漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0132396
漏洞标题:社交网络安全之唱吧敏感信息泄露引发的安全问题(CDN推送平台\短信网关\密码找回接口均可控影响上亿用户)
相关厂商:Changba-inc
漏洞作者: HackBraid
提交时间:2015-08-07 15:49
修复时间:2015-09-24 12:00
公开时间:2015-09-24 12:00
漏洞类型:敏感信息泄露
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-08-07: 细节已通知厂商并且等待厂商处理中
2015-08-10: 厂商已经确认,细节仅向厂商公开
2015-08-20: 细节向核心白帽子及相关领域专家公开
2015-08-30: 细节向普通白帽子公开
2015-09-09: 细节向实习白帽子公开
2015-09-24: 细节向公众公开
简要描述:
泄露如下信息:
1.可以直接CDN推送音频或者直接通过CDN推送写webshell
2.唱吧官方的短信平台
3.找回密码的接口
4.各种数据库连接信息
http://tech.qq.com/a/20131011/014300.htm 据说用户数破亿了
详细说明:
#01 漏洞起源
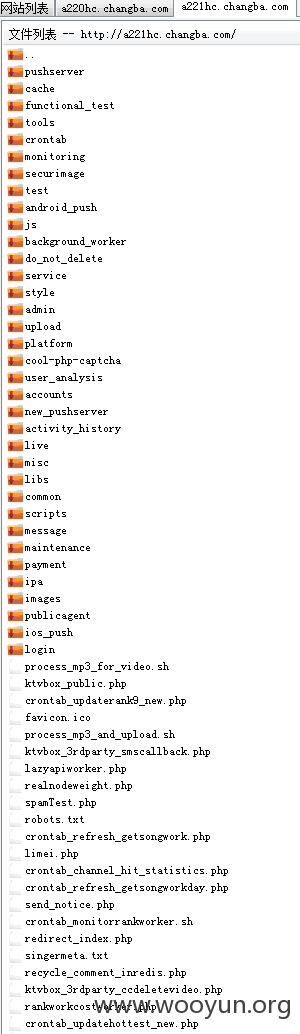
svn泄露:
http://a221hc.changba.com/.svn/entries
http://a219hc.changba.com/.svn/entries
http://a220hc.changba.com/.svn/entries
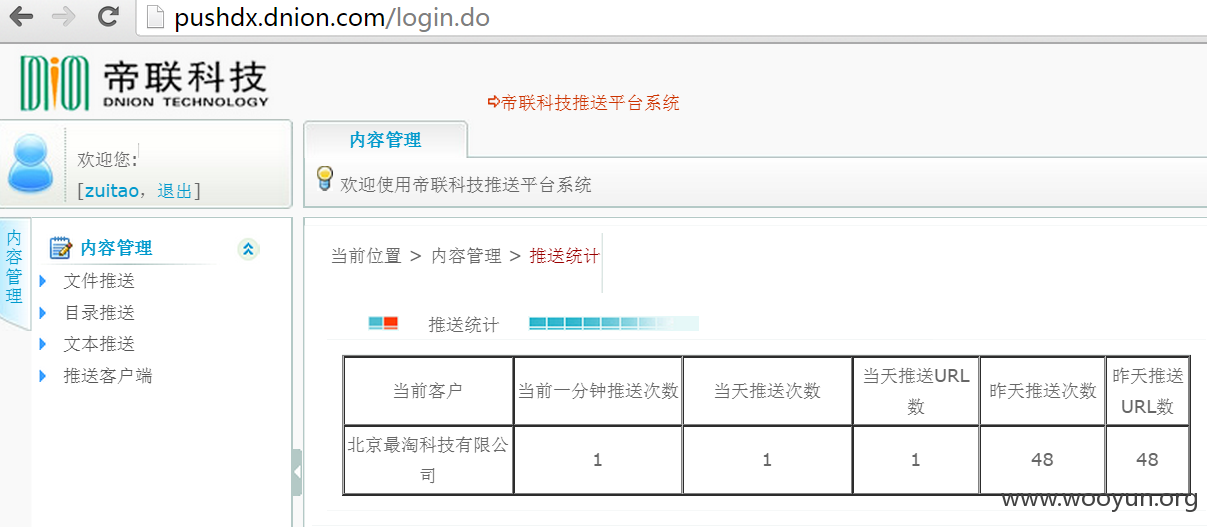
