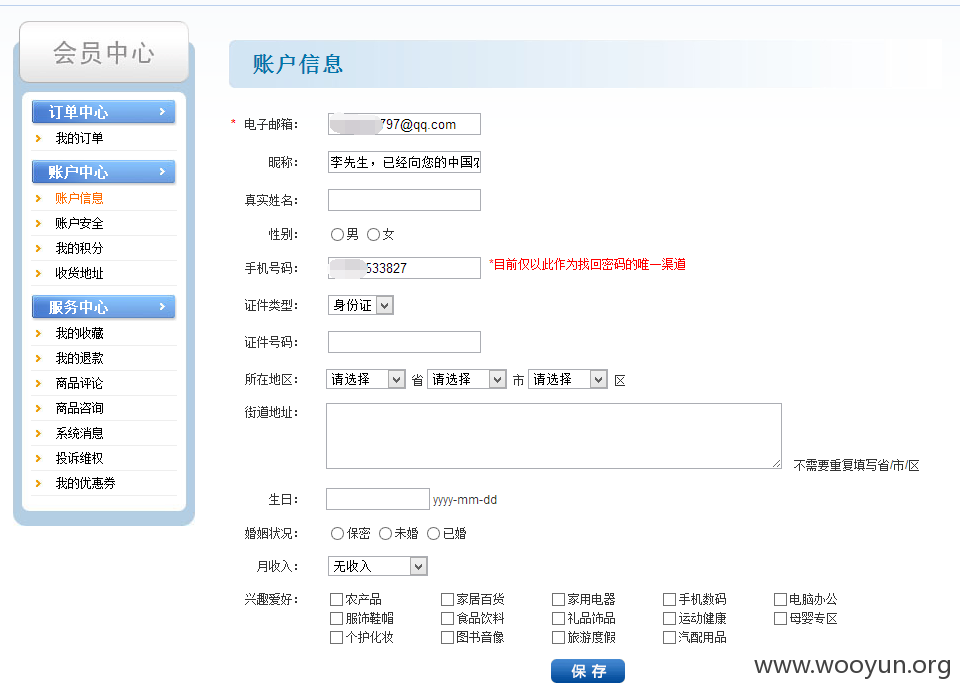
全部是用JS做过滤。
点击账户安全。
提交一下,得到短信:
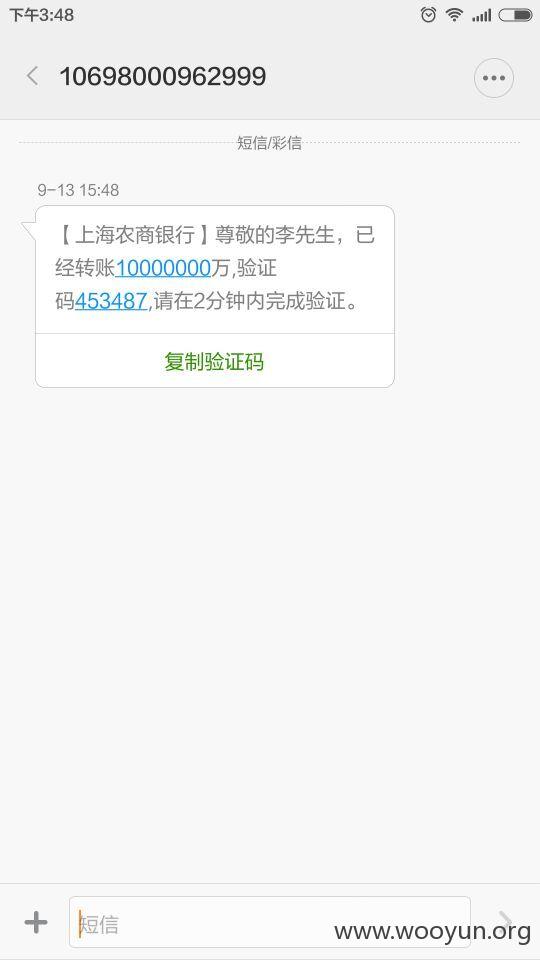
既然是JS过滤,完全可以修改内容,- -可想而知。逻辑漏洞还是有的。
还有一个难题我不会利用。
貌似存在POST SQL注入:
部分*代替了。
效果如下:
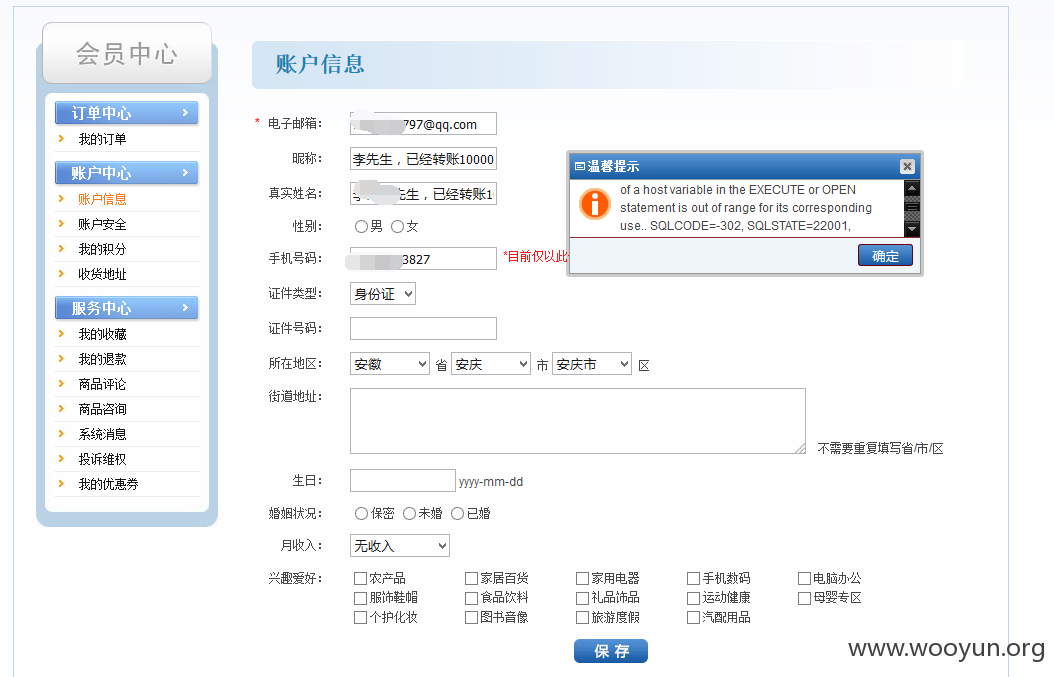
我也看不懂,大神继续。
随便注册一个账号,然后修改账户信息。
利用短信验证钓鱼。

全部是用JS做过滤。
点击账户安全。
提交一下,得到短信:

既然是JS过滤,完全可以修改内容,- -可想而知。逻辑漏洞还是有的。
还有一个难题我不会利用。
貌似存在POST SQL注入:
部分*代替了。
效果如下:

我也看不懂,大神继续。
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2015-09-17 16:00
厂商回复:
CNVD确认并复现所述情况,已经转由CNCERT向银行业信息化主管部门通报,由其后续协调网站管理单位处置. 同时已经转报给上海分中心,由其后续联系处置.
最新状态:
暂无





