漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0131160
漏洞标题:中国科学院某站SQL注入导致众多内部邮箱沦陷(涉及内部专利信息)
相关厂商:中国科学院
漏洞作者: M4sk
提交时间:2015-08-03 09:29
修复时间:2015-09-17 10:06
公开时间:2015-09-17 10:06
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(中国科技网)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-08-03: 细节已通知厂商并且等待厂商处理中
2015-08-03: 厂商已经确认,细节仅向厂商公开
2015-08-13: 细节向核心白帽子及相关领域专家公开
2015-08-23: 细节向普通白帽子公开
2015-09-02: 细节向实习白帽子公开
2015-09-17: 细节向公众公开
简要描述:
RT
详细说明:
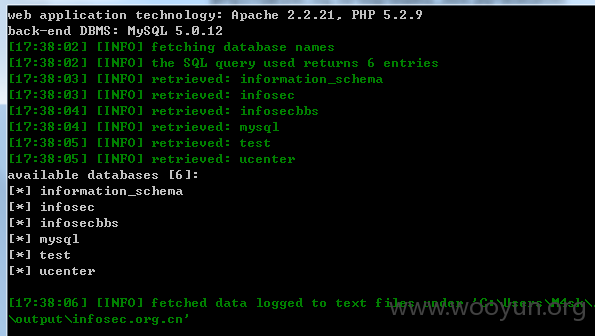
存在sql注入漏洞的一堆 我丢点出来证明下
http://vcc.siat.ac.cn/index/info?title_id=455