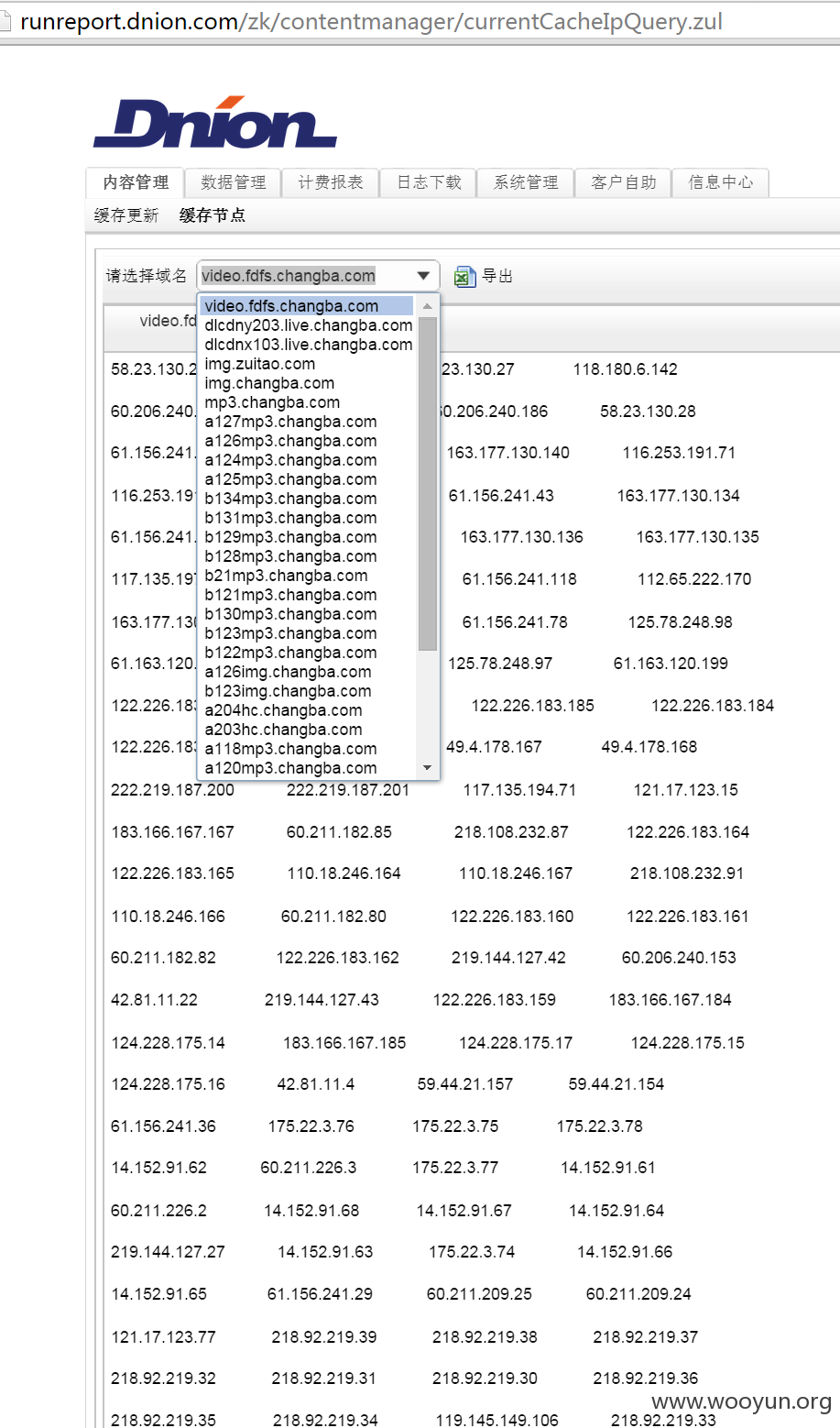
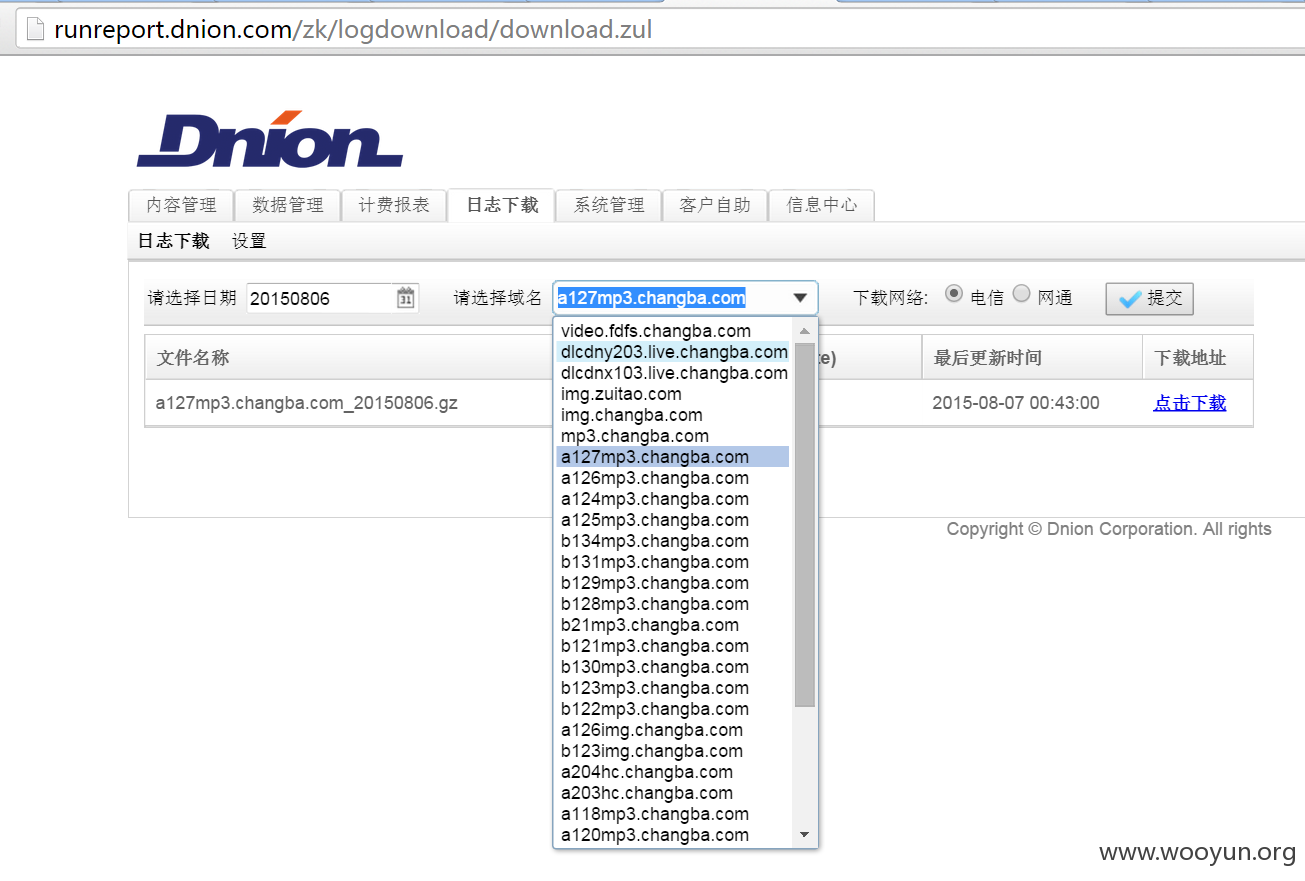
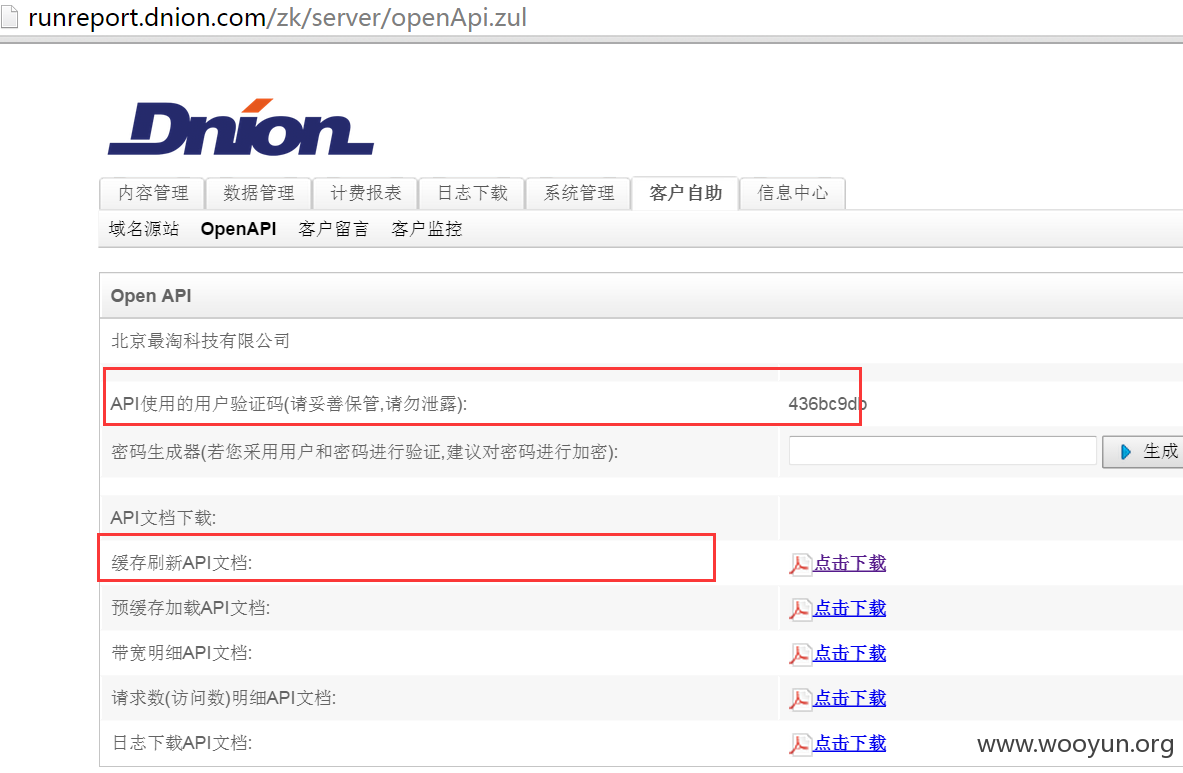
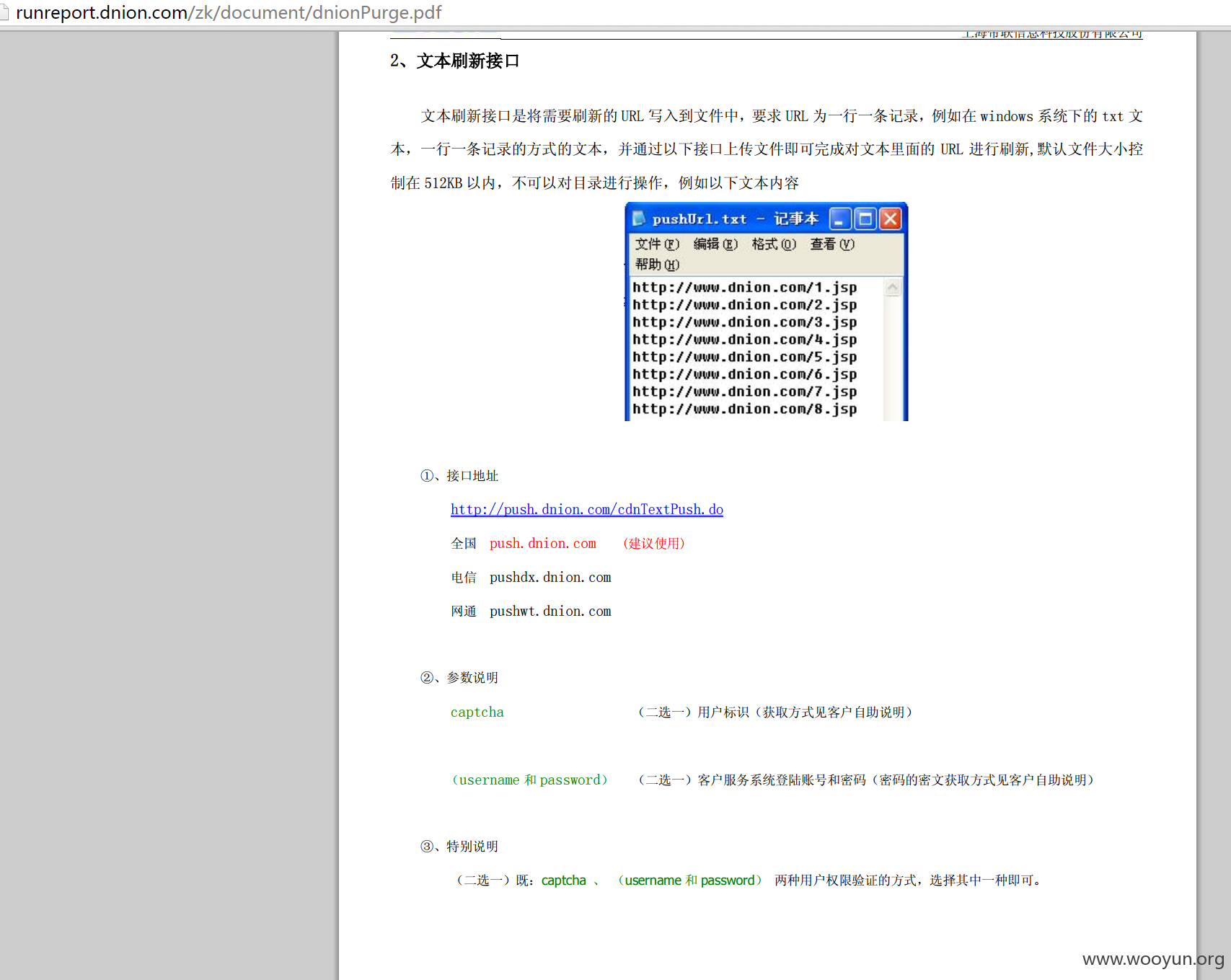
#02 CDN推送平台
源码泄露cdn推送平台的账户密码,使用的CDN商为帝联
http://pushdx.dnion.com/
这里可以推送shell.php吗?
