漏洞概要
关注数(24)
关注此漏洞
漏洞标题:汇仁集团主站SQL注射(送肾宝么?)
提交时间:2015-08-31 09:36
修复时间:2015-10-17 10:26
公开时间:2015-10-17 10:26
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:10
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
Tags标签:
无
漏洞详情
披露状态:
2015-08-31: 细节已通知厂商并且等待厂商处理中
2015-09-02: cncert国家互联网应急中心暂未能联系到相关单位,细节仅向通报机构公开
2015-09-12: 细节向核心白帽子及相关领域专家公开
2015-09-22: 细节向普通白帽子公开
2015-10-02: 细节向实习白帽子公开
2015-10-17: 细节向公众公开
简要描述:
汇仁集团主站SQL注射(送肾宝么?)
详细说明:
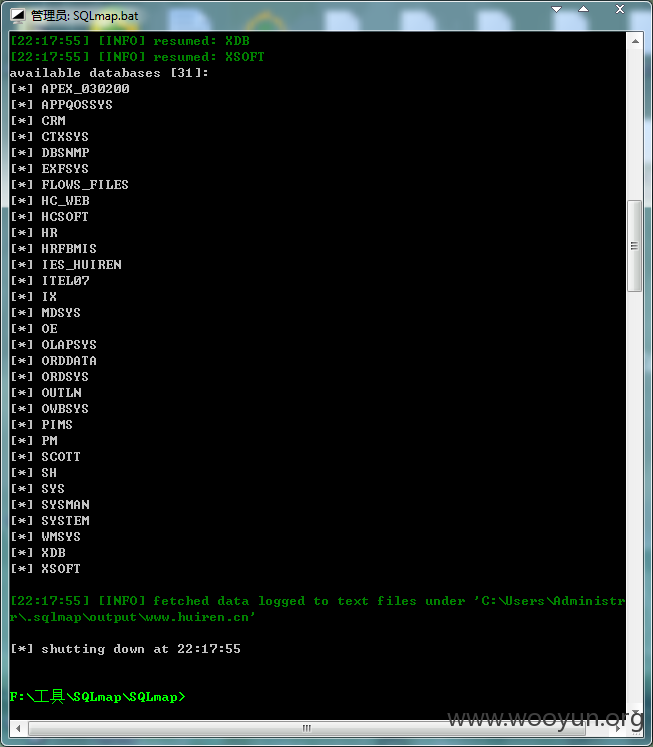
脱出数据,太多了。。。
不深入,你们懂
漏洞证明:
修复方案:
版权声明:转载请注明来源 冷白开。@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2015-09-02 10:25
厂商回复:
CNVD确认并复现所述情况,已经由CNVD通过网站公开联系方式(或以往建立的处置渠道)向网站管理单位(软件生产厂商)通报。
最新状态:
暂无