http://vcc.siat.ac.cn/index/getInfo?title_id=455
http://vcc.siat.ac.cn/index/info?lan=true&to_path=research&title_id=453
http://vcc.siat.ac.cn/index/info?to_path=research&title_id=453
http://vcc.siat.ac.cn/index/videoList?title_id=453
http://vcc.siat.ac.cn/index/album?title_id=451
http://vcc.siat.ac.cn/index/member?title_id=452&sub_title=460
http://vcc.siat.ac.cn/index/photo?title_id=451&sub_title=459&album_id=102
等等//.....太多 先列举这么多了..
root权限的
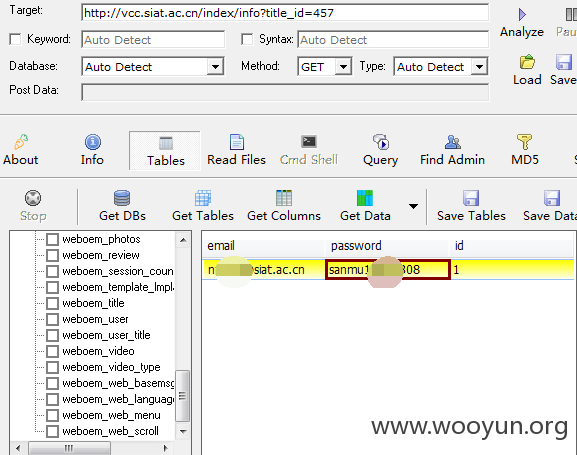
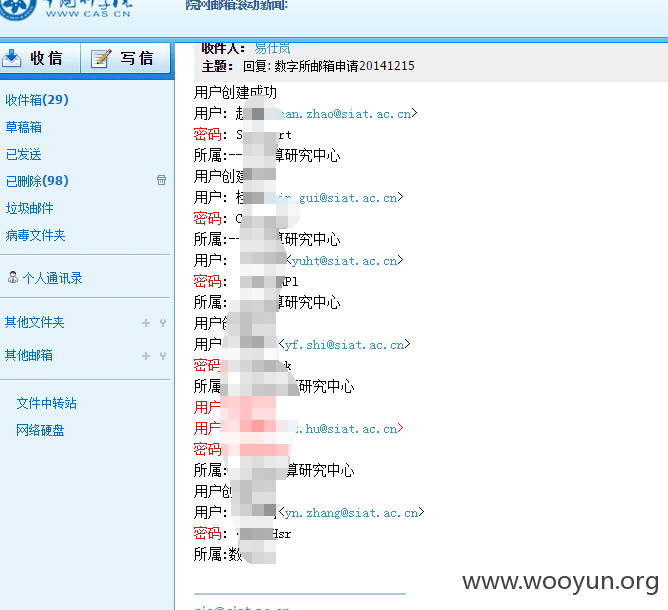