还有客户端的推送
cdn所有节点信息
还有每天的日志
这里有api接口和使用说明,通过CDN推送的方式写shell应该是可行的
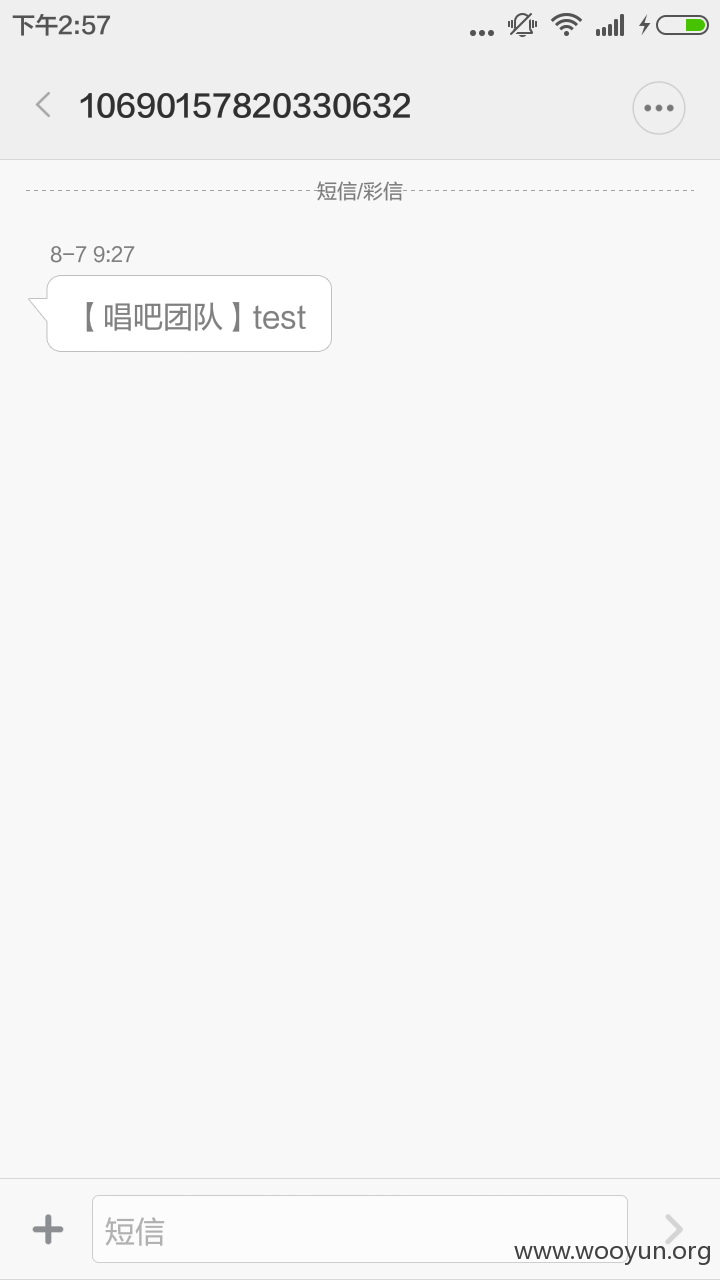
#03 唱吧短信网关
http://ws.montnets.com:9002/MWGate/wmgw.asmx/MongateCsSpSendSmsNew?userId=J00275&password=187523&pszMobis=15200009999&pszMsg=test&pszSubPort=1065712038002984"
即可收到发来的短信
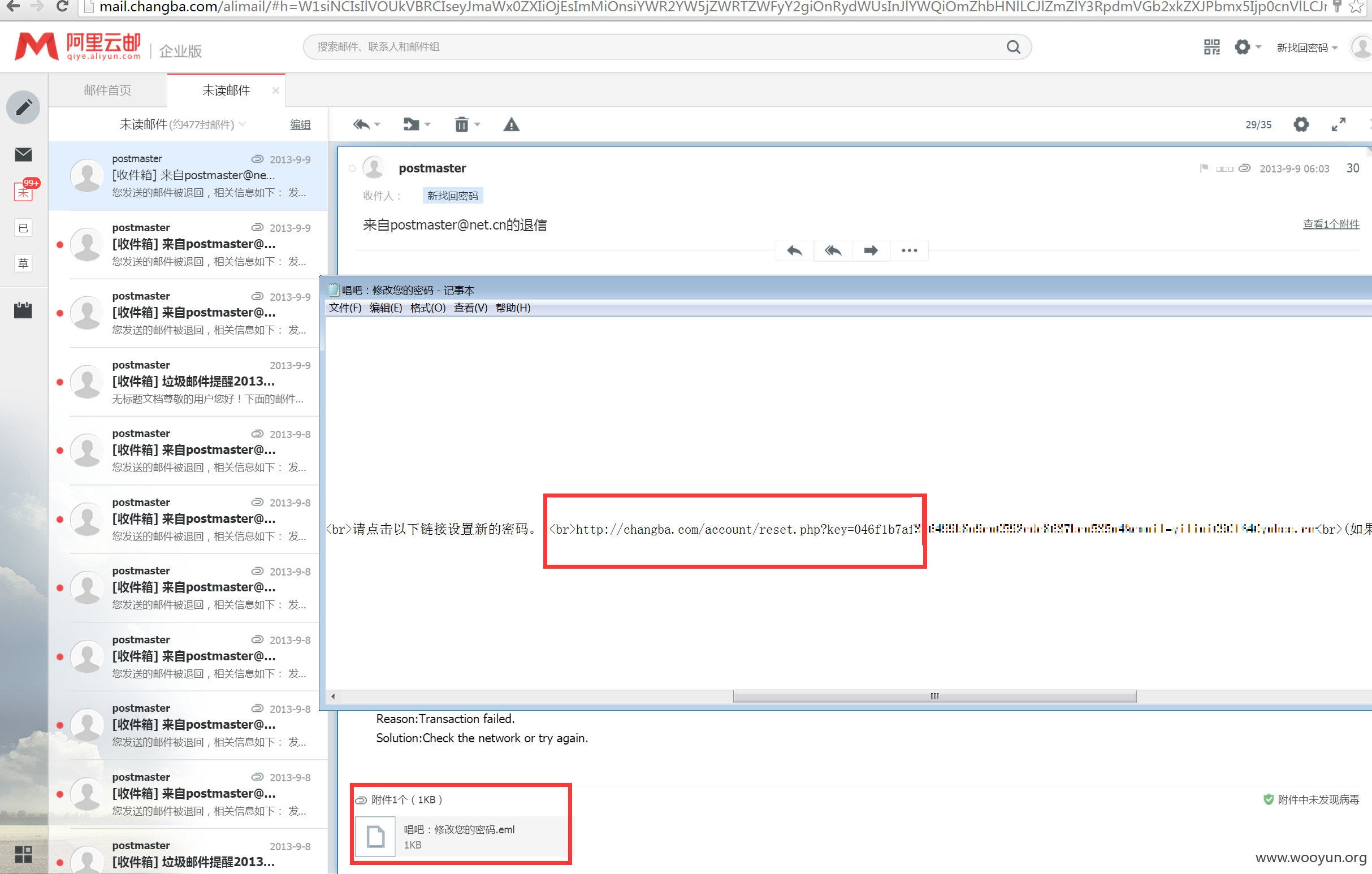
#04 找回密码
泄露[email protected] 5120vluKtr0Pssap
#05 商家支付宝信息泄露
ca证书也在源码中,cacert.pem,只贴部分
GTE CyberTrust Global Root
==========================
-----BEGIN CERTIFICATE-----
MIICWjCCAcMCAgGlMA0GCSqGSIb3DQEBBAUAMHUxCzAJBgNVBAYTAlVTMRgwFgYDVQQKEw9HVEUg
Q29ycG9yYXRpb24xJzAlBgNVBAsTHkdURSBDeWJlclRydXN0IFNvbHV0aW9ucywgSW5jLjEjMCEG
A1UEAxMaR1RFIEN5YmVyVHJ1c3QgR2xvYmFsIFJvb3QwHhcNOTgwODEzMDAyOTAwWhcNMTgwODEz
MjM1OTAwWjB1MQswCQYDVQQGEwJVUzEYMBYGA1UEChMPR1RFIENvcnBvcmF0aW9uMScwJQYDVQQL
Ex5HVEUgQ3liZXJUcnVzdCBTb2x1dGlvbnMsIEluYy4xIzAhBgNVBAMTGkdURSBDeWJlclRydXN0
IEdsb2JhbCBSb290MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCVD6C28FCc6HrHiM3dFw4u
sJTQGz0O9pTAipTHBsiQl8i4ZBp6fmw8U+E3KHNgf7KXUwefU/ltWJTSr41tiGeA5u2ylc9yMcql
HHK6XALnZELn+aks1joNrI1CqiQBOeacPwGFVw1Yh0X404Wqk2kmhXBIgD8SFcd5tB8FLztimQID
AQABMA0GCSqGSIb3DQEBBAUAA4GBAG3rGwnpXtlR22ciYaQqPEh346B8pt5zohQDhT37qw4wxYMW
M4ETCJ57NE7fQMh017l93PR2VX2bY1QY6fDq81yx2YtCHrnAlU66+tXifPVoYb+O7AWXX1uw16OF
NMQkpw0PlZPvy5TYnh+dXIVtx6quTx8itc2VrbqnzPmrC3p/
-----END CERTIFICATE-----
Thawte Server CA
================
-----BEGIN CERTIFICATE-----
MIIDEzCCAnygAwIBAgIBATANBgkqhkiG9w0BAQQFADCBxDELMAkGA1UEBhMCWkExFTATBgNVBAgT
DFdlc3Rlcm4gQ2FwZTESMBAGA1UEBxMJQ2FwZSBUb3duMR0wGwYDVQQKExRUaGF3dGUgQ29uc3Vs
dGluZyBjYzEoMCYGA1UECxMfQ2VydGlmaWNhdGlvbiBTZXJ2aWNlcyBEaXZpc2lvbjEZMBcGA1UE
AxMQVGhhd3RlIFNlcnZlciBDQTEmMCQGCSqGSIb3DQEJARYXc2VydmVyLWNlcnRzQHRoYXd0ZS5j
b20wHhcNOTYwODAxMDAwMDAwWhcNMjAxMjMxMjM1OTU5WjCBxDELMAkGA1UEBhMCWkExFTATBgNV
BAgTDFdlc3Rlcm4gQ2FwZTESMBAGA1UEBxMJQ2FwZSBUb3duMR0wGwYDVQQKExRUaGF3dGUgQ29u
