漏洞概要
关注数(24)
关注此漏洞
漏洞标题:中国玩家网某服务器运帷不当可Getshell进内网
提交时间:2015-08-06 11:33
修复时间:2015-08-11 11:34
公开时间:2015-08-11 11:34
漏洞类型:未授权访问/权限绕过
危害等级:高
自评Rank:20
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
Tags标签:
无
漏洞详情
披露状态:
2015-08-06: 细节已通知厂商并且等待厂商处理中
2015-08-11: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
中国玩家网jenkins未授权访问,getshell进内网
详细说明:
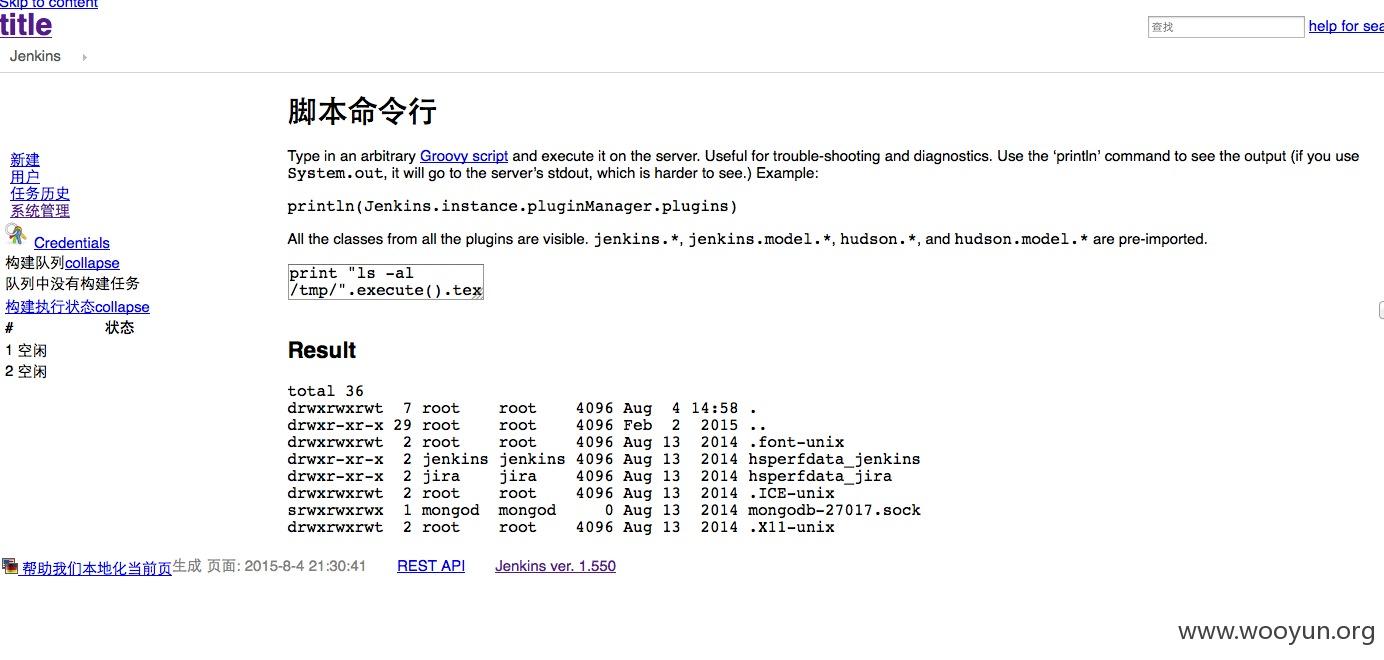
http://180.168.34.2:8080/script
http://www.cwan.com/
虽然jenkins的js丢了,但是命令照样执行
漏洞证明:
你有 777 的目录,我就可以写python脚本,就能写反弹shell了,想想我只是为了刷点wb,赚点奖品,还是算了
没图不完整,so
修复方案:
修改jenkins配置,修改访问控制策略
给我20rank
版权声明:转载请注明来源 new@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2015-08-11 11:34
厂商回复:
漏洞Rank:4 (WooYun评价)
最新状态:
暂无



