漏洞原理参考DiscuzX任意文件删除漏洞:
————————————————————————————————
通过搜索发现suning.com下存在一个苏宁云台商家社区使用Discuzx2搭建的社区:
http://sopbbs.suning.com
目测这个站点没有及时打补丁,所以攻击者可以利用上面的漏洞可以删除该社区的整站数据,删除data/install.lock文件就可以整站重装
————————————————————————————————
1.先更新个人资料处“店铺”名为:
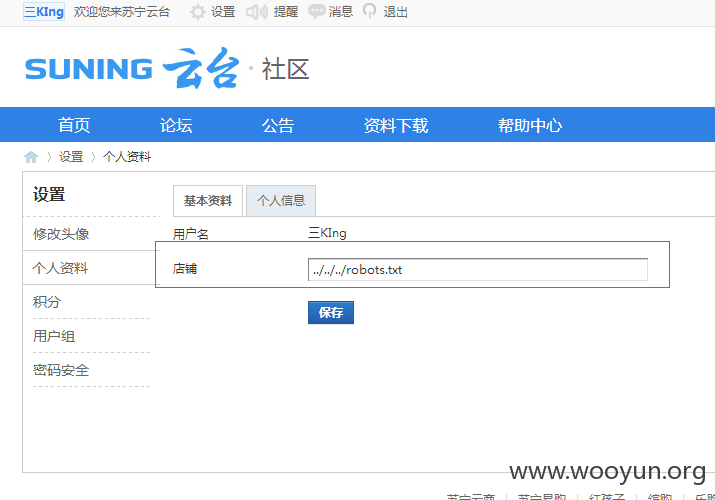
2.提交下面的删除请求:
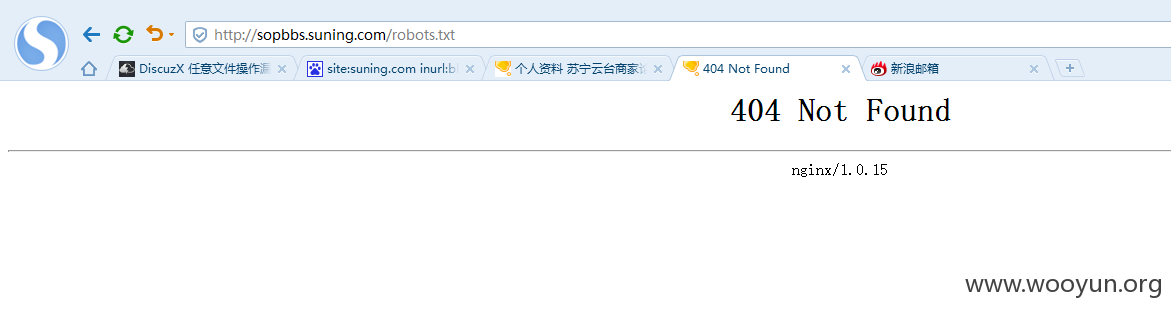
返回查看
发现已经不存在了