c3VsdGluZyBjYzEoMCYGA1UECxMfQ2VydGlmaWNhdGlvbiBTZXJ2aWNlcyBEaXZpc2lvbjEZMBcG
A1UEAxMQVGhhd3RlIFNlcnZlciBDQTEmMCQGCSqGSIb3DQEJARYXc2VydmVyLWNlcnRzQHRoYXd0
ZS5jb20wgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBANOkUG7I/1Zr5s9dtuoMaHVHoqrC2oQl
/Kj0R1HahbUgdJSGHg91yekIYfUGbTBuFRkC6VLAYttNmZ7iagxEOM3+vuNkCXDF/rFrKbYvScg7
1CcEJRCXL+eQbcAoQpnXTEPew/UhbVSfXcNY4cDk2VuwuNy0e982OsK1ZiIS1ocNAgMBAAGjEzAR
MA8GA1UdEwEB/wQFMAMBAf8wDQYJKoZIhvcNAQEEBQADgYEAB/pMaVz7lcxG7oWDTSEwjsrZqG9J
GubaUeNgcGyEYRGhGshIPllDfU+VPaGLtwtimHp1it2ITk6eQNuozDJ0uW8NxuOzRAvZim+aKZuZ
GCg70eNAKJpaPNW15yAbi8qkq43pUdniTCxZqdq5snUb9kLy78fyGPmJvKP/iiMucEc=
-----END CERTIFICATE-----
#06 流量监控平台
1.http://**.**.**/stats_
*****;$password = &q*****
*****a11c1230e11948913dd02b.png*****
#07 ssh信息泄露
*****9;root',:password => *****
*****cod*****
漏洞证明:
#08 数据库信息
由于都是在内网,所以贴下数据库信息作为证明
*****^心主库数*****
*****039;servername'*****
*****']['p*****
*****'username'*****
*****]['password*****
*****']['p*****
*****'dbname']*****
*****]['charset*****
/*zuitaoktv核心从库地址*/
*****'servername'*****
*****lave'][*****
*****9;]['username*****
*****039;]['passwor*****
*****ve']['p*****
*****]['dbname']*****
*****9;]['charset*****
/*mysql Id生成专用数据库地址*/
*****$config['ZuitaoKtvServer'*****
*****039;] = $config['Zuitao*****
*****039;] = $config['ZuitaoKt*****
*****039;] = $config['ZuitaoKt*****
*****039;] = $config['ZuitaoKt*****
*****]['dbname']*****
*****9;]['charset*****
// ================================
// ====== 地方功能数据库 ===========
// ================================
/*mysql duet 数据库地址*/