然后注入出 邮箱密码//... [email protected] sanmu198XXXXXX (XXX代表打码的)
然后果断登陆之:https://mail.cstnet.cn 和 http://mailax1.cstnet.cn/
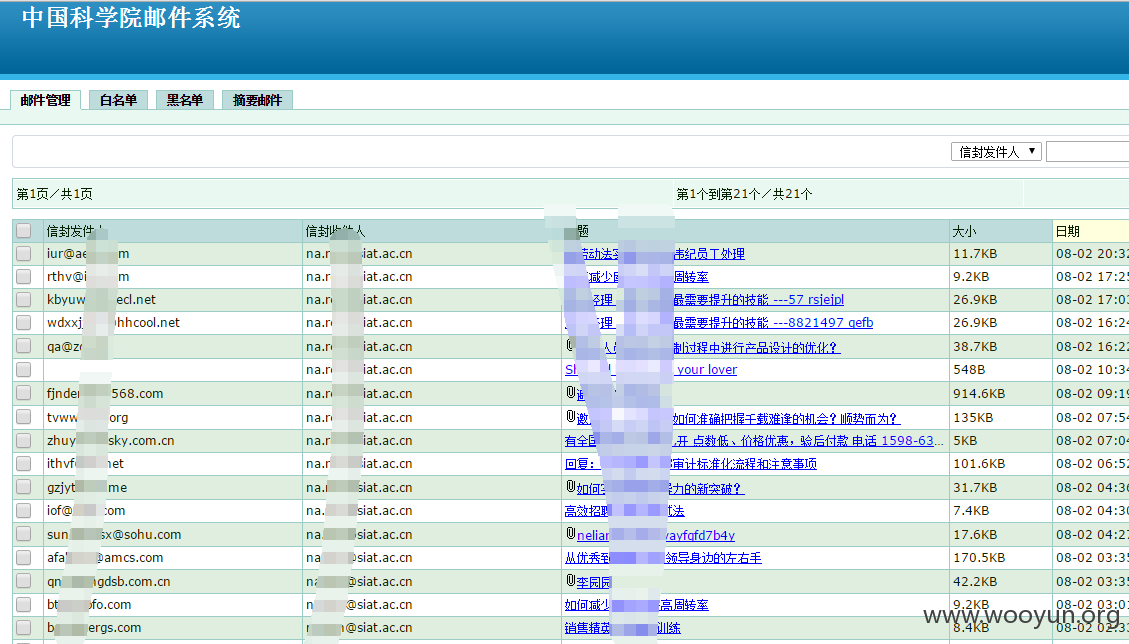
里面还有各种专利信息
当然在里面还泄露了一些内部的邮箱密码
敏感信息没去特意找了 有时候邮箱沦陷比网站沦陷了危害还大...
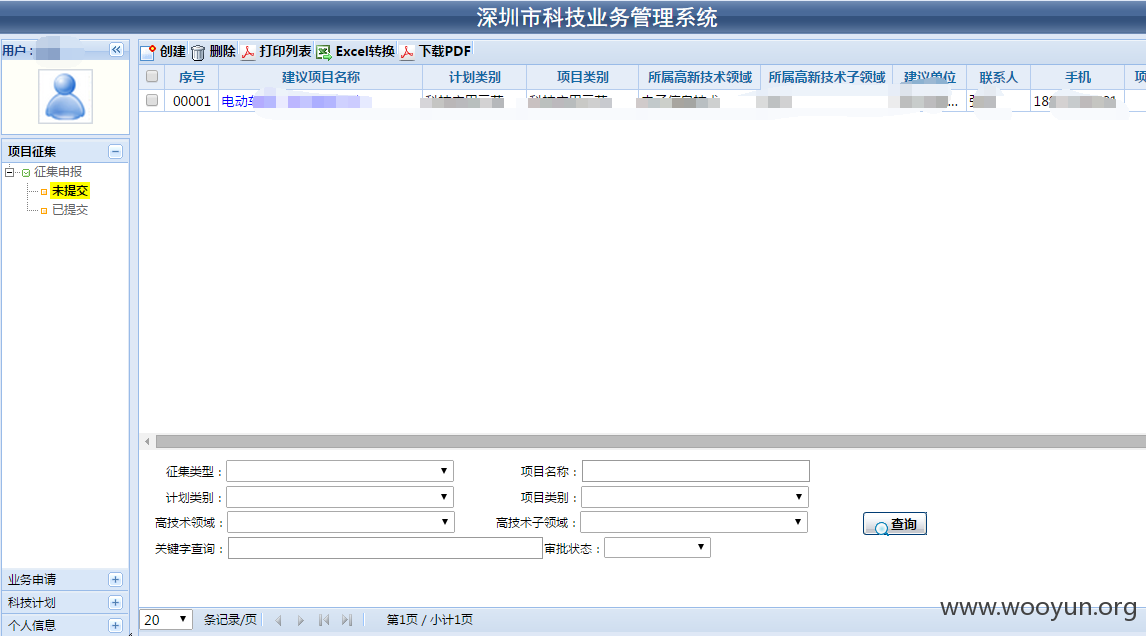
通过一些邮件的密码泄露 我还登陆了一些专利提交的后台
通过注入又泄露了一堆用户名和密码:
当然我们看到邮箱了 可以通过会员密码去撞库内部邮箱的密码~
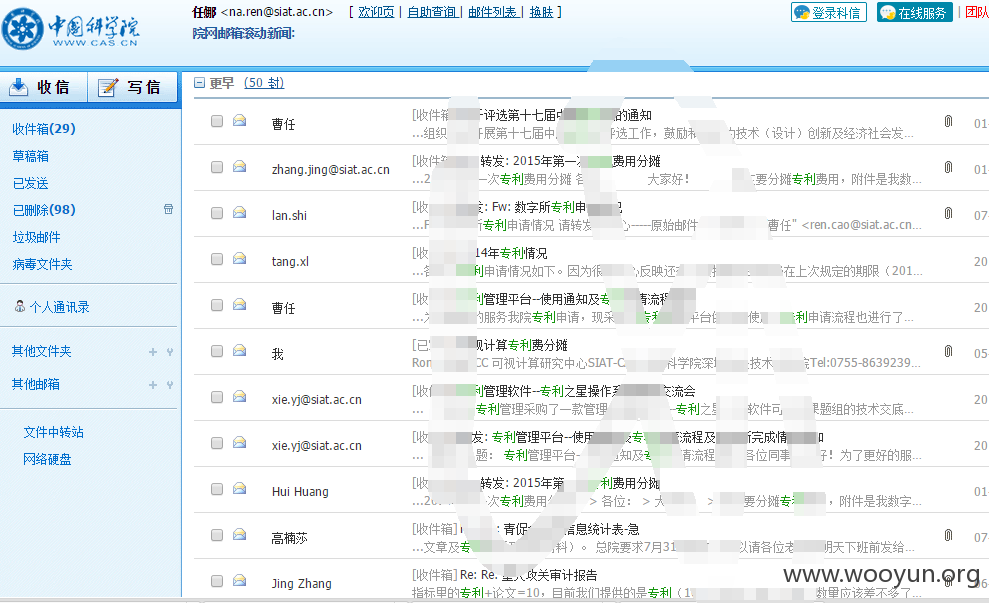
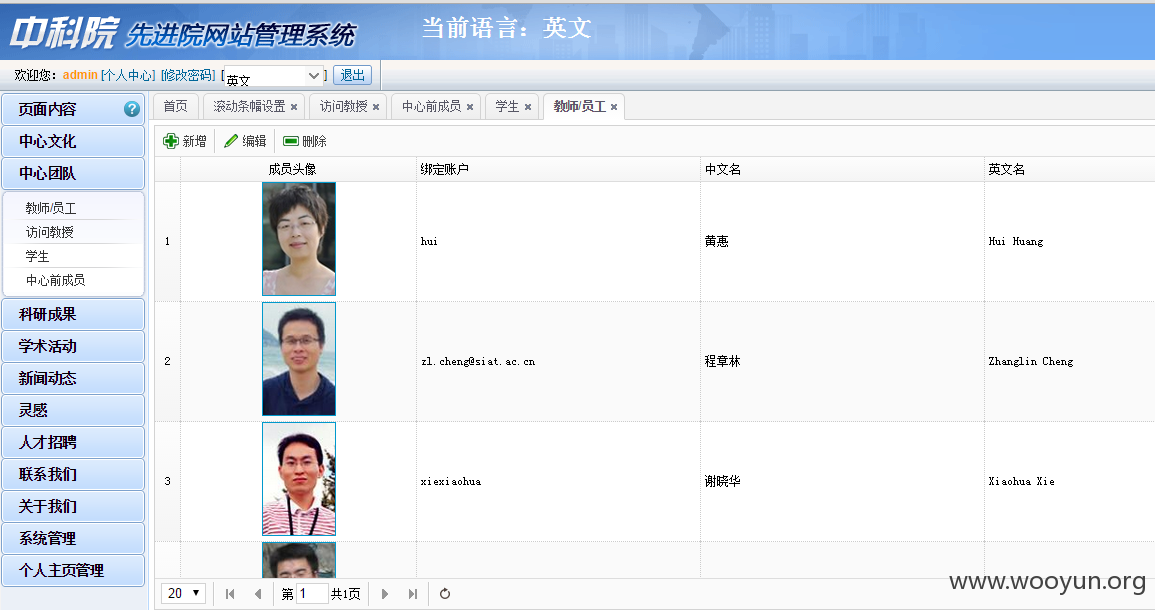
然而我通过这些信息又成功进入了后台
泄露各种人的信息
不深入了~~
漏洞证明:
综上
修复方案:
各种改密码 修注入
版权声明:转载请注明来源 M4sk@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2015-08-03 10:05
厂商回复:
收到
最新状态:
暂无