http://m.tiexue.net/touch/Login.aspx这个接口是铁血网手机登陆接口,发现登陆处未做登陆限制
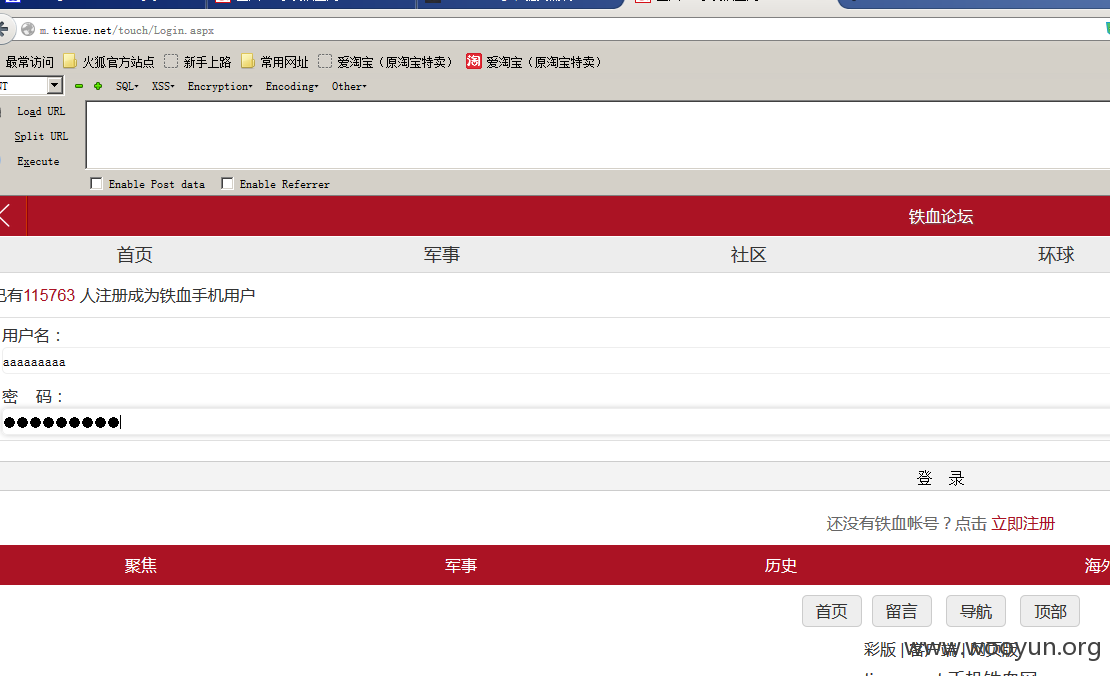
然后抓取post数据包如下:
发现用户名和密码都是明文传输的,然后去撞库试试,判断可以撞库成功
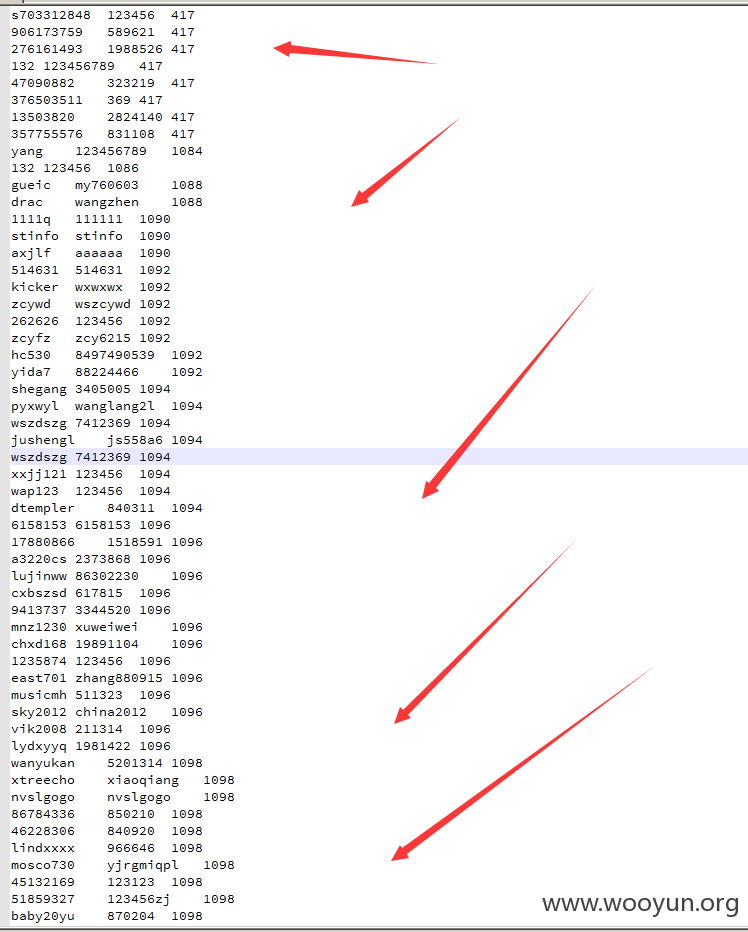
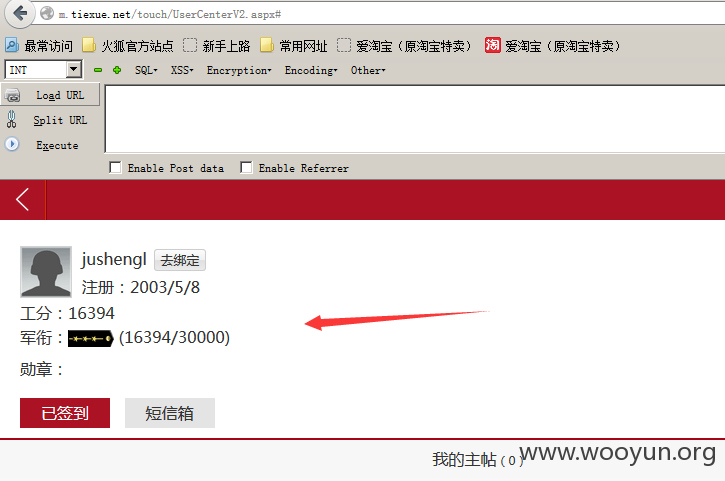
成功用户证明:
登陆成功咯~看看都是老用户,而且还有经验不少~
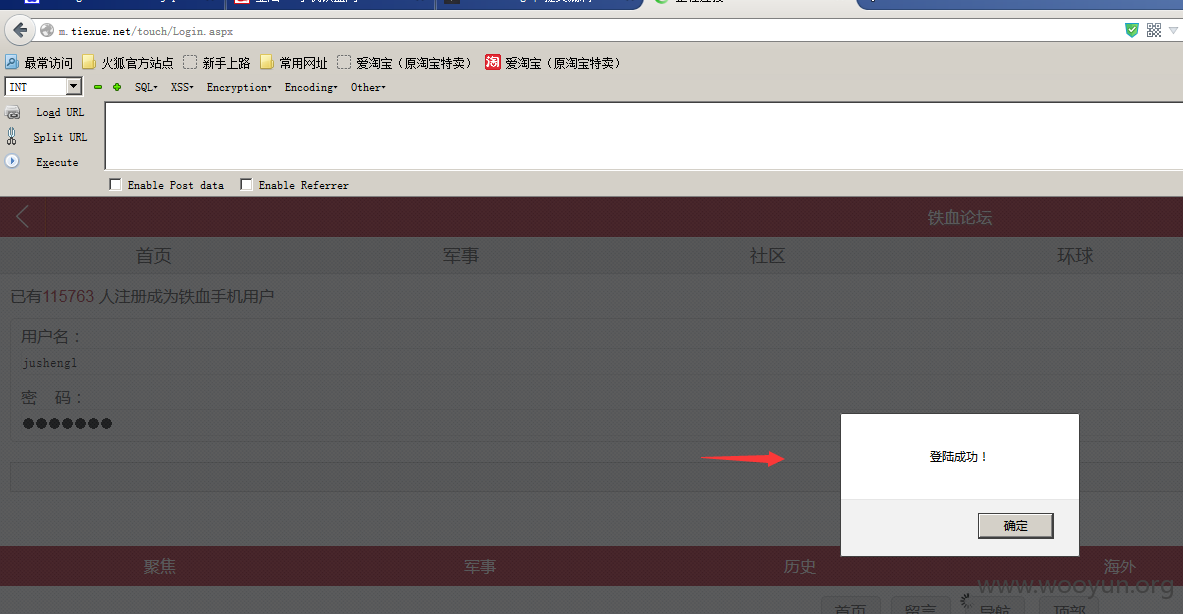
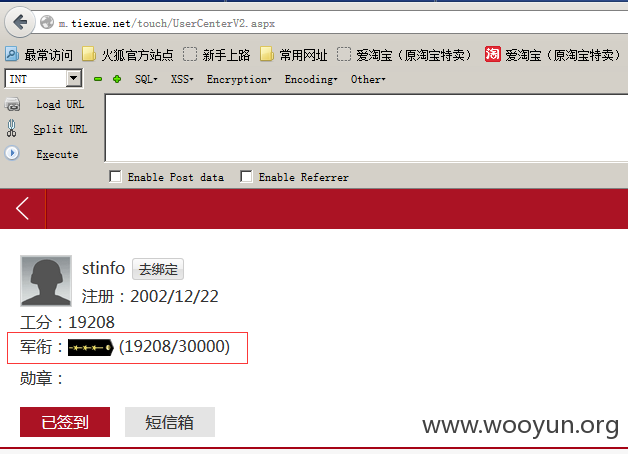
http://m.tiexue.net/touch/Login.aspx这个接口是铁血网手机登陆接口,发现登陆处未做登陆限制

然后抓取post数据包如下:
发现用户名和密码都是明文传输的,然后去撞库试试,判断可以撞库成功

成功用户证明:
登陆成功咯~看看都是老用户,而且还有经验不少~