*****['servername*****
*****uet']['*****
*****;]['username*****
*****39;]['password*****
*****uet']['*****
*****;]['dbname'*****
*****;]['charset*****
**********
*****从库^*****
*****;]['servername*****
*****slave']['*****
*****#039;]['username*****
*****e']['passw*****
*****slave']['*****
*****39;]['dbname'*****
*****#039;]['charset&*****
**********
*****^^专用^*****
*****39;]['servername*****
*****hottest'][*****
*****#039;]['username&*****
*****t']['passwo*****
*****hottest'][*****
*****#039;]['dbname*****
*****t']['charse*****
**********
**********
*****['servername*****
*****ite']['*****
*****;]['username*****
*****39;]['password*****
*****ite']['*****
*****;]['dbname'*****
*****;]['charset*****
**********
*****]['servername'*****
*****l_read'][*****
*****039;]['username&*****
*****']['passwo*****
*****read']['*****
*****039;]['dbname*****
*****039;]['charset*****
*****'servername'*****
*****Read'][*****
*****9;]['username*****
*****039;]['passwor*****
*****ad']['p*****
*****]['dbname']*****
*****039;charset'] = *****
dbconf=(["host170"]="zuitaoktv"
["host109"]="zuitaoktv"
["host111"]="zuitaoktv"
["host146"]="zuitaoktv"
["host152"]="zuitaoktv"
["host159"]="zuitaoktv"
["host160"]="changba_client"
["host161"]="zuitaoktv"
["host171"]="mall ktvroom"
["host183"]="work_gift gift_sync"
["host189"]="payment"
["host195"]="zuitaoktv"
["host204"]="zuitaoktv duet"
)
*****cnf --host=192.168.1.170 --port=3306*****
*****-host=192.168.1.109 --port=3306 --*****
*****-host=192.168.1.111 --port=3306 --*****
*****-host=192.168.1.152 --port=3306 --*****
*****-host=192.168.1.159 --port=3306 --*****
*****-host=192.168.1.160 --port=3306 --*****
*****-host=192.168.1.161 --port=3306 --*****
*****-host=192.168.1.146 --port=3306 --*****
*****-host=192.168.1.171 --port=3306 --*****
*****-host=192.168.1.183 --port=3306 --*****
*****-host=192.168.1.189 --port=3306 --*****
*****-host=192.168.1.195 --port=3306 --*****
*****-host=192.168.1.204 --port=3306 --*****
***** )*****
*****ode*****
*****^^账*****
*****ervername'] = &*****
*****39;]['por*****
*****39;username']*****
*****assword'] = *****
*****39;]['pco*****
*****#039;dbname'*****
*****#039;charset'*****
*****cod*****
<code>mysql_servers = array(
"192.168.1.76","192.168.1.82",
##快速mysql
'192.168.1.72', '192.168.1.73', '192.168.1.165','192.168.1.31','192.168.1.32','192.168.1.65', '192.168.1.64',/* '192.168.1.63',*/
"192.168.1.110", "192.168.1.111", "192.168.1.113", /*"192.168.1.116",*/"192.168.1.117","192.168.1.27",/* "192.168.1.28",*/
/*"192.168.1.120", "192.168.1.131", */
"192.168.1.130", /*"192.168.1.134",*/ "192.168.1.121", /*"192.168.1.122",*/ /*"192.168.1.123",*/
/*"192.168.1.124",*/ /*"192.168.1.125",*/ /*"192.168.1.135",*/ /* "192.168.1.136", */
/*"192.168.1.138", "192.168.1.139", */
/* "192.168.1.144" , */ "192.168.1.148", /* "192.168.1.149" , */ "192.168.1.150",
"192.168.1.151", "192.168.1.152", "192.168.1.158", "192.168.1.160", "192.168.1.167", "192.168.1.189", "192.168.1.178",
"192.168.1.171", "192.168.1.174", "192.168.1.183", "192.168.1.187", "192.168.1.190","192.168.1.195", "192.168.1.88","192.168.1.91","192.168.1.92",
'192.168.1.145'/*145居然被遗漏了!*/,
/* duet */
/***主库替代为61 "192.168.1.60",**/ "192.168.1.76","192.168.1.61", /* "192.168.1.119", */
/* userwork only*/
"192.168.1.88","192.168.1.89","192.168.1.190",
/* gift */
'192.168.1.62',
/*feed 从库*/
"192.168.1.90", "192.168.1.174", "192.168.1.176",
);
if(date('i')>40){
$mysql_servers = array_merge($mysql_servers,array(
/* ,"192.168.1.129" */ /*,"192.168.1.132" ,*/"192.168.1.141", /*"192.168.1.142", */ "192.168.1.143",
));
}
if(APPLICATION == 'DUET'){
$mysql_servers = array(
"192.168.1.202", /*"192.168.1.203", "192.168.1.204",*/ "192.168.1.205","192.168.1.206","192.168.1.209"
);
}
*****ot;330*****
*****ot;roo*****
*****HtVBpLDPAL*****
*****DA5N2U0MmEK&q*****
修复方案:
svn修补
公网敏感账户定期更改口令
内网账户定期更改口令
版权声明:转载请注明来源 HackBraid@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2015-08-10 12:00
厂商回复:
谢谢指出。
最新状态:
暂无