东风汽车公司始建于1969年,是中国汽车行业的骨干企业。经过三十多年的建设,已陆续建成了十堰(主要以中、重型商用车、零部件、汽车装备事业为主)、襄樊(以轻型商用车、乘用车为主)、武汉(以乘用车为主)、广州(以乘用车为主)等主要生产基地,公司运营中心于2003年9月28日由十堰迁至武汉。主营业务包括全系列商用车、乘用车、汽车零部件和汽车装备。目前,整车业务产品结构基本形成商用车、乘用车各占一半的格局。截至2004年底,公司总资产768.9亿元(RMB),净资产339亿元(RMB),在册员工10.6万人。
东风汽车公司某子站SQL注射(泄露6W多员工姓名、身份证号、公积金余额等)、后台管理员密码密码明文存储;
注入地址: http://www.dfgjj.dfmc.com.cn/ShowNews.aspx?Id=2345 参数:Id
GJJCX 公积金查询表中数据有6万多条
YE:余额 ZH:账号 SFZ:身份证
网站可查询:
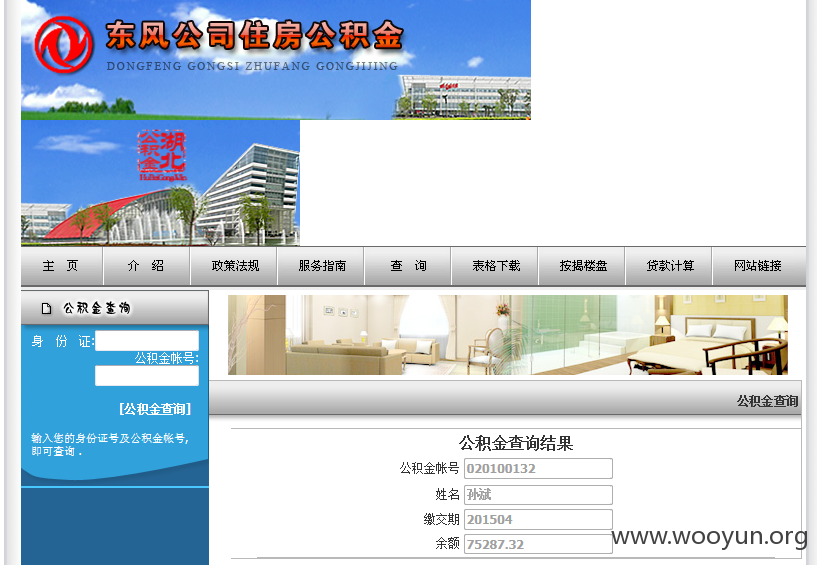
后台管理员密码明文存储
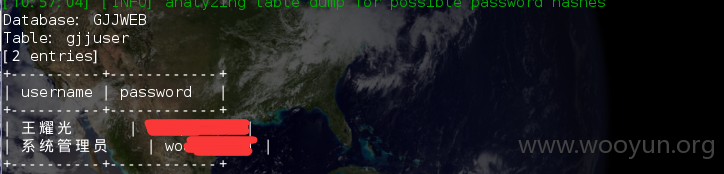
GJJCX 公积金查询表中数据有6万多条
YE:余额 ZH:账号 SFZ:身份证
网站可查询:

后台管理员密码明文存储